Image privacy decision recommendation system and method under social network on the basis of privacy rule and perceptual Hash
A social network and perceptual hash technology, applied in the field of privacy protection of social network images, can solve the problems of cumbersome process, error-prone, additional semantic information to the content to be protected by image privacy protection technology, etc., and achieve the effect of reducing privacy leakage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
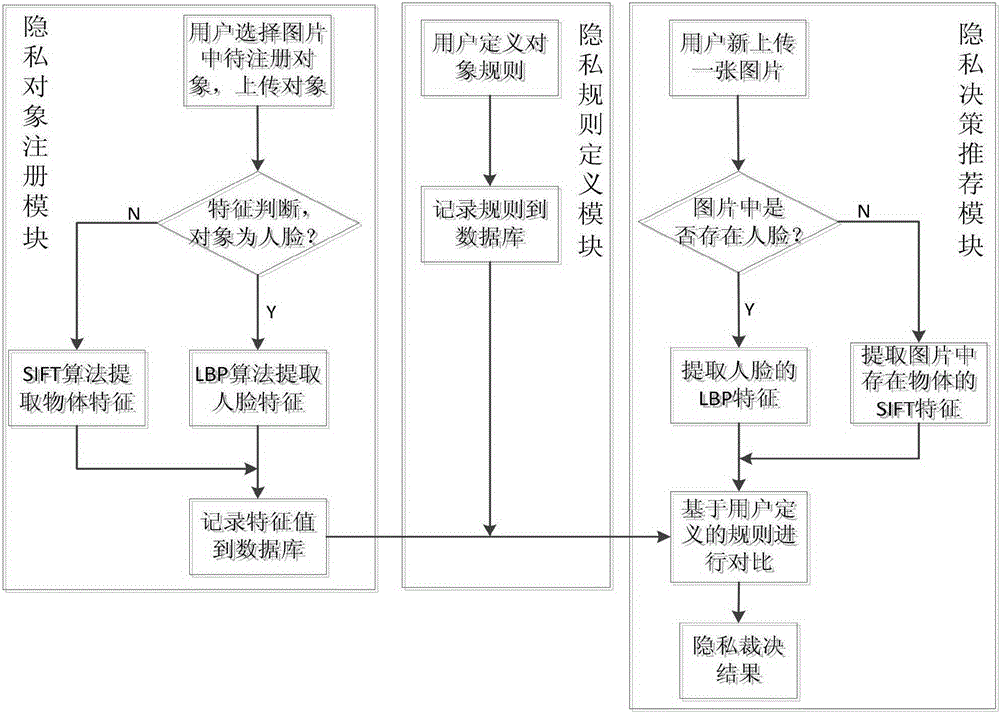
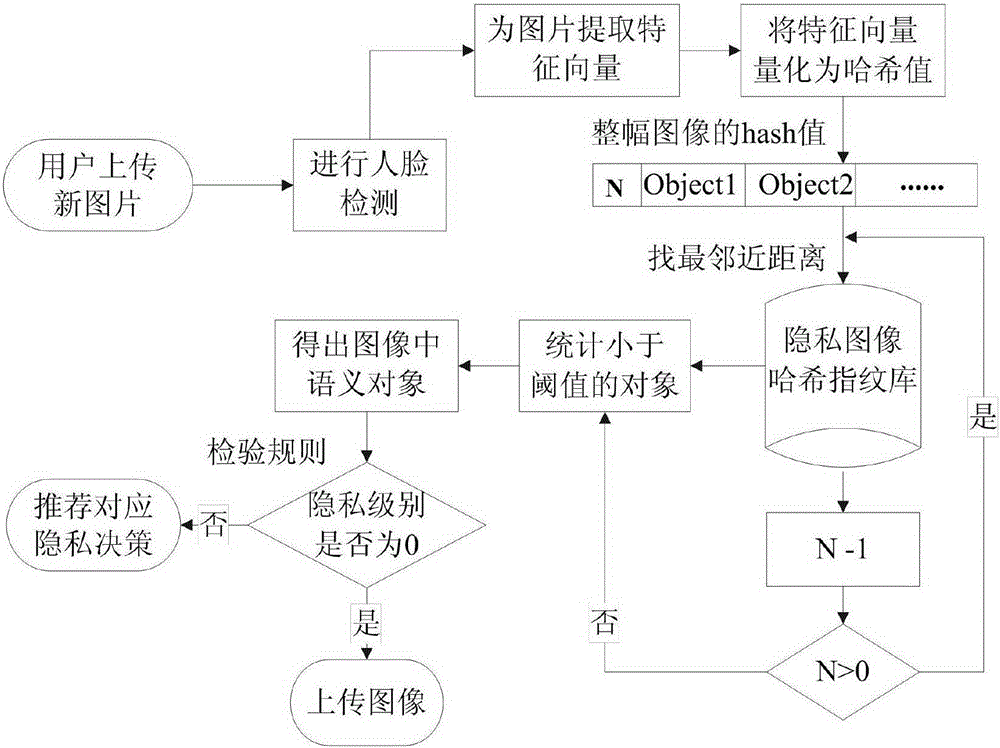
[0030] In this example, if figure 1 As shown, an image privacy decision-making recommendation system based on privacy rules and perceptual hashing social network, the decision-making recommendation system includes: privacy object registration