Method for evaluating information safety risk based on interval number and ideal solution
A risk assessment and information security technology, applied in the field of information security risk assessment based on interval numbers and ideal solutions, can solve problems such as more professional opinions not being taken seriously, and achieve the effect of reasonable information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] In order to better understand the present invention, the content of the present invention is further illustrated below in conjunction with the examples, but the content of the present invention is not limited to the following examples. Those skilled in the art can make various changes or modifications to the present invention, and these equivalent forms are also within the scope of the claims listed in this application.
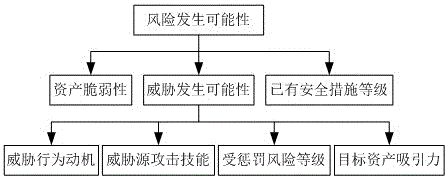
[0043] The present invention adopts a factor layered framework structure, which decomposes each factor affecting information security risk assessment in a more detailed and reasonable manner, and its schematic diagram is as follows figure 1 shown.
[0044] figure 1 The medium risk comprehensive value is an index to measure the security risk level of the information system, which is jointly determined by the possibility of security incidents and the losses caused, and its calculation formula is:
[0045] Risk composite value = R(P, I) (Formula 1)
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com