Identity authentication method, identity authentication device, and server
An identity authentication, the same location technology, applied in user identity/authority verification, key distribution, can solve problems such as system or user loss, inability to guarantee sensitive data and operational security, lack of
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
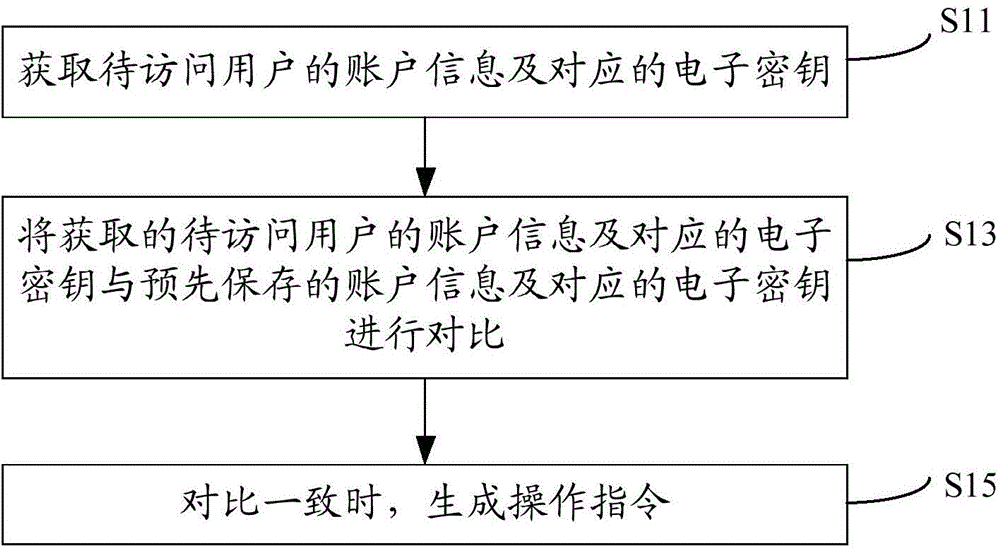
[0077] According to an aspect of the embodiments of the present invention, an identity authentication method is provided. In this method, firstly, the account information of the user to be accessed and the corresponding electronic key are obtained; then, the account information of the user to be accessed and the corresponding electronic key are acquired. The electronic key is compared with the pre-saved account information and the corresponding electronic key; finally, when the comparison is consistent, an operation instruction is generated.
[0078] like figure 1 As shown, the method includes:
[0079] Step S11, acquiring the account information of the user to be accessed and the corresponding electronic key.
[0080] Among them, the account information includes: account number, user name, account password, key password and account application time. Of course, it can be understood that in the identity authentication method of the embodiment of the present invention, the spe...
Embodiment 2
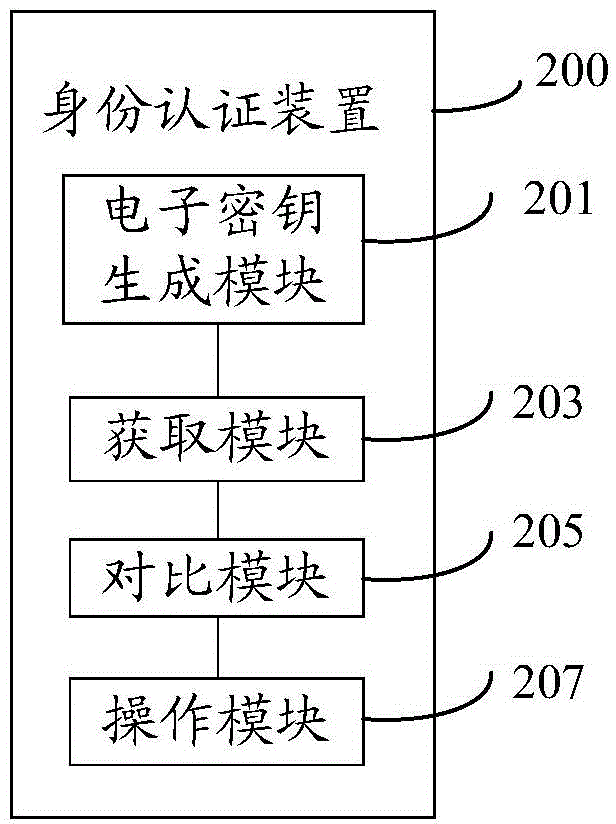
[0145] According to another aspect of the embodiments of the present invention, an identity authentication device is also provided, such as figure 2 As shown, the device 200 includes:
[0146] An acquisition module 203, configured to acquire the account information of the user to be accessed and the corresponding electronic key;
[0147] A comparison module 205, configured to compare the acquired account information and corresponding electronic key of the user to be accessed with the pre-saved account information and corresponding electronic key;
[0148] The operation module 207 is configured to generate an operation instruction when the comparison is consistent.
[0149] Optionally, the account information includes: account number, user name, account password, key password and account application time.
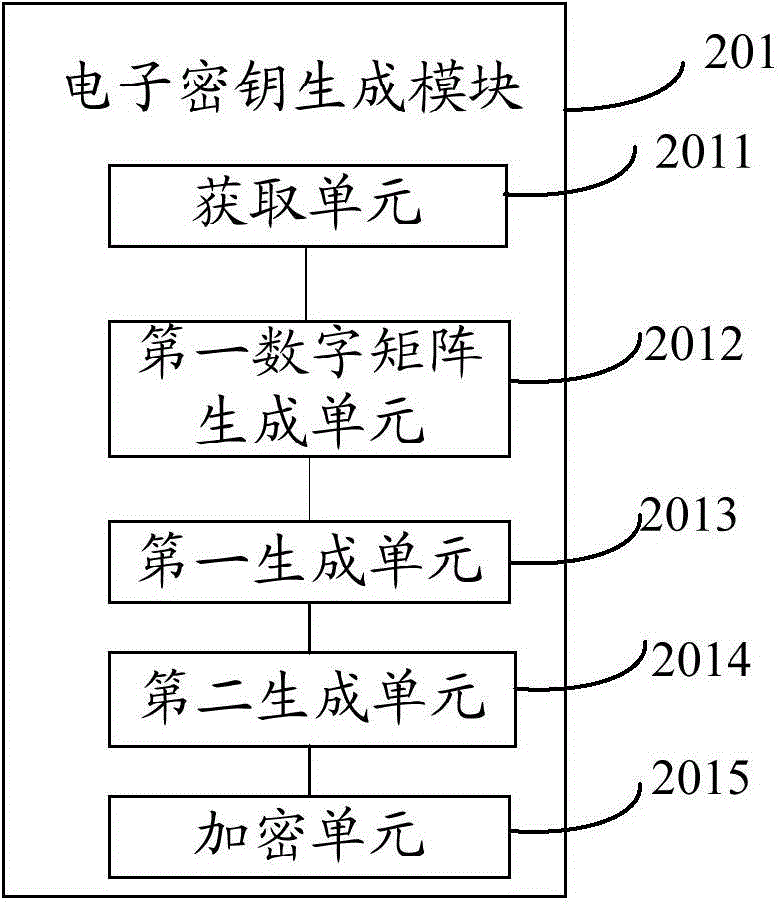
[0150] Optionally, the corresponding electronic key is generated according to the account password and key password.
[0151] Optionally, the device 200 also includes: ...
Embodiment 3
[0198] According to another aspect of the embodiments of the present invention, there is also provided a server, which includes a database, and also includes the above-mentioned identity authentication device.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com