Method for user identity authentication in authentication service cloud
A user identity authentication and authentication service cloud technology, applied in the authentication service cloud for the user identity authentication field, can solve the problems of service interruption, unfavorable resource elastic deployment, safe and reliable operation, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0013] The content of the present invention is described in more detail below:
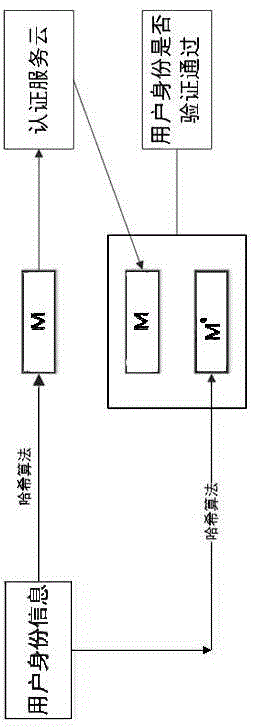
[0014] Before the user uses cloud computing-related applications and services for the first time, user identity information is entered, such as: user identity information M is stored in the authentication service cloud, and before the user accesses cloud computing-related applications and services, the application and service prompts the user Enter the relevant identity information, the application and service will send the user's identity information M' to the authentication service cloud, and the authentication service cloud will complete the comparison with the user's identity information M stored in its own database. If M=M', it will be considered that the user has provided identity information If it is consistent with the storage in the database, the authentication is passed; otherwise, the relevant identity information is deemed to be different, and the authentication fails.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com