End system-based safety improving method of network data
A network data and end system technology, applied in the field of network data security improvement, can solve problems such as inability to verify correctness, and achieve the effect of being flexible, easy to implement, and ensuring correctness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
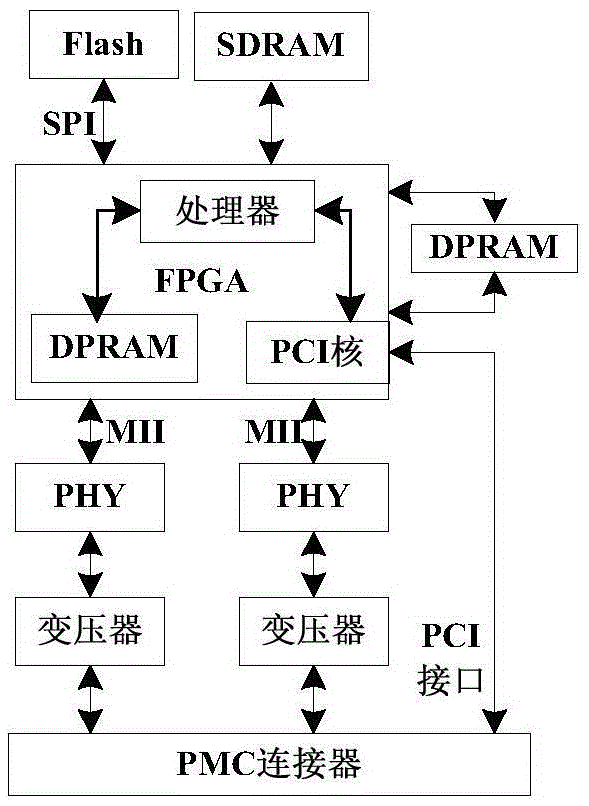
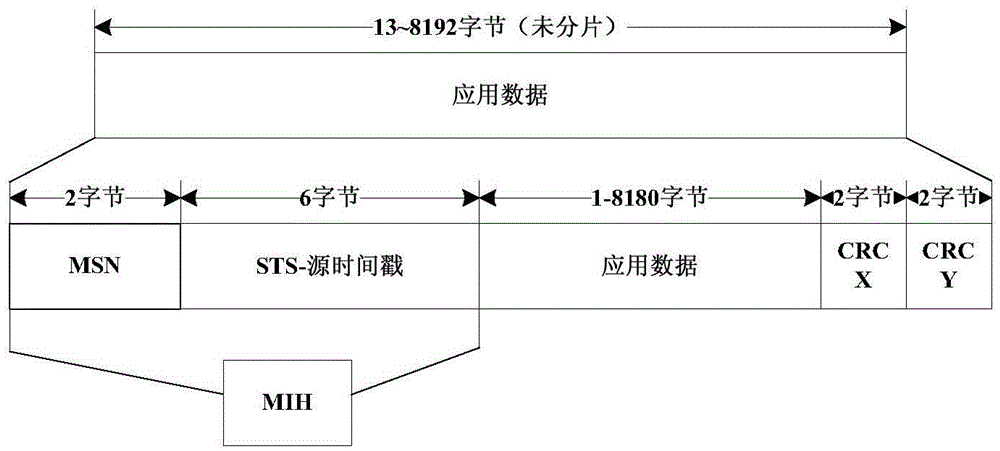
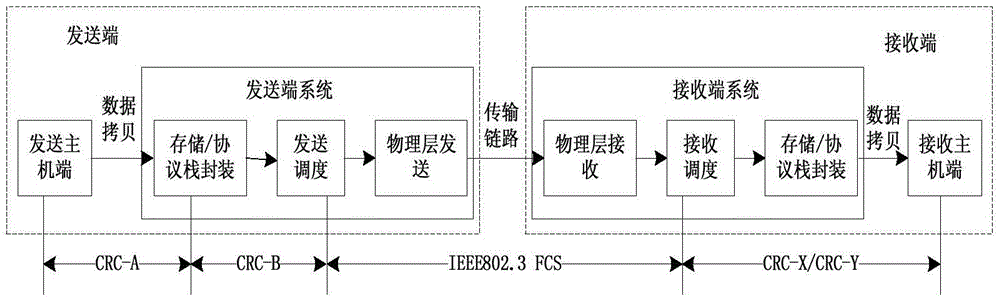
[0027] The present invention proposes a method for improving network data security based on an end system, such as figure 1 As shown, including FPGA internal integrated processor core, externally mounted SDRAM and DPRAM dual-port chips, SDRAM is used as a buffer for the application data of the communication port, used to buffer the sending data of the host end and the receiving data of the end system, and the DPRAM dual-port As the sending buffer of the link layer of the end system; by increasing the data copy CRC and the internal data format between the host and the end system to improve data security indicators. Application data format such as figure 2 As shown, for the standard A664 network, the longest application data is 8192 bytes. In order to increase data security, the integrity message header MIH field and two 16-bit CRC fields are added to the application data; the MIH field is composed of It consists of 2-byte message sequence number MSN and 6-byte source time sta...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com