IP-MAC real-name binding based network access control system and control method
An IP-MAC and network access technology, applied in the field of network access control systems based on IP-MAC real-name binding, can solve the problem of not realizing the network real-name binding of terminal computer equipment, unable to control the permissions of different resources, and having no terminals Access to intranet control and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
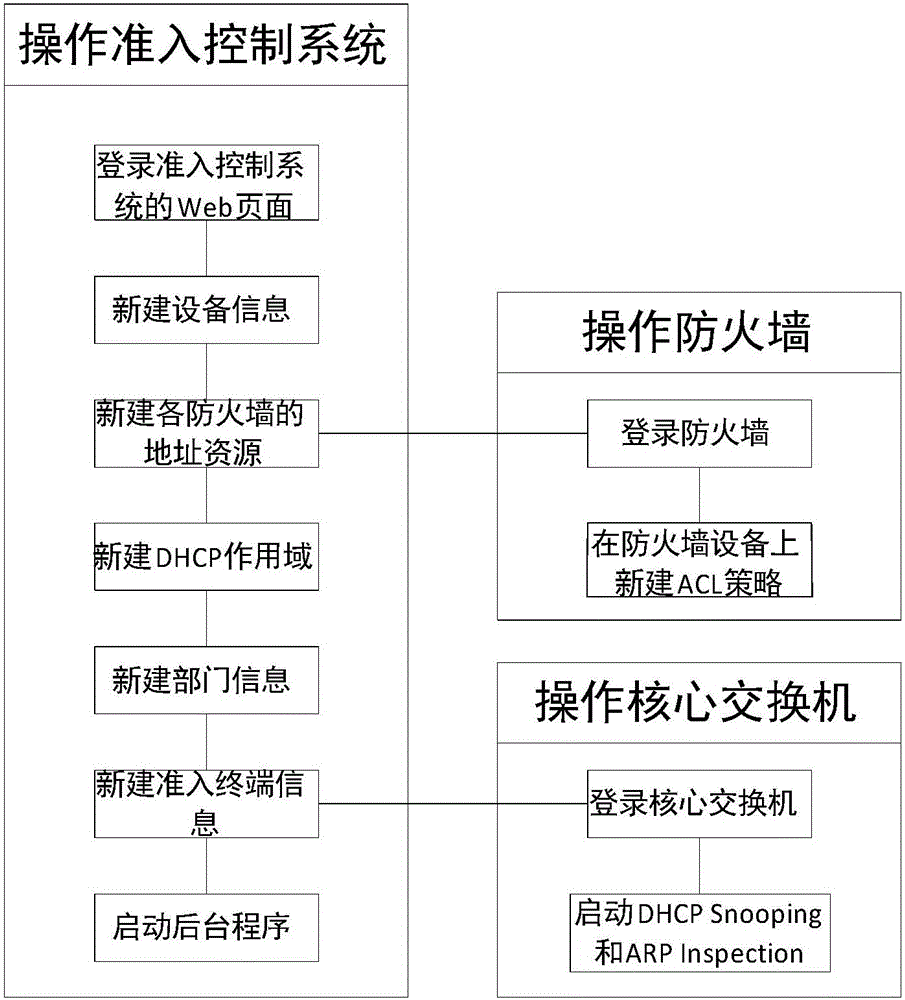
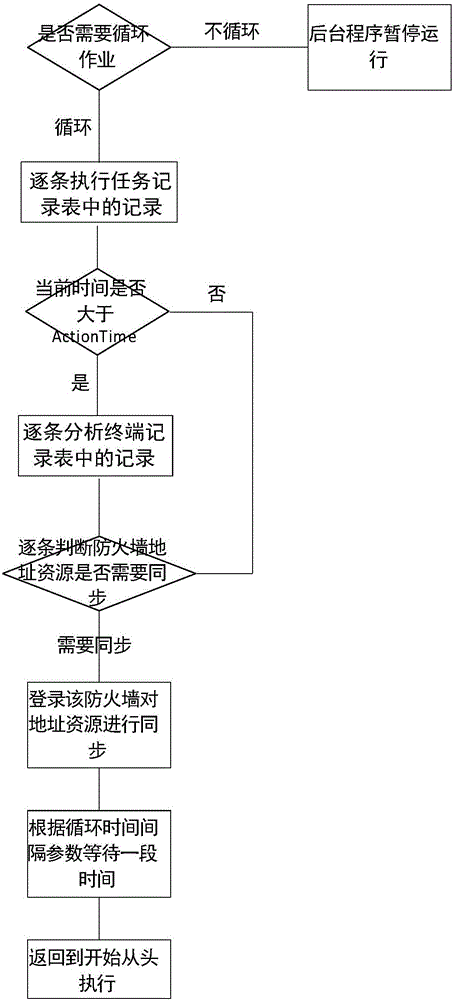
[0073] Embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
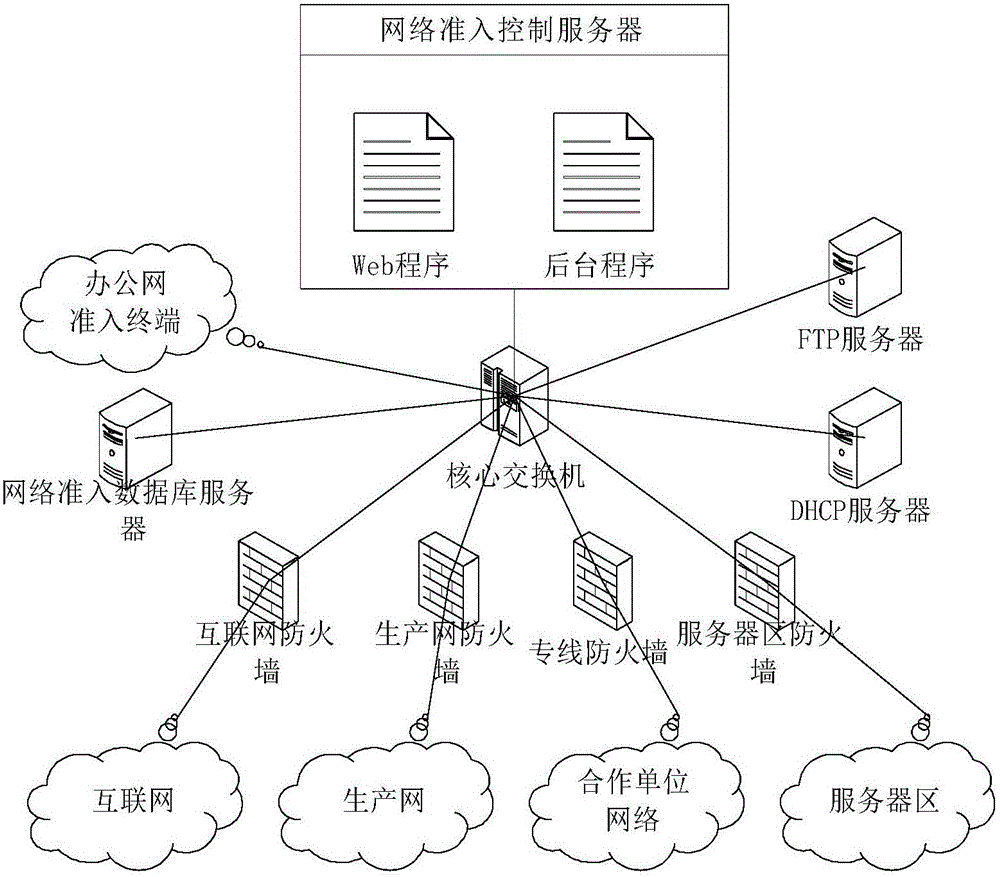
[0074] A network access control system based on IP-MAC real-name binding, such as figure 1 As shown, it includes core switches, DHCP servers, FTP servers, network access database servers, network access control servers, and office network access terminals. The core switch adopts a three-layer switch, which is the gateway of each vlan in the LAN. In the present invention, the core switch uses the DHCPSnooping function and the ARPInspection function to realize the shielding of counterfeit DHCP servers and the shielding of manually configured IP addresses. The DHCP server is directly connected to the core switch or is not directly connected to the same Layer 2 switch as the terminal subject to admission control, and is used for issuing IP addresses and binding IP-MAC. The FTP server and the core switch can access each other on the network, which is used...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com