Door control method, terminal, server and access control system
An access control and server technology, which is applied in the field of terminals, servers, access control systems, and access control methods, can solve problems such as low control efficiency and slow speed of opening the access control system, and achieve the effect of improving control efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
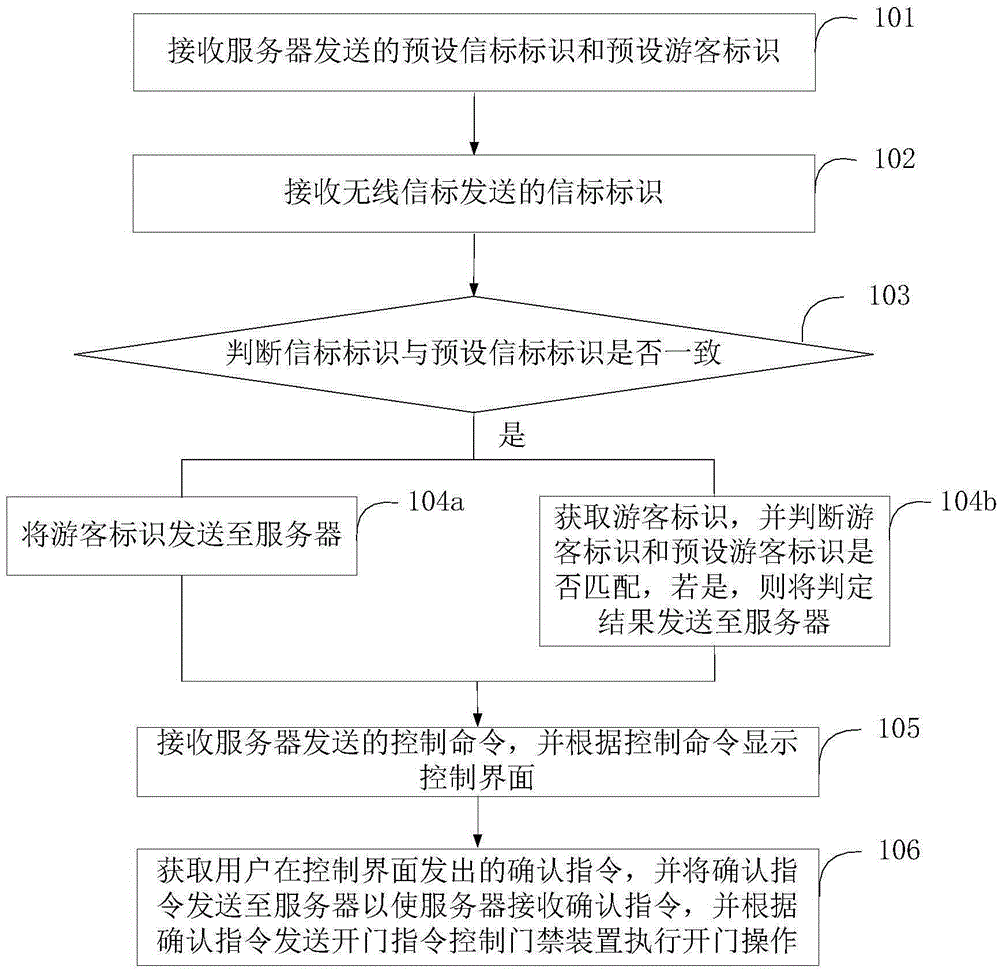
[0061] figure 1 The implementation process of the access control method provided by this embodiment is shown. For the convenience of description, only the parts related to this embodiment are shown, and the details are as follows:
[0062] In step 101, the preset beacon identifier and preset visitor identifier sent by the server are received.
[0063] Wherein, the preset beacon identifier is a beacon identifier of a wireless beacon corresponding to the access control device. After receiving the preset beacon ID and preset visitor ID sent by the server, the information that the authority to open the access control device has been obtained can be displayed, so that the user knows that the electronic ticket has been purchased.
[0064] In step 102, a beacon identifier sent by a wireless beacon is received.
[0065] Among them, wireless beacons include Bluetooth beacons and WIFI beacons. Wireless beacons use radio to broadcast a Bluetooth data frame or WIFI data frame at regular...
