Software update device, and software update program
A software update device and software technology, applied in software deployment, secure communication devices, computer security devices, etc., can solve problems such as illegal copying of embedded devices, bypassing security functions, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
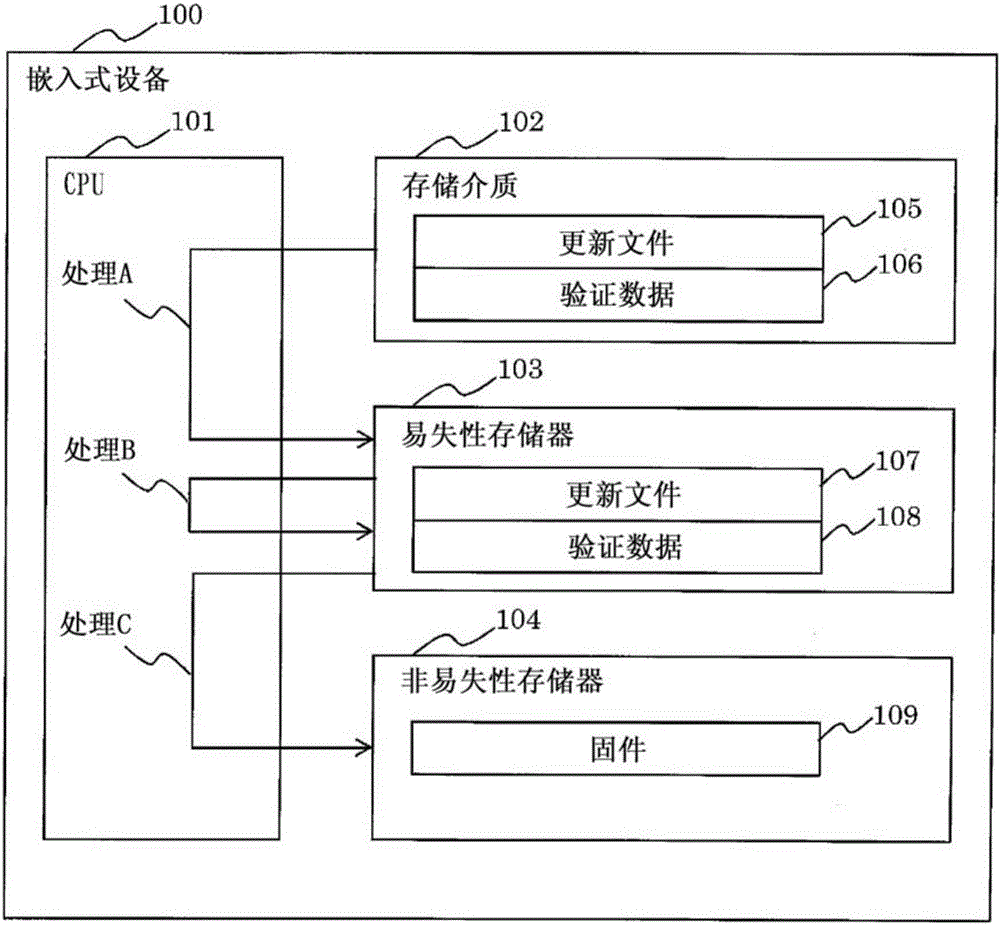
[0041] figure 1 is a hardware configuration diagram of the embedded device 100 (software update device).
[0042] The embedded device 100 includes a CPU 101 , a storage medium 102 , a volatile memory 103 , and a nonvolatile memory 104 .
[0043] The end user supplies the update file 105 (update data) to the embedded device 100 via the storage medium 102 . The embedded device 100 uses the update file 105 stored in the storage medium 102 to update the firmware 109 in the non-volatile memory 104 .
