Scheme for mining abnormal behaviour of industrial internet
An industrial Internet and behavioral technology, applied to electrical components, transmission systems, etc., can solve problems that cannot be prevented in time, and achieve fast calculation speed, high classification accuracy, and good robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
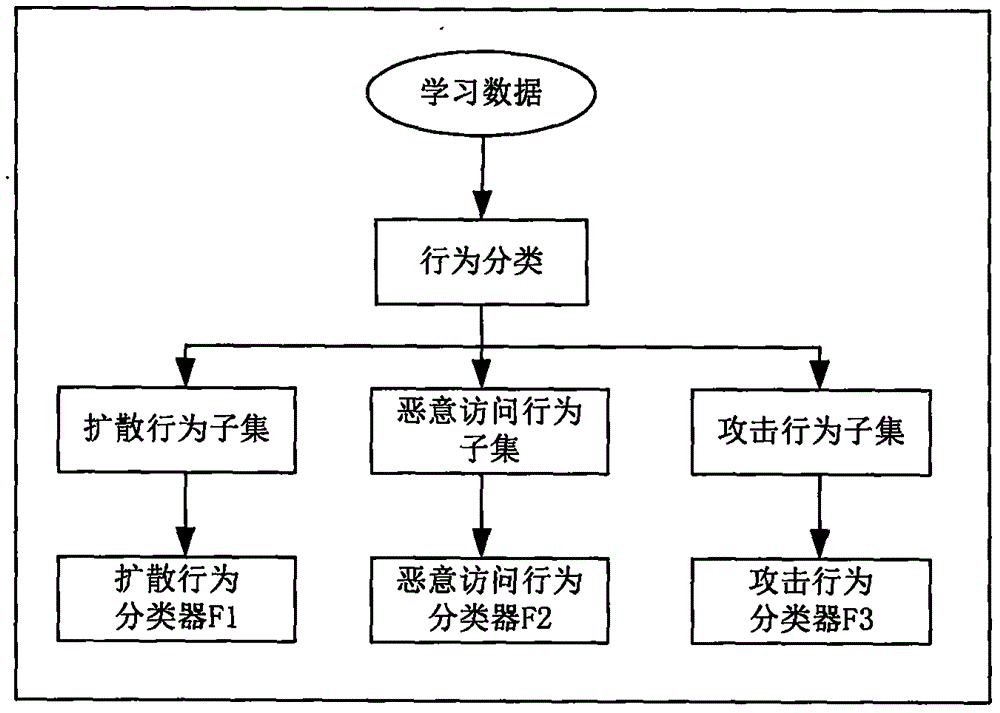
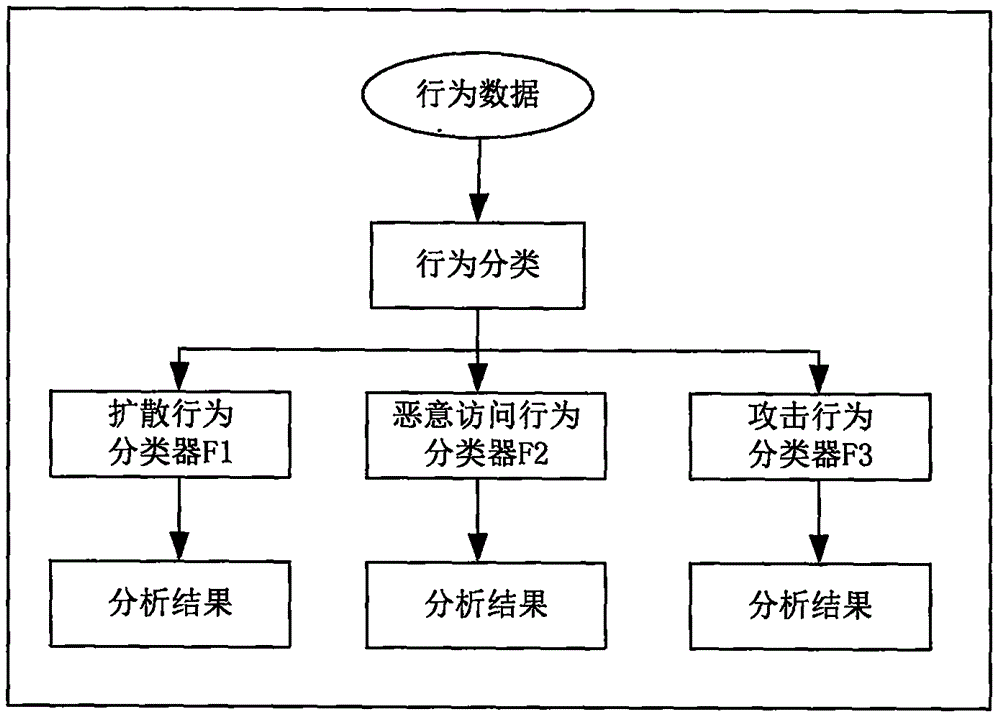
[0019] The behavior of malware in industrial control networks in the mobile Internet environment has different characteristics at each infection stage, so the classification of its behavior helps to improve the accuracy of monitoring. Abnormal behaviors of mobile terminals in industrial control networks in the mobile Internet environment may include:
[0020] ·Attacks on mobile industrial control systems by malicious programs such as mobile terminal zombies, Trojan horses and viruses, and artificial attacks on mobile industrial control systems. These malicious attacks have the characteristics of great harm and heavy losses. Attackers can control the core operation of the mobile industrial control system through malicious instructions, or maliciously download confidential information in the industrial control system.
[0021] ·Infected terminals spread malicious codes to other terminals in various ways. Due to the strong communication capabilities of mobile terminals, infecte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com