Method and system for voice communication encryption and decryption
A voice communication, encryption and decryption technology, applied in wireless communication, electrical components, safety devices, etc., can solve the problems of low security and reliability of voice communication, potential safety hazards of mobile phone users, leakage of mobile phone user information, etc., to improve speed, High security, the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] In order to better understand and illustrate the present invention, the present invention will be further described in detail below in conjunction with the accompanying drawings.
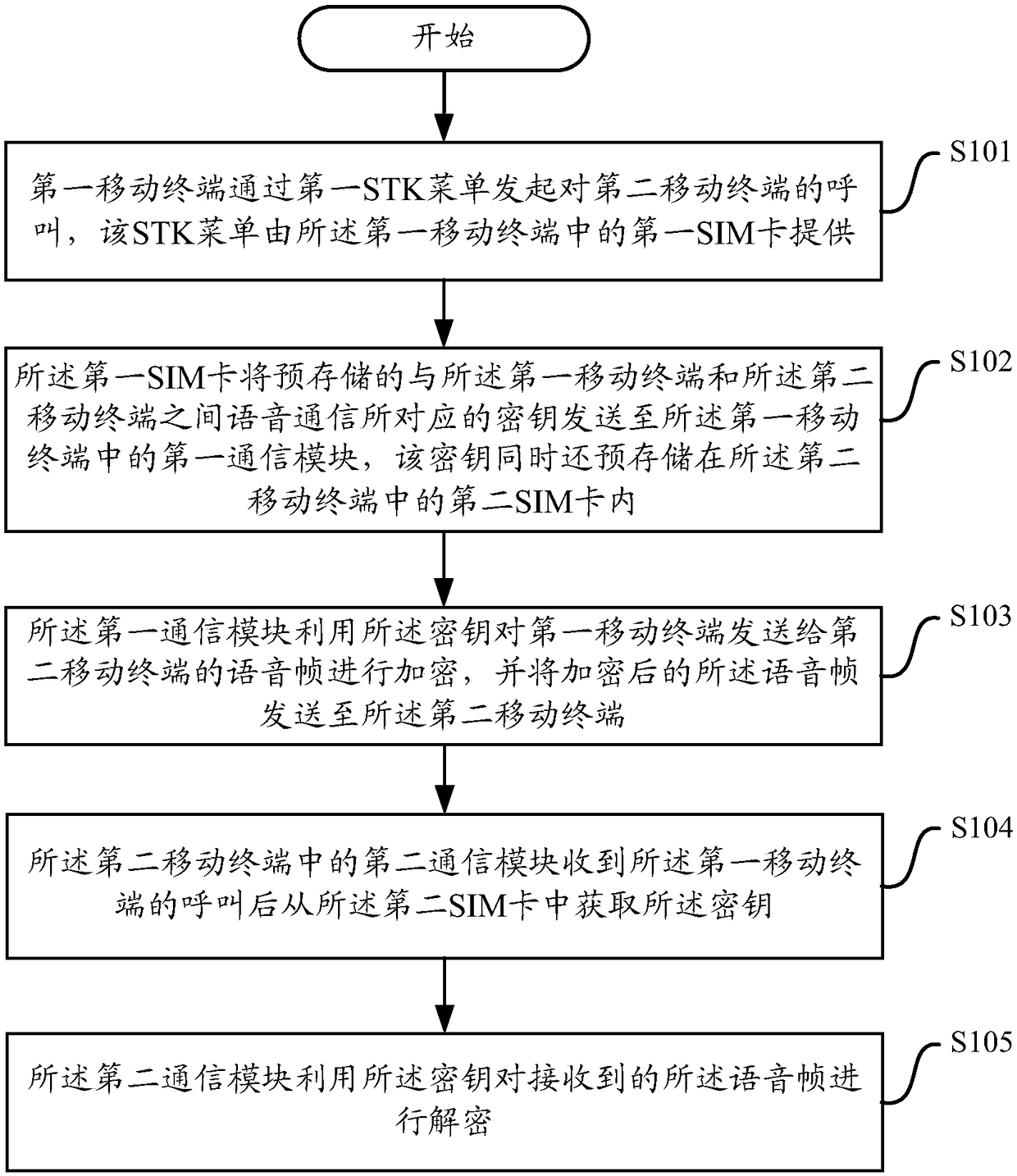
[0033] The invention provides a voice communication encryption and decryption method. Please refer to figure 1 , figure 1 It is a flow chart of the method for encrypting and decrypting voice communication according to the present invention. As shown, the method includes the following steps:
[0034] In step S101, the first mobile terminal initiates a call to the second mobile terminal through