Information identification method, information identification equipment and user terminal
A technology for user terminal and information identification, applied in the field of mobile Internet, can solve the problems of poor security guarantee effect, insufficient security guarantee measures, and increase the cumbersome operation of users.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
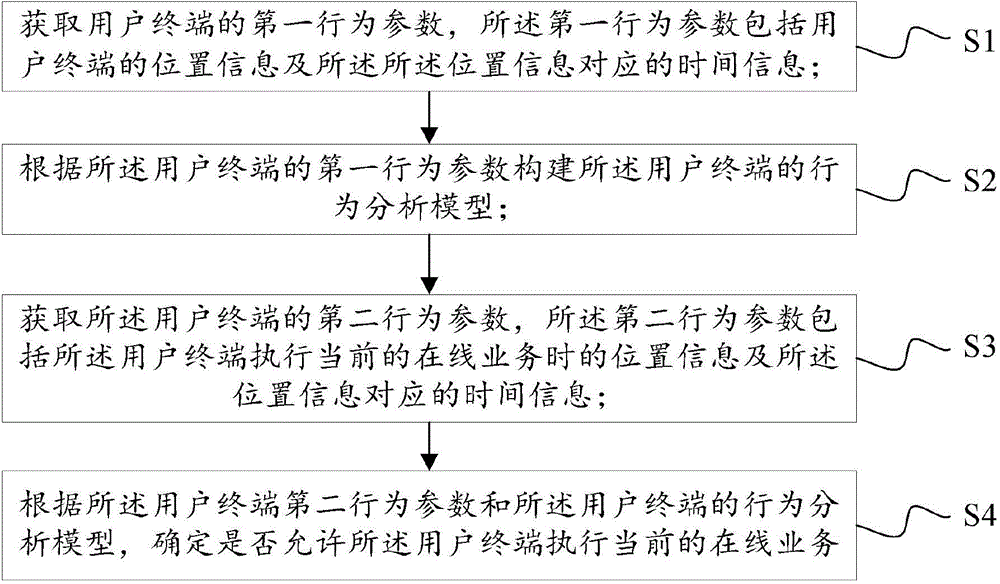
[0076] Refer to attached figure 1 , an embodiment of the present invention provides an information identification method, including:
[0077] S1. Obtain a first behavior parameter of the user terminal, where the first behavior parameter includes location information of the user terminal and time information corresponding to the location information;
[0078] In one embodiment of the present invention, the first behavior parameter of the user terminal may be the previous historical behavior parameter of the user terminal, and the server may continuously obtain the user terminal's behavior parameters within a fixed period (such as one week, one month, one quarter, one year, etc.) Behavioral parameters, and conduct statistical analysis on the acquired behavioral parameters. In a preferred solution of this embodiment, the first behavior parameter includes the location information of the user terminal and the time information corresponding to the location information, such as the ...
Embodiment 2
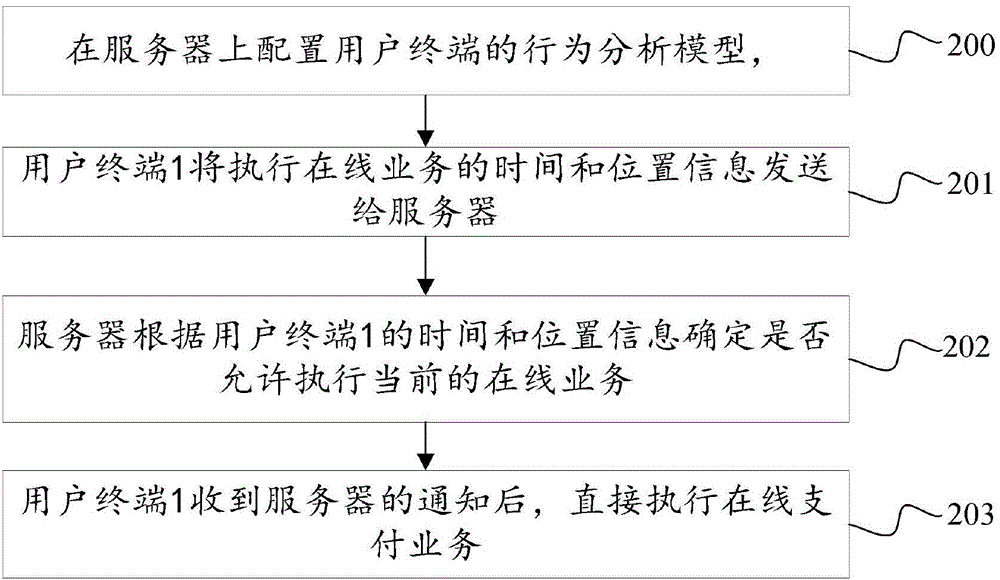
[0113] Refer to attached figure 2 , the embodiment of the present invention also provides an information identification method, wherein:
[0114] 200. Configure the behavior analysis model of the user terminal on the server, specifically establish a matrix on the server, the matrix contains the scene factors of the user terminal in different scenarios, the row vector of the matrix can represent the identity of the user terminal, and the column vector can represent Scene ID, fill in the scene factor of the scene in the intersecting spaces of row vector and column vector, specifically:
[0115]
scene 1
scene 2
scene 3
……
Scene N
user 1
0
1
3
……
0
user 2
1
0
2
1
[0116] ……
……
……
……
……
……
user n
0
1
0
……
1
[0117] In addition, when configured on the server, all areas with a scenario factor greater than 1 are safe areas...
