Unlocking method, unlocking device and unlocking system of access control lock
An access control lock and unlock technology, which is applied in the direction of instruments, time registers, single input port/output port registers, etc., can solve the problems of poor user experience, low experience of opening and unlocking, and single unlocking method, achieving The effect of enhancing experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
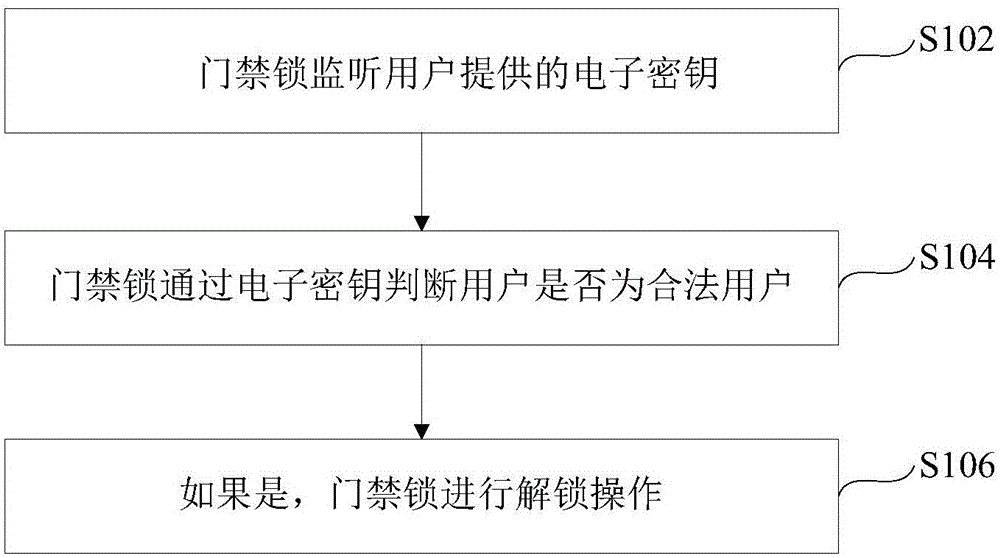
[0031] see figure 1 The flow chart of an unlocking method for an access control lock is shown. The method is described from the side of the access control lock as an example, and includes the following steps:
[0032] Step S102, the access control lock monitors the electronic key provided by the user; the electronic key includes a variety of the following information: the code pattern information of the user terminal collected by the image collector configured by the access control lock, the card reader configured by the access control lock The access control card information collected, and the Bluetooth unlocking information of the user terminal collected through the Bluetooth device configured by the access control lock; wherein, the code type information includes: barcode, two-dimensional code, three-dimensional code or four-dimensional code, etc.; specifically, whether it is Any form of electronic key carries the identity information of the user, thus ensuring the uniquene...
Embodiment 2
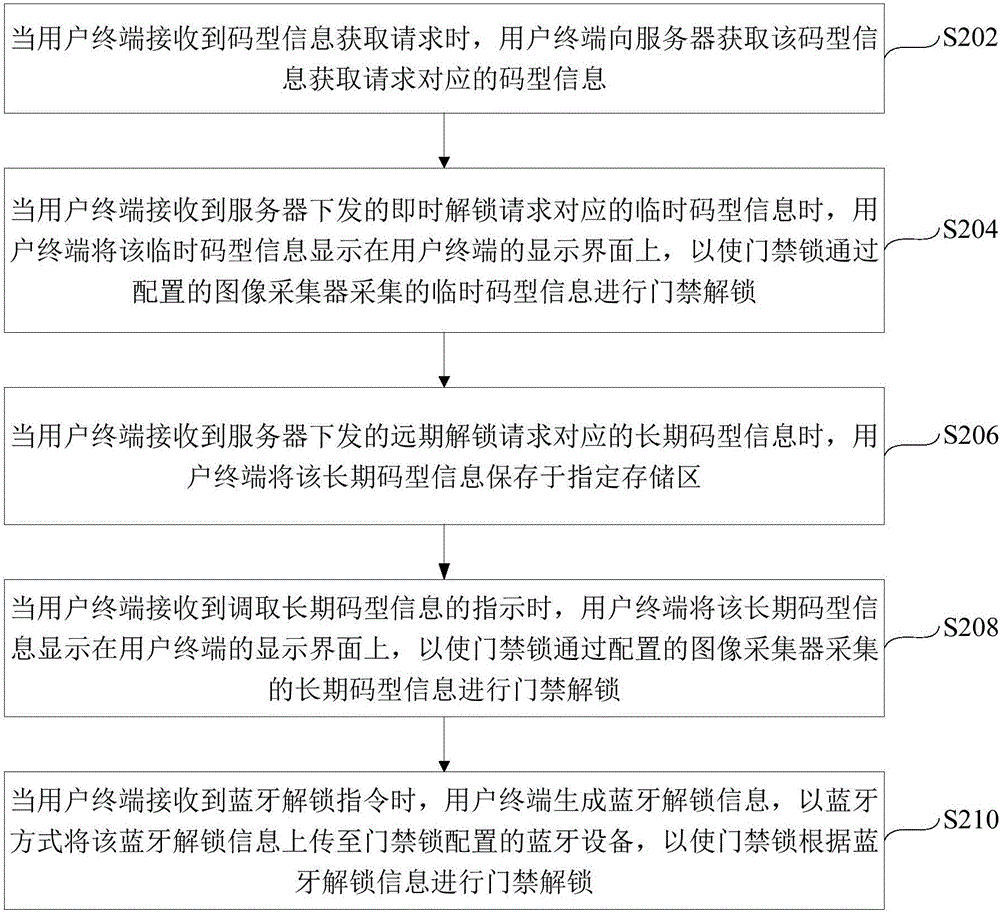
[0049] see figure 2 A flow chart of an unlocking method for an access control lock is shown. The method is described from the user terminal side as an example, and includes the following steps:
[0050] Step S202, when the user terminal receives the code pattern information acquisition request, the user terminal obtains the code pattern information corresponding to the code pattern information acquisition request from the server; wherein, the code pattern information acquisition request includes an immediate unlock request and a long-term unlock request ;The code type information above includes: barcode, two-dimensional code, three-dimensional code or four-dimensional code; specifically, the instant unlock request indicates that a temporary code type needs to be received, and the validity period of the temporary code type is dynamically and periodically set by the server, such as the temporary code The code pattern is valid within 30 minutes. After this time period, the code ...
Embodiment 3
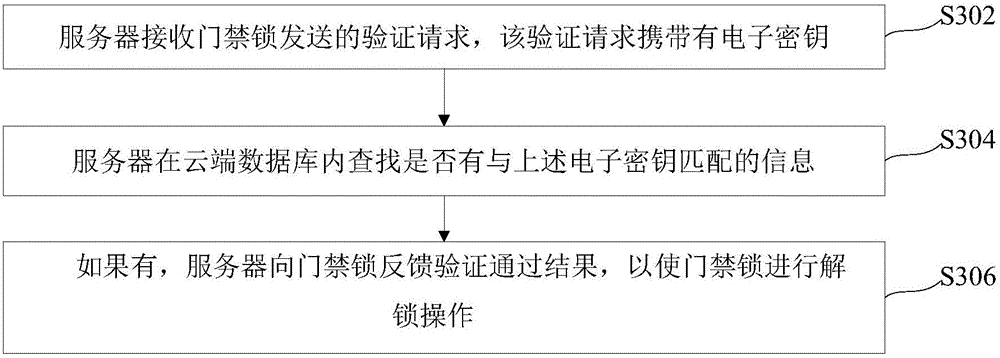
[0057] see image 3 A flow chart of an unlocking method for an access control lock is shown. The method is described by taking the description from the server side as an example, and includes the following steps:
[0058] Step S302, the server receives the verification request sent by the access control lock, and the verification request carries an electronic key; the electronic key includes a variety of the following information: the code pattern information of the user terminal collected by the image collector configured with the access control lock, The access control card information collected through the card reader configured with the access control lock, and the Bluetooth unlocking information of the user terminal collected through the Bluetooth device configured with the access control lock; wherein, the code type information includes: barcode, two-dimensional code, three-dimensional code or four-dimensional code;
[0059] Step S304, the above-mentioned server searches...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com