module, privacy rule definition module, privacy decision recommendation module, privacy object hash fingerprint library and privacy rule base;
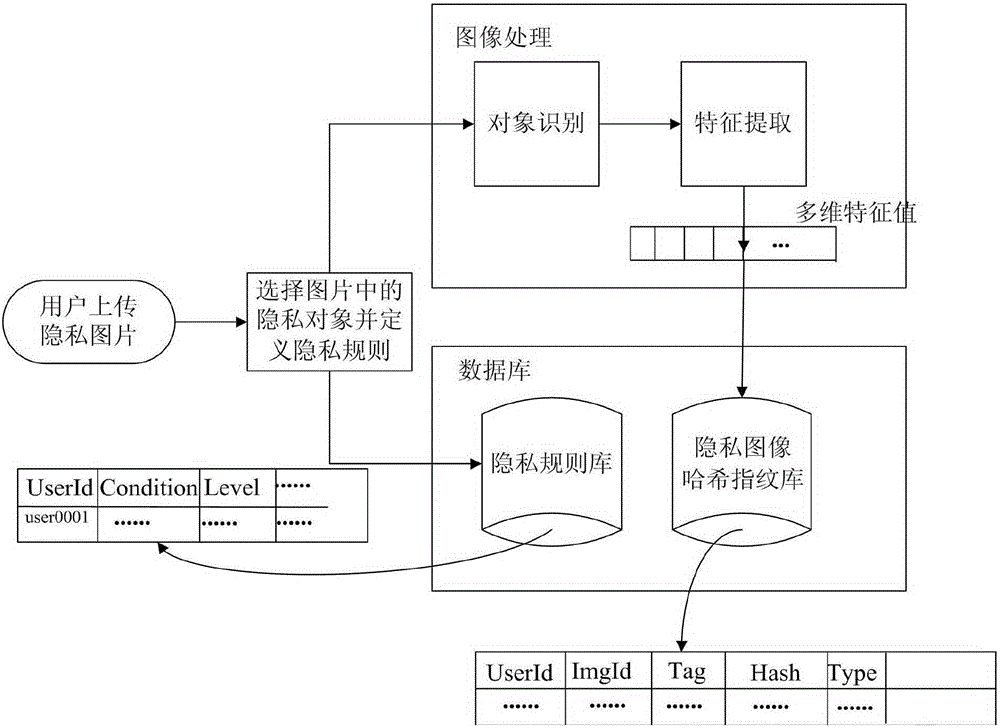
[0031] The privacy object registration module receives the pictures containing the protected objects submitted by the user and the semantic tags set by the user, and performs image recognition on the pictures to obtain the hash fingerprints of the protected objects in the pictures; then compares the hash fingerprints with the set semantic tags Store them together in the privacy object hash fingerprint database;
[0032] The privacy rule definition module is used to select the semantic tags stored in the privacy object hash fingerprint library, obtain the tag set, and set the corresponding privac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com