Website user password encryption and verification method
A verification method and user technology, which is applied in the field of website user password encryption and verification, can solve problems such as easy guessing of passwords by hackers and easy disclosure of user plaintext passwords.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
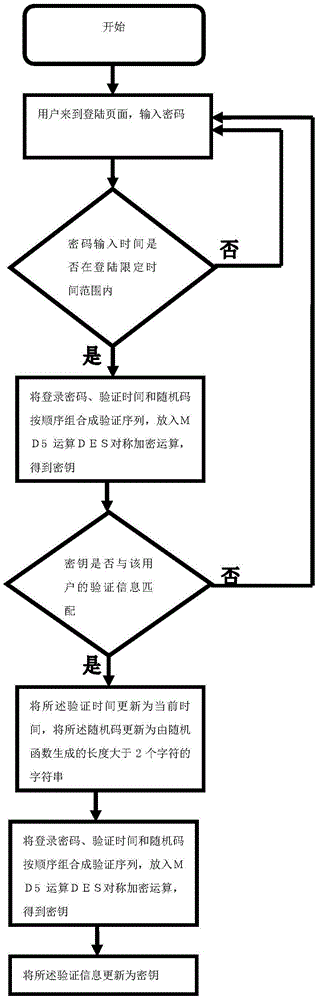
[0025] Embodiment 1: (login method of common user)
[0026] 1. Before user A logs in, the website database stores user A's verification time, verification information, random code and login time limit, where the verification time is the time when the user successfully logged in to the website last time, such as (2015 / 10 / 27 14:54:41 ), the verification information is obtained by the encryption algorithm of the present invention after the user's last successful landing on the website, such as (p73M3PPEa98lkGSGglXLWjHPEphVfsXhtpFs+siE / 3HTj9m0YJFp / A==), the random code is the length generated by the random function after the user's last successful landing on the website For a string of more than 2 characters, such as (NJj), the login time limit is a unified time range set by the website administrator for ordinary users. Users must enter the password within this time range and submit it to the server to enter the next page. One step, otherwise it will prompt wrong password. The ti...
Embodiment 2
[0043] Embodiment 2: (login method of website administrator B)
[0044]1. Before user B logs in, the website database stores user B's verification time, verification information, random code and login time limit. The verification time is the time when the user successfully logged in to the website last time, such as (2015 / 10 / 27 14:54:41 ), the verification information is obtained by the encryption algorithm of the present invention after the user's last successful landing on the website, such as: (p73M3PPEa98lkGSGglXLWjHPEphVfsXhtpFs+siE / 3HTj9m0YJFp / A==), the random code is generated by a random function after the user's last successful landing on the website For a character string longer than 2 characters, such as (NJj), the login time limit is a unified time range set by the website administrator for ordinary users. Users must enter the password within this time range and submit it to the server before they can enter Next step, otherwise it will prompt wrong password. The t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com