Embodiment 2
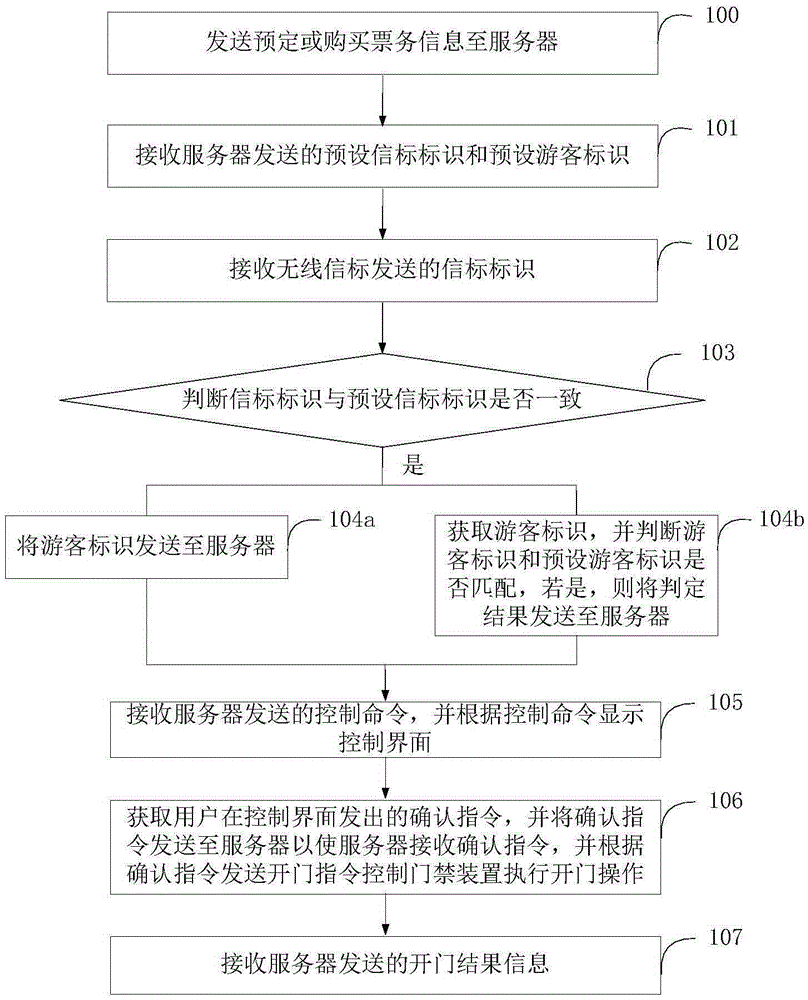
[0082] image 3 The implementation process of the access control method provided by this embodiment is shown. For the convenience of description, only the parts related to this embodiment are shown, and the details are as follows:
[0083] In step 301, the reservation or ticket purchase information sent by the terminal is received.
[0084] In a specific implementation, tourists purchase tickets through the system to trigger the system to generate electronic tickets.
[0085] In step 302a, a preset visitor ID is generated and added to the white list with the authority to open the access control device. Wherein, the preset tourist identification may be a password.
[0086] In step 302b, a preset visitor ID is acquired. Wherein, the preset tourist identification can be password and fingerprint information.
[0087] In step 303, the preset beacon ID and the preset tourist ID are sent to the terminal corresponding to the preset tourist ID.
[0088] In step 304a, the tourist i...
Embodiment 3
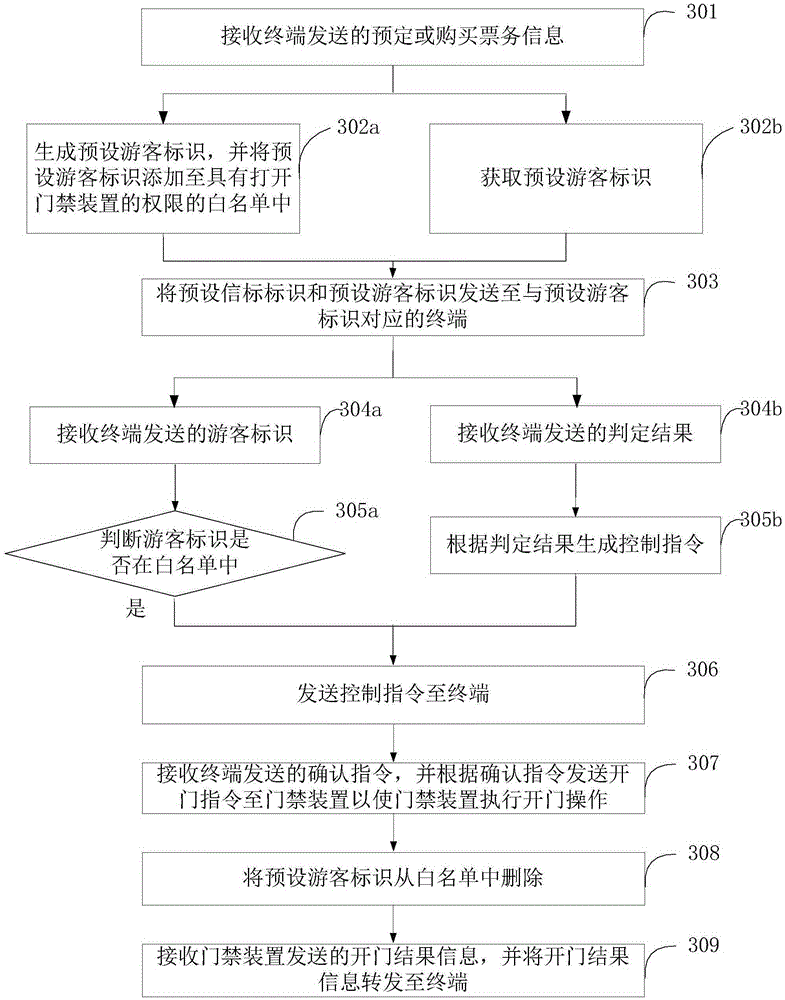
[0104] Figure 4 The implementation process of the access control method provided by this embodiment is shown. For the convenience of description, only the parts related to this embodiment are shown, and the details are as follows:
[0105] In step 401, the terminal sends reservation or ticket purchase information to the server.
[0106] In step 402, the server receives reservation or purchase ticket information.
[0107] In step 403a, the server generates a preset visitor ID, and adds the preset visitor ID to the white list with the authority to open the access control device.
[0108] In step 403b, the server acquires a preset visitor ID.
[0109] In step 404, the server sends the preset beacon identifier and the preset visitor identifier to the terminal corresponding to the preset visitor identifier.
[0110] In step 405, the terminal receives a preset beacon identifier and a preset visitor identifier.
[0111] In step 406, the terminal receives the beacon identifier se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com