the first STK menu, the STK menu is provided by the first SIM card in the first mobile terminal;
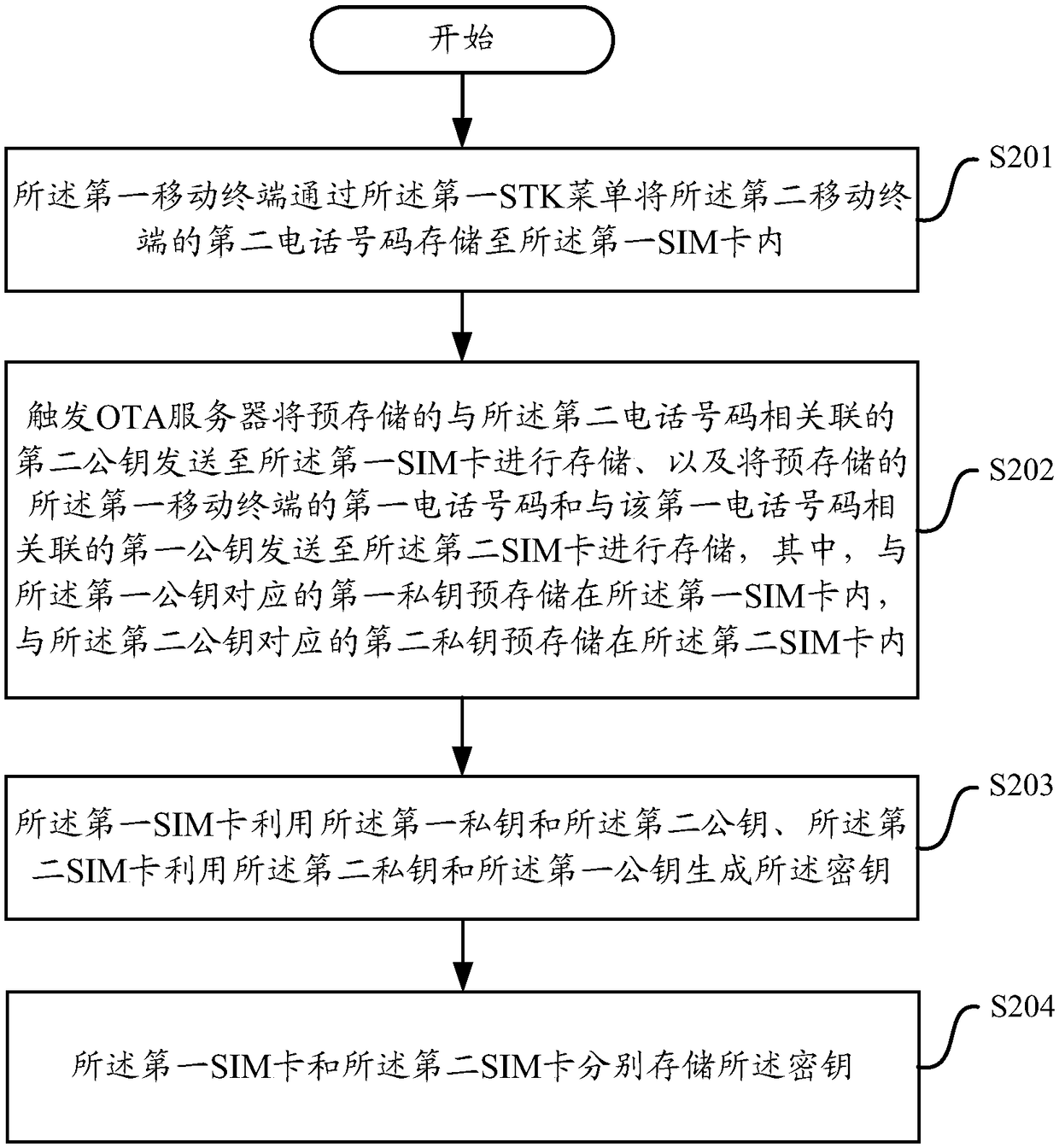
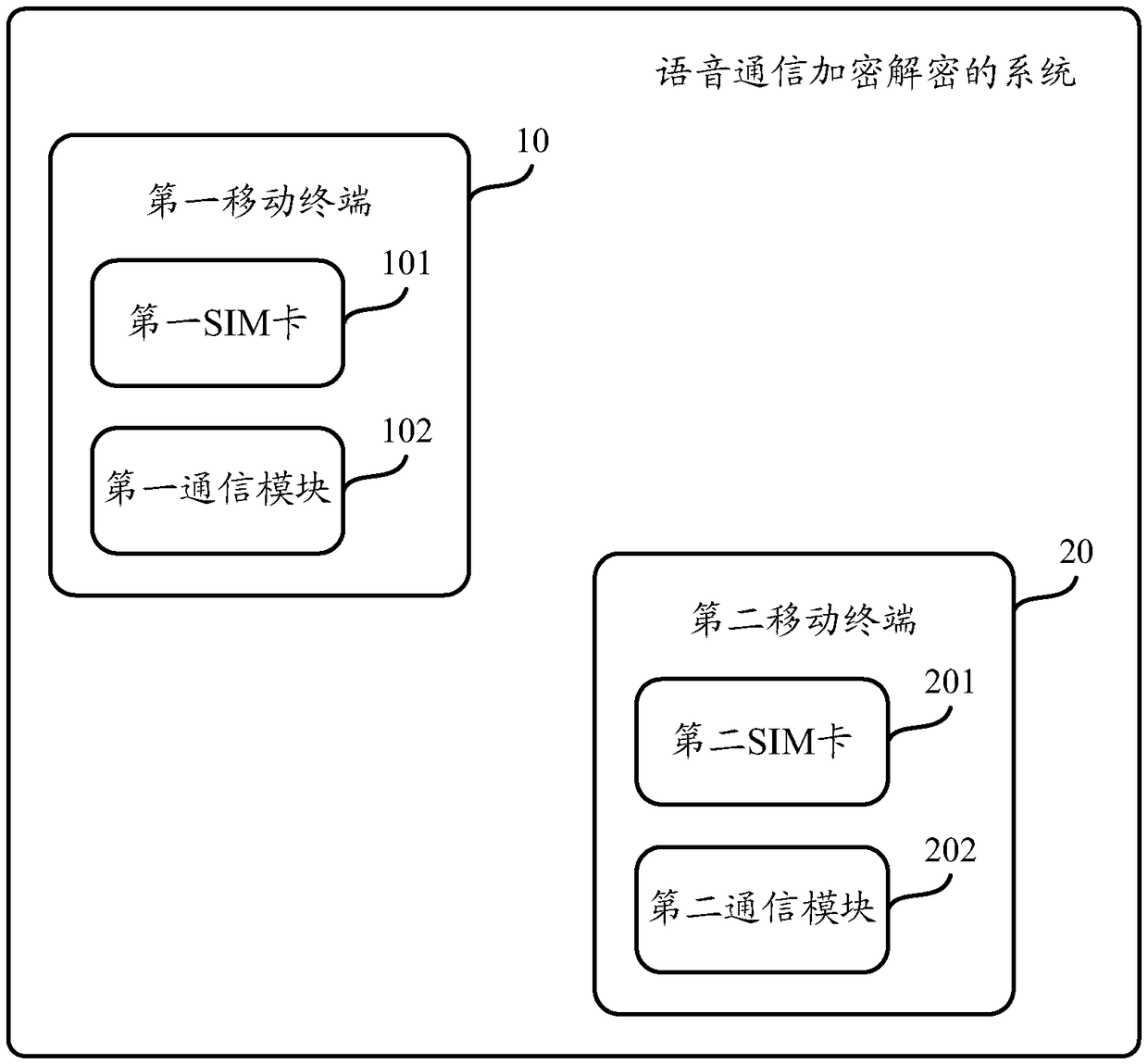
[0035] In step S102, the first SIM card sends the pre-stored key corresponding to the voice communication between the first mobile terminal and the second mobile terminal to the first mobile terminal in the first mobile terminal. The communication module, the key is also pre-stored in the second SIM card ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com