Image Security Transmission Method Based on Fountain Code and Adaptive Resource Allocation
A technology for resource allocation and secure transmission, applied in the direction of link quality-based transmission modification, transmission system, digital transmission system, etc. The effect of reducing transmission delay, low complexity and improving transmission efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
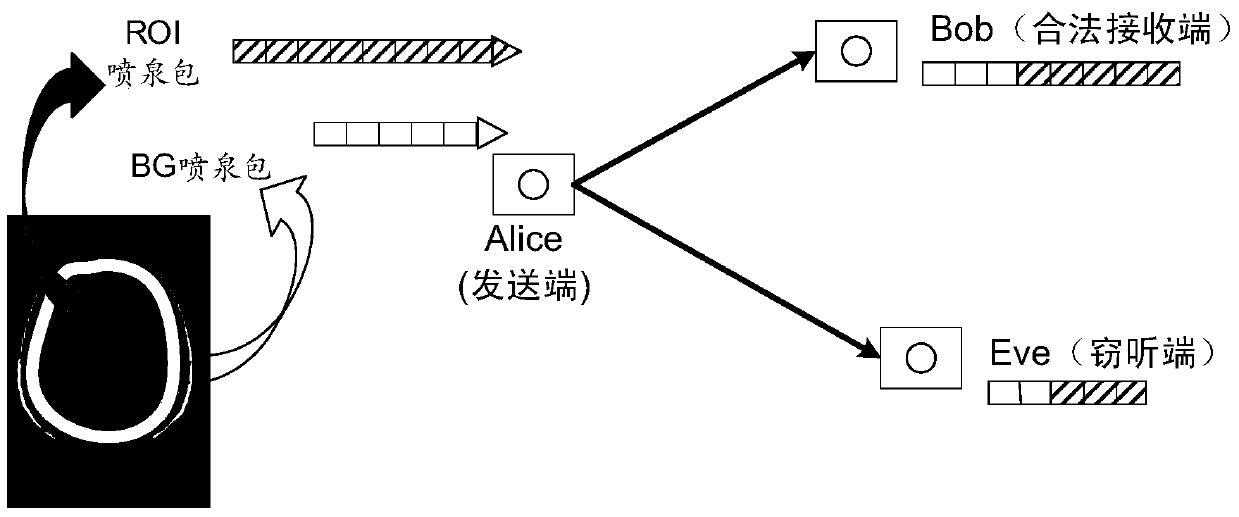
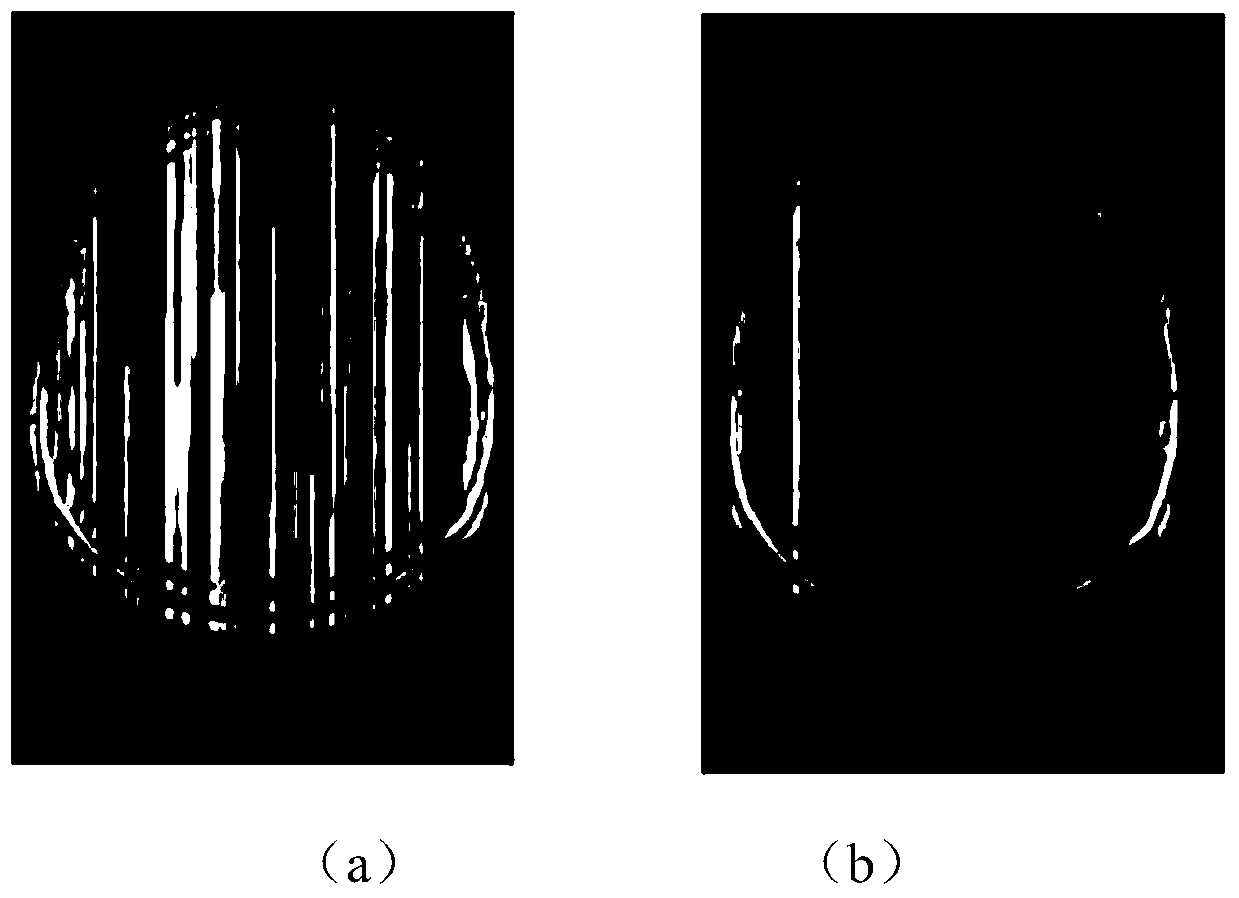
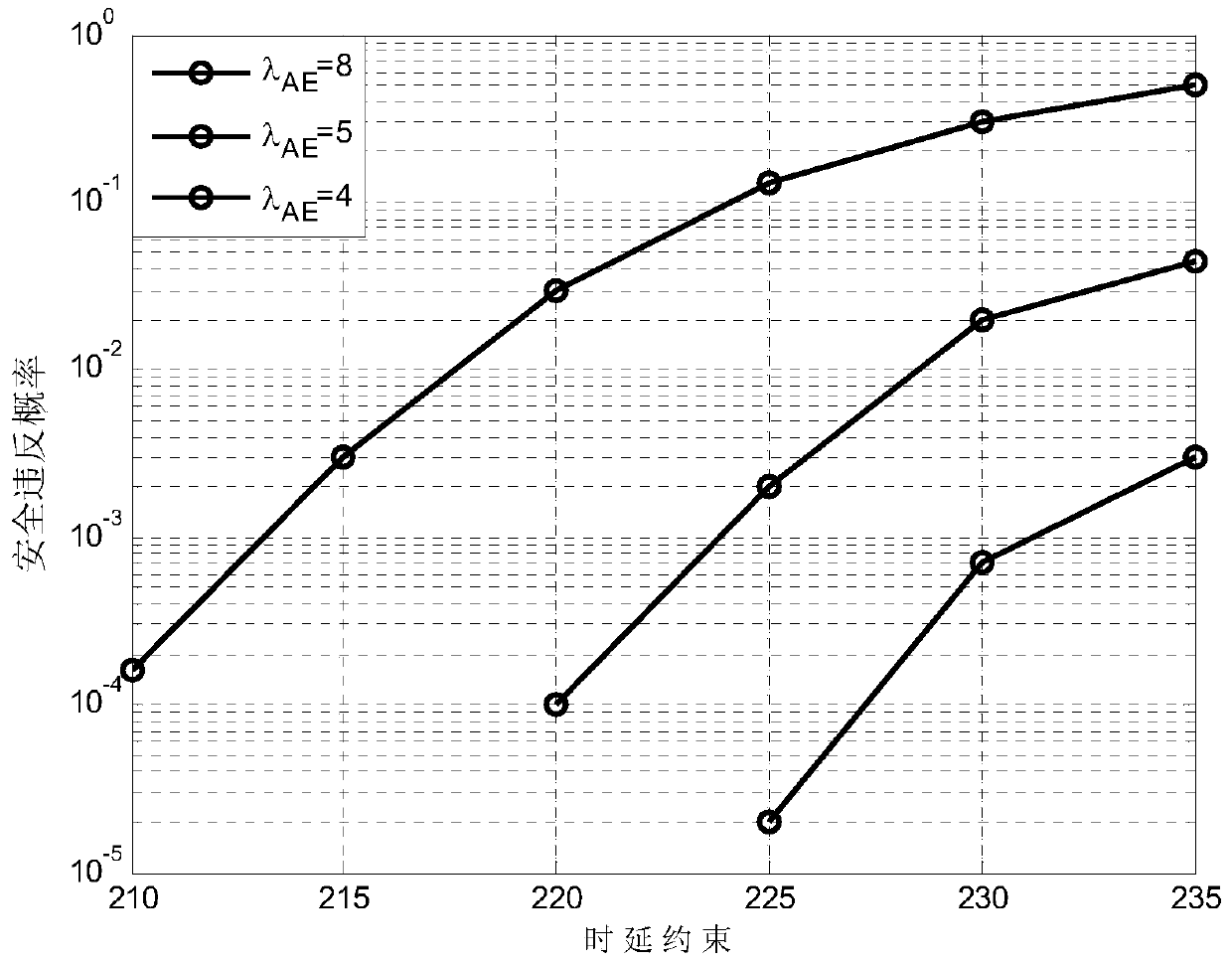
[0052] In this embodiment, the human brain MRI image with a resolution of 352×512 is selected as the private image to be transmitted. Each pixel is represented by 8-bit binary. The original image is divided into 191 ROI original packets and 35 BG original packets. packs, each containing 410 symbols. Considering different delay constraints, the simulation verifies the effectiveness of the present invention. figure 2 is the image actually received by the legal receiving end Bob (the right of the figure) and the eavesdropping end Eve (the left of the figure) when using the method of the present invention to transmit under the given delay constraint T=210, where the white dots are because the present invention will The pixels corresponding to the missing packets are set to 255. From figure 2 It can be seen that the effect of the image received by the legitimate receiving end Bob is obviously better than that of the eavesdropping end Eve. image 3 is the security violation pro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com