Multilevel locking and multilevel unlocking method for mobile device
A mobile device unlocking technology, applied in the direction of instruments, electronic digital data processing, digital data authentication, etc., can solve the problems of multi-level locking and unlocking that are not applicable to mobile devices, and achieve the effect of protecting data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
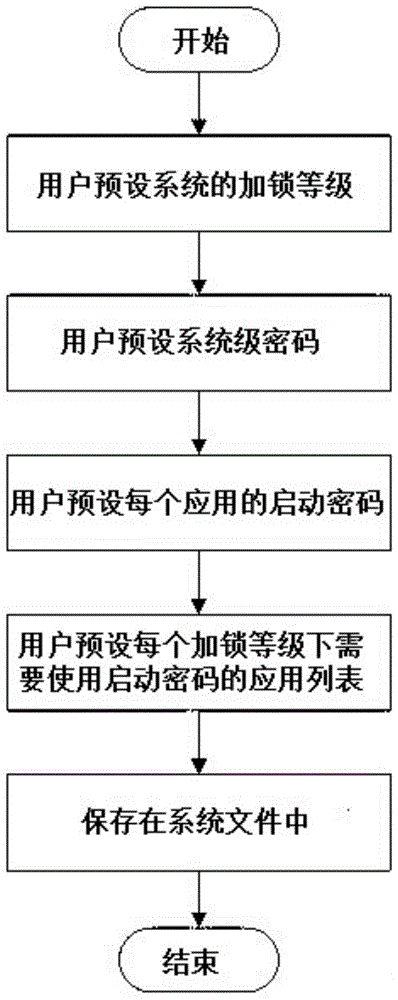
[0024] A method for multi-level locking and multi-level unlocking for mobile devices, the specific steps comprising:
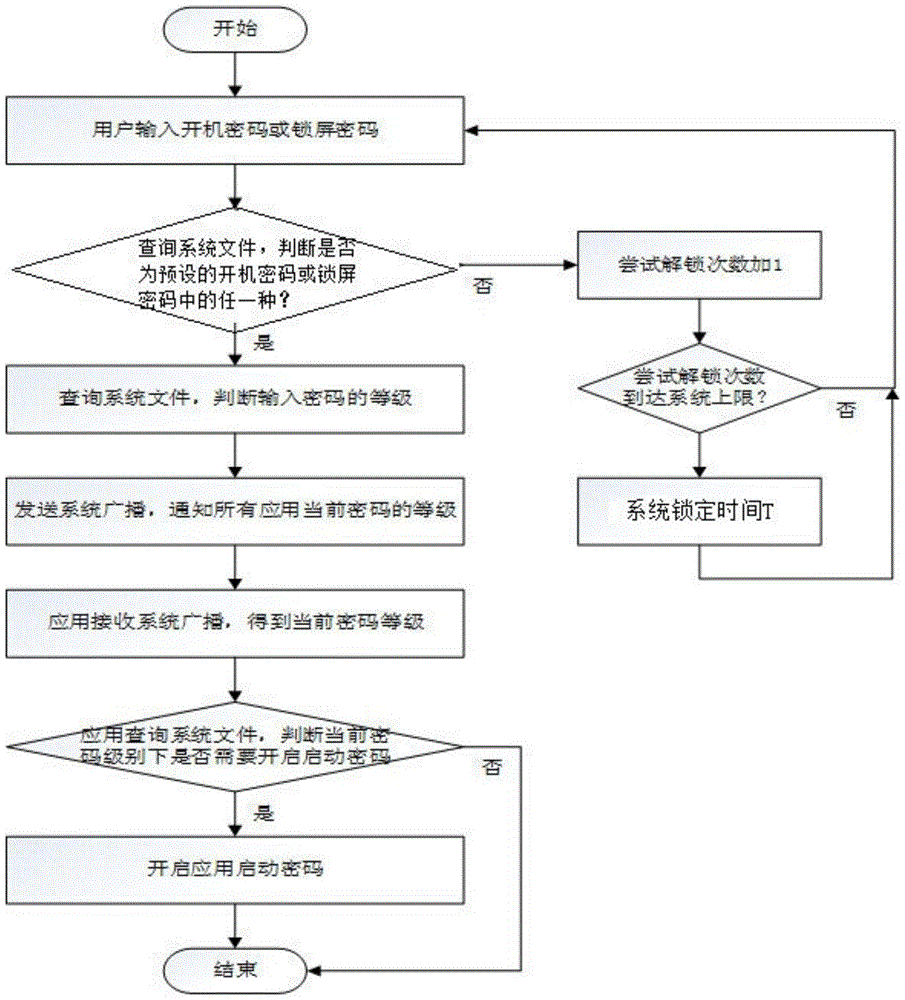
[0025] (1) Multi-level locking: In the system settings of the mobile device, a module for user-preset locking methods is reserved. Users can preset the system's locking level, system-level password, startup password of each application and The list of applications that need to use the startup password under each locking level is stored in the system file. Different locking levels correspond to different system-level passwords and the list of applications that need to use the startup password; where the system-level password includes the startup password and Screen lock password, power-on password refers to the password that the user needs to enter when turning on or restarting the mobile device; lock screen password refers to the password that the user needs to enter when unlocking the screen of the mobile device; the system of the mobile device automatically s...
Embodiment 2
[0034] According to a method for multi-level locking and multi-level unlocking of mobile devices described in Embodiment 1, the difference is that in step (1), the locking levels of the system include primary locking, secondary locking, Three-level lock and four-level lock. When the first level is locked, when the user enters the power-on password or lock screen password to enter the system, all applications on the mobile device do not need to use the startup password, so that all applications can be accessed and viewed at any time. All materials; when the second level is locked, when the user enters the power-on password or lock screen password, some applications on the mobile device need to use the startup password and some applications do not need to use the startup password, which can protect the data of more private applications; the third level of encryption When locked, when the user enters the power-on password or lock screen password, all applications on the mobile dev...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com