Bypass distinguisher method and system based on class separability criteria
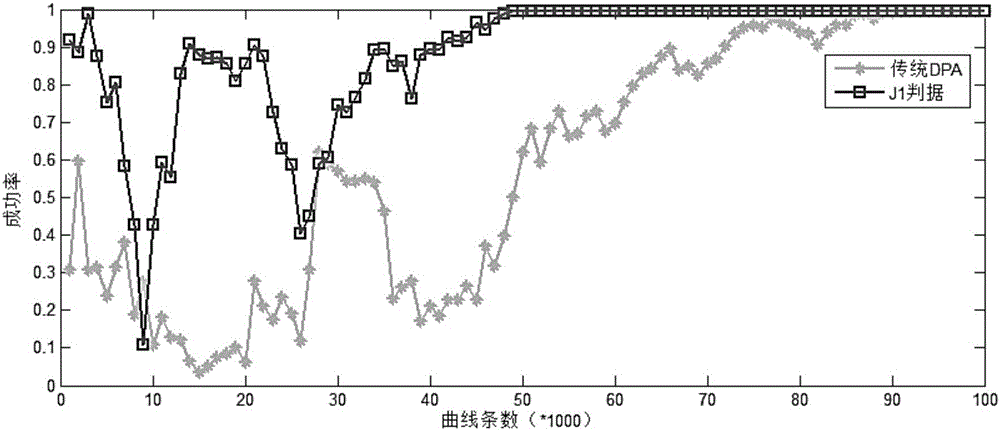
A bypass and criterion technology, applied in the field of computer security, can solve the problem of single use of information in the DPA discrimination method, and achieve the effect of improving analysis efficiency and large separability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
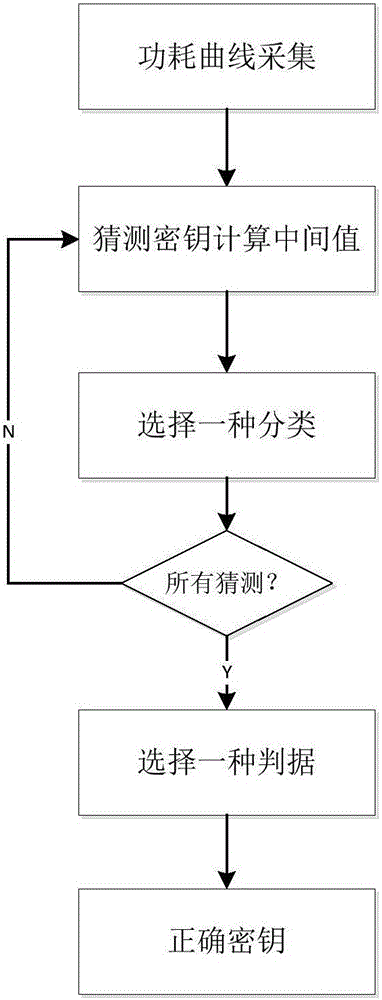
[0026] This embodiment relates to a bit-based general differential power consumption analysis method, which is described by taking AES hardware implementation as an example: for hardware-implemented AES, the analysis can be expressed as a function: I=f(k,m). Due to the existence of key confusion, the intermediate value in the register of each round is related to the current 8-bit round key, and its 16-byte S boxes are executed in parallel and overlapped on the power consumption curve. This invisibly reduces the signal-to-noise ratio and increases the number of curves required for the attack. To carry out ordinary DPA attacks, a large number of power consumption curves must be collected at the same time, occupying a large storage space and computing power.
[0027] This embodiment includes the following steps:
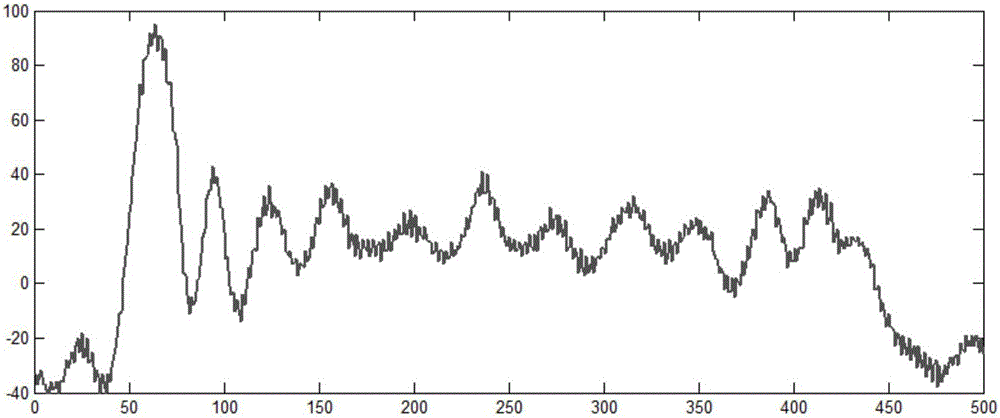
[0028] ①Randomly input the plaintext m, execute the target function f cyclically, and collect the power consumption curve, such as figure 2 shown;
[0029] ②Accordin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com