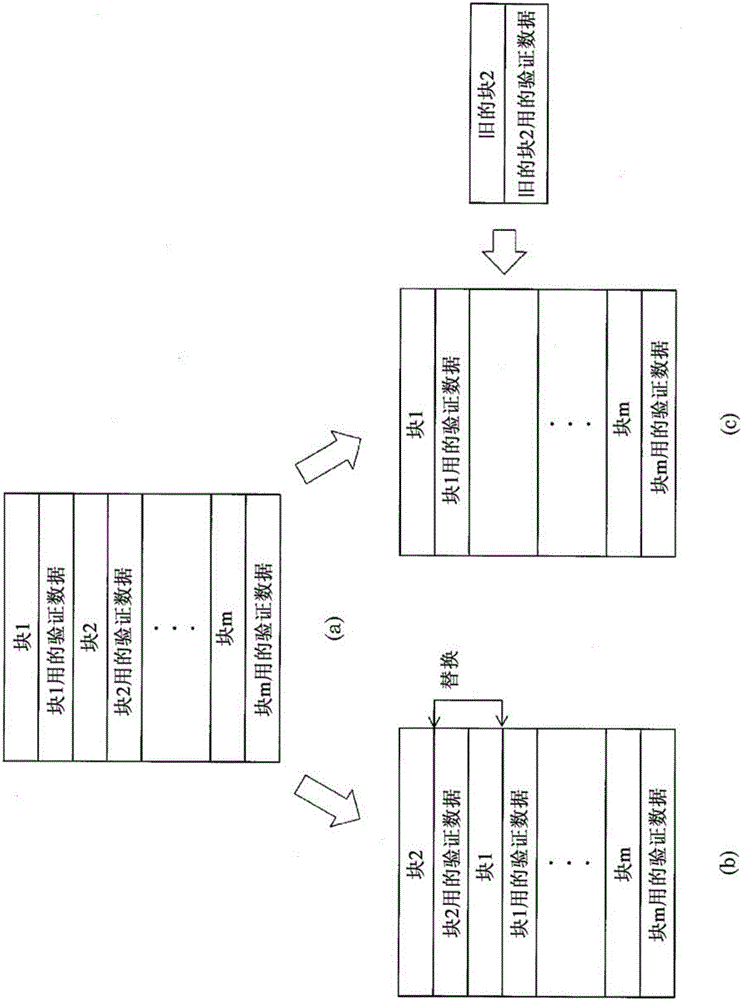
[0044] In the case of applying tamper detection technology to the protection of firmware, the end user supplies the embedded device 100 with verification data 106 for detecting tampering of the update file 105 together with the update file 105 .
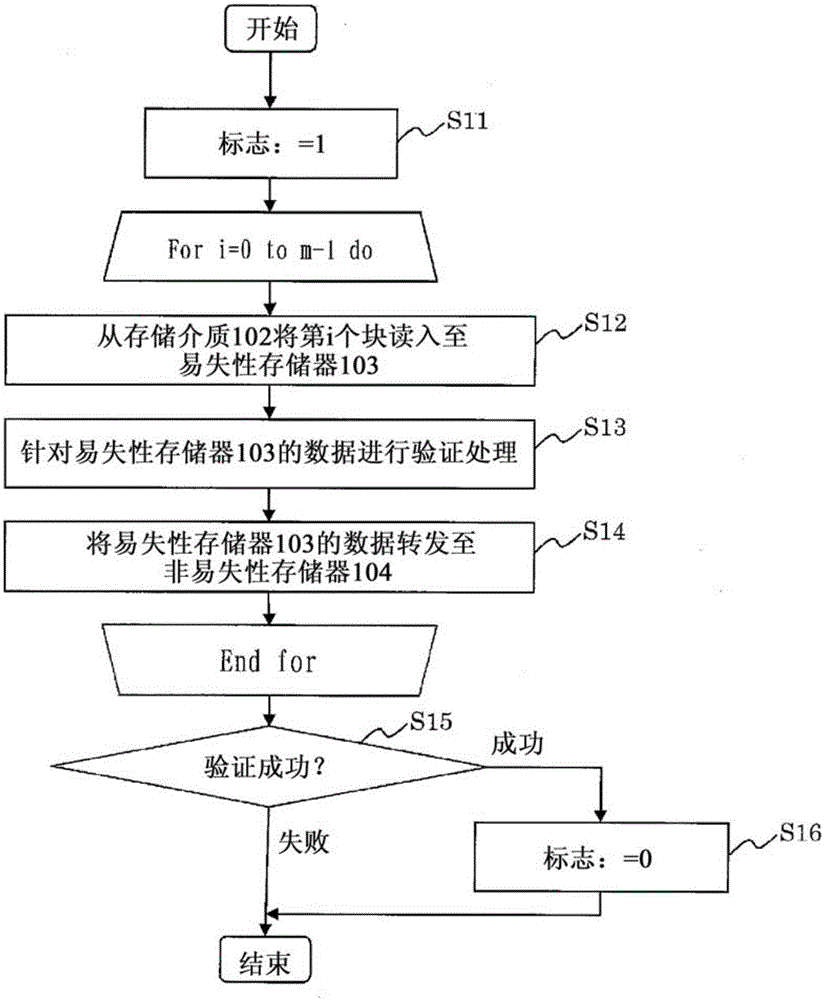
[0045] When updating the firmware 109, the CPU 101 performs the following processing.
[0046] First, CPU 101 executes process A to copy update file 105 and verification data 106 existing in storage medium 102 to volatile memory 103 . Th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com