Network virtualization method based on software defined network (SDN)
A network virtualization and network technology, which is applied in the field of computer network virtualization, can solve the problems of not realizing the creation of virtual networks based on SDN, and achieve good scalability, throughput improvement, and the effect of controlling burst traffic
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
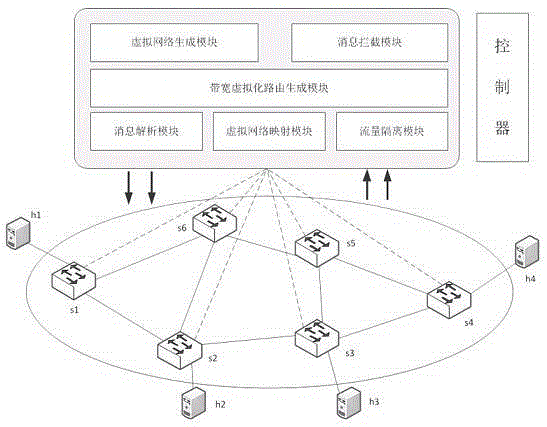
[0055] As the best implementation mode of this technical solution, refer to figure 1 network topology and figure 2 In this example, first establish a virtual network based on the MAC address, set the relevant parameters of the virtual network and add several hosts, and briefly describe the communication process between the hosts in the virtual network. The specific steps are as follows:
[0056] Step 1, create a new virtual network slice1, specify the virtual network name and id, specify the establishment of a virtual network based on the MAC address, specify the traffic isolation parameter as http traffic, and specify the bandwidth requirement of the virtual network as bandwidth;
[0057] Step 2: Add hosts h1, h3, and h4 to the virtual network slice1, and their mac addresses are mac1, mac3, and mac4 respectively. At this time, the set of host addresses in the virtual network slice1 is {mac1, mac3, mac4};
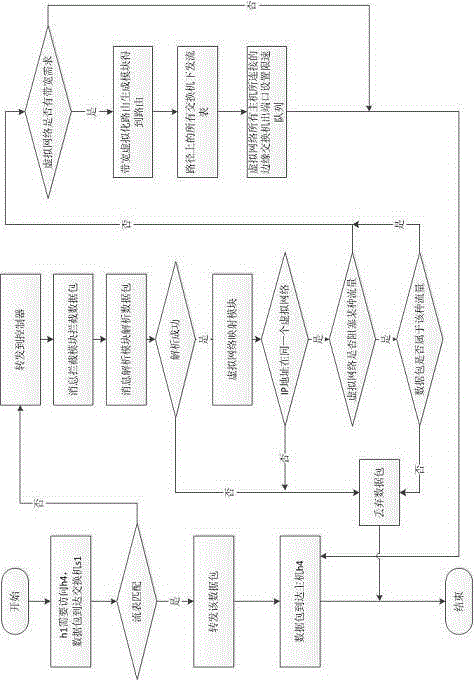
[0058] Step 3, the host h1 sends an http data packet to h4, and the...
Embodiment 2
[0066] As the best implementation mode of this technical solution, refer to Figure 4 , an example shows how to use the MM_ATT algorithm to find a routing algorithm that improves network throughput and avoids competing hotspot links. The specific steps are as follows:
[0067] In step 1, the bandwidth utilization of each link needs to be calculated during the initialization process.
[0068] Step 2. Delete all links whose remaining bandwidth does not meet the bandwidth requirements of the virtual network. The deleted topology is as follows Figure 4 As shown in , the number next to the link represents the bandwidth utilization of the link (unit: %).
[0069] Step 3, assuming that the route from s1 to s11 needs to be calculated, first we set max_hop=6, the algorithm will search the route from s1 to s11 in depth first, and the route found by the algorithm is: s1-s0-s3-s8-s10-s11, the The bandwidth utilization ratios on the path are 4, 6, 6, 6, 4, and it can be found that the m...
Embodiment approach
[0072] As another preferred embodiment of this method, it includes:
[0073] Step 1, when the network is initialized, the controller obtains the SDN network topology information through detection, including switch information and link information;
[0074] Step 2, when the network is initialized, no virtual network exists, and all underlying network resources are temporarily unavailable;
[0075] Step 3, the prerequisite for using network resources is to obtain a virtual network slice, otherwise no network resources can be used, create a virtual network slice, and go to step 4;
[0076] Step 4: Create a virtual network slice and call the virtual network generation module. The virtual network generation module collects information on various request parameters from users, and creates a virtual network slice according to the request parameters. The request parameters include the virtual network ID, name, traffic isolation type, and bandwidth requirements. , after the creation i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com