Discrimination method for advