Network flooding attack detection, storage and display system and method
A flood attack and display system technology, applied in transmission systems, electrical components, etc., can solve the problems of no records, network managers do not have records, etc., to achieve the effect of convenient management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
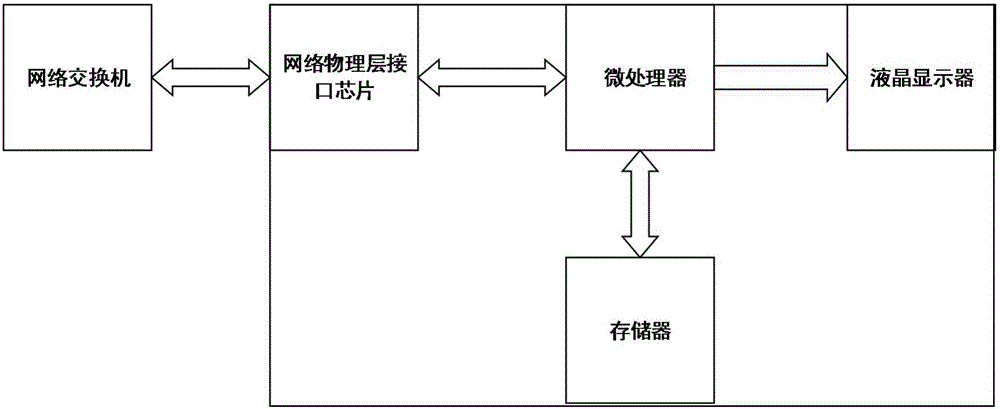
[0011] Embodiment 1: A system for detecting, storing and displaying network flood attacks. The involved hardware device consists of the following parts: a network physical layer interface chip, a microprocessor, a memory, and a liquid crystal display. The system is connected to a network port of a network switch through a network cable.
[0012] In LAN communication, the Address Resolution Protocol (ARP, Address Resolution Protocol) is often used to obtain the MAC address through the IP address. When a computer A in the local area network needs to obtain its MAC address through the IP address of the destination computer B, this computer A broadcasts an ARP request message containing the IP address of the destination computer B to all computers in the LAN. Computer B will return the MAC address information to determine the MAC address of the target computer B; after receiving the returned message, computer A will store the IP address and MAC address in the local ARP cache and k...
Embodiment 2
[0026] Embodiment 2: A detection, storage and display system of a network flood attack, mainly composed of a network physical layer interface chip, a microprocessor, a memory, and a liquid crystal display, and the detection system is connected to a network port of a switch through a network cable above, used to receive all ARP request frames in the local area network; the microprocessor classifies the received ARP request frames according to the source MAC address, and the microprocessor records the receiving time of the frame and judges the multi-frame ARP Whether the characteristics of the request frame conform to the characteristics of a flood attack, when it is determined that the characteristics belong to the characteristics of a flood attack, the microprocessor records the receiving time of the frame and the MAC address of the source host, stores them in the memory, and saves the data in the memory ARP flooding information is output on the LCD display.
[0027] The featu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com