Strategy operation, configuration issuing, conflict resolution and closed-loop management method and system
A technology for policy configuration and conflict handling, applied in the field of communication and information, it can solve the problems of high complexity of data management, user loss, user complaints, etc., to achieve the effect of safe configuration and use of policies, good user experience, and cost reduction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
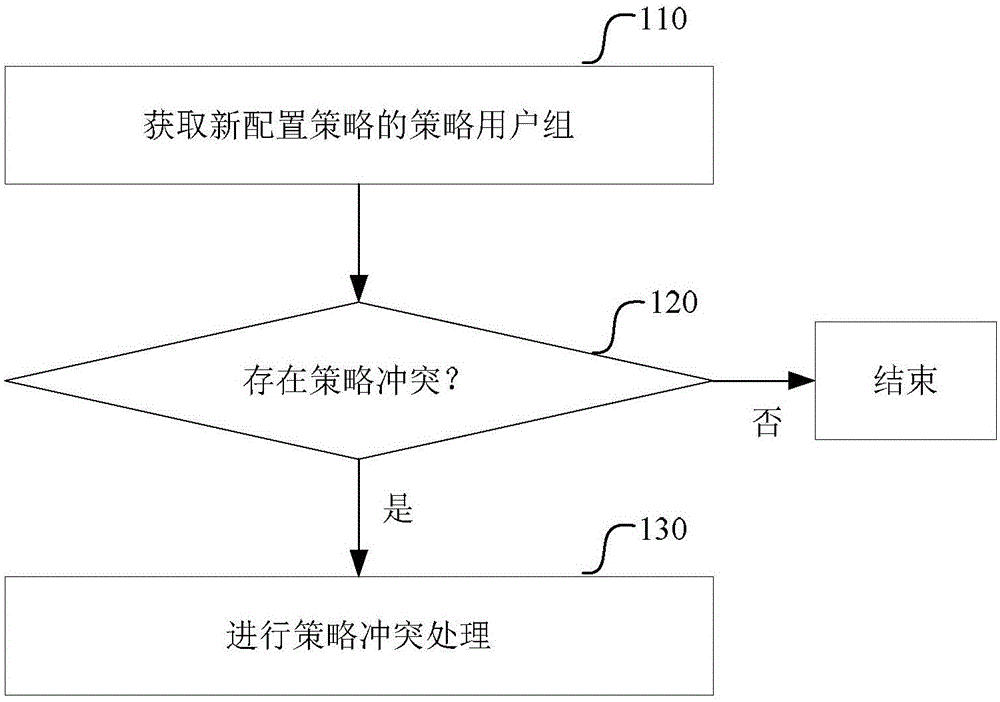
[0079] This embodiment provides a policy conflict handling method, such as figure 1 shown, including:
[0080] Step 110, acquiring the policy user group of the newly configured policy;
[0081] For example, the new configuration policy may be a newly configured policy related to network traffic.
[0082] Step 120, for a user in the policy user group who has subscribed to multiple policies, determine whether there is a policy conflict between the new configuration policy and other policies ordered by the user, if yes, perform step 130, otherwise end;
[0083] In this step, whether there is a policy conflict can be determined one by one for users in the policy user group. However, in order to realize rapid processing of policy conflicts, this embodiment adopts the following grouping method to determine whether there is a policy conflict between other policies ordered by users in the policy user group and the new configuration policy:
[0084] Grouping users who have subscribe...
Embodiment 2
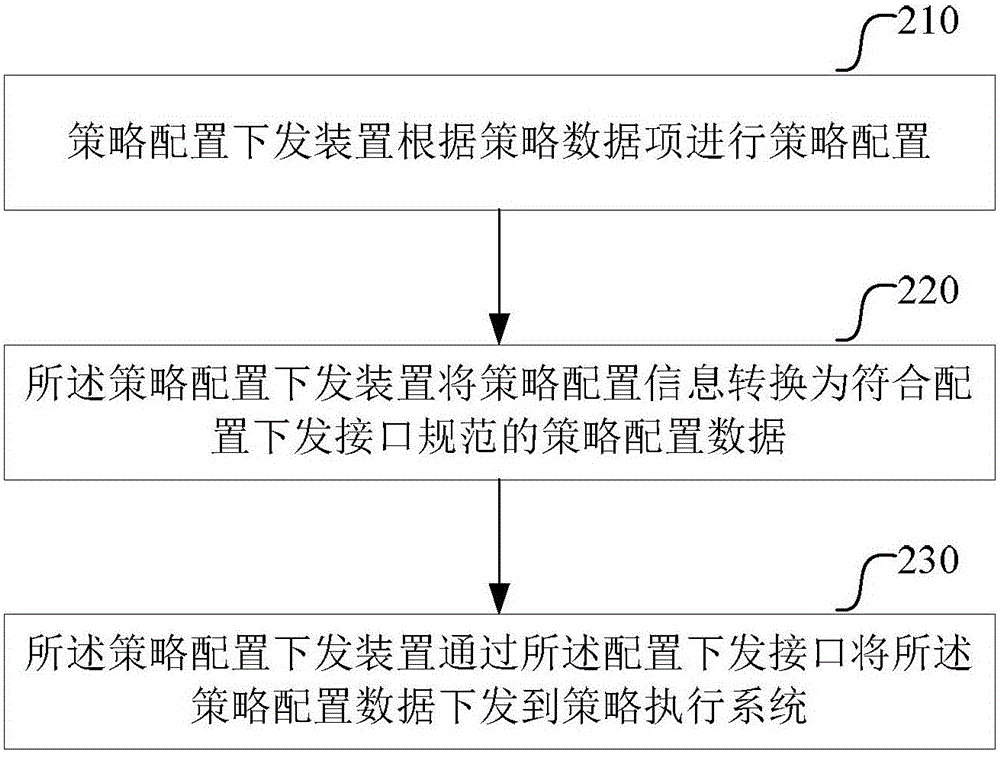
[0165] This embodiment provides a method for delivering policy configuration, such as image 3 shown, including:
[0166] Step 210, the device for issuing policy configuration performs policy configuration according to the policy data item;
[0167] Policy data items need to be collected during policy configuration, and policy data items can be obtained in one or more of the following ways:
[0168] Obtained from the data analysis system:
[0169] Obtained from the business acceptance system;
[0170] Obtained through the administrator interface.
[0171] Policy configuration includes configuring the user policy order relationship between the collected policy user groups and policies; creating policy rules, and configuring trigger conditions and output actions for each policy rule.
[0172] In this embodiment, the policy configuration may be a network traffic-related policy configuration.
[0173] In this embodiment, after the policy configuration of the newly added polic...
Embodiment 3
[0231] The policy operation method provided in this embodiment is applied to the policy operation system 1, such as Figure 5 As shown, the peripheral modules associated with the policy operation system include: a data analysis system 105, a business acceptance system 106, and a policy execution system 108. The administrator 104 can input instructions to the policy operation system 1 through the administrator interface, and the terminal user 107 can interact with the business The acceptance system 106 interacts. The policy operation system 1 can interact with the data analysis system 105 and the business acceptance system 106 through standard or proprietary interfaces.
[0232] in:
[0233] The administrator 104 is the initiator, approver and manager of policies in the policy operation system
[0234] The data analysis system 105 provides data support for the strategic operation system. In one embodiment, the data analysis system can be a system with data collection and anal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com