Embodiment 3
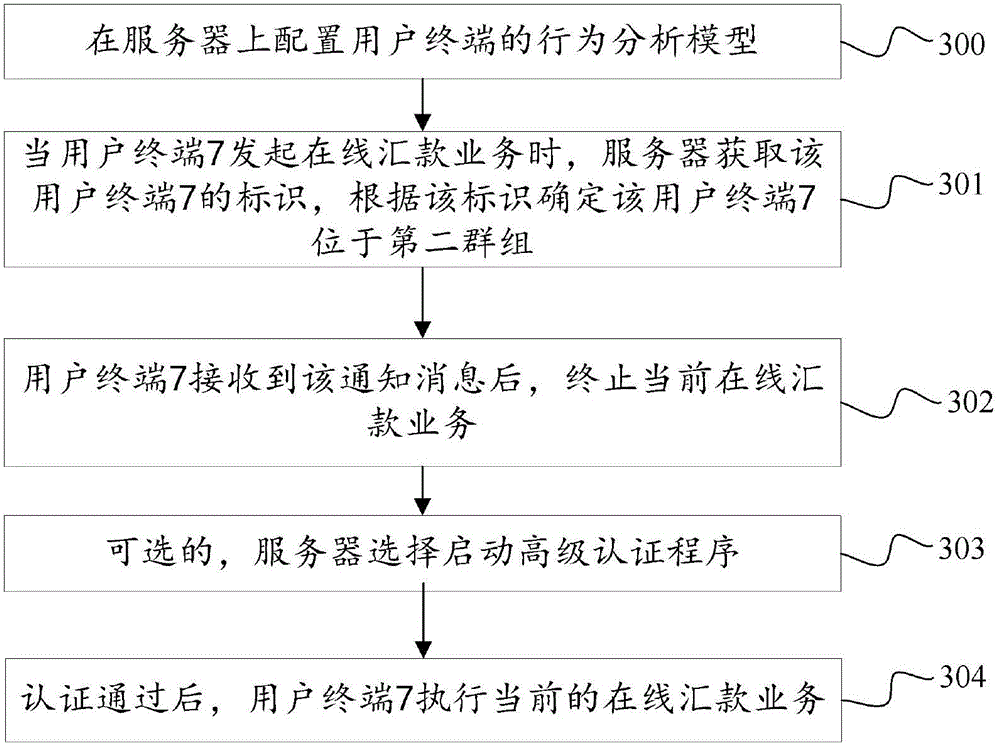
[0122] Refer to attached image 3 , the embodiment of the present invention also provides an information identification method, wherein:
[0123] 300. Configure the behavior analysis model of the user terminal on the server, specifically according to the aforementioned clustering method, cluster and group the user terminals stored on the server, such as clustering user terminals 2, 3, 4, and 5 into the first Group, clustering the user terminals 6, 7, 8, 9 into a second group. The security rule corresponding to the first group is that the user terminals in the group can perform all online services, and the security rule corresponding to the second group is that the user terminals in the group can only perform online payment services;
[0124] 301. When the user terminal 7 initiates an online remittance service, the server obtains the identification of the user terminal 7, and determines that the user terminal 7 is located in the second group according to the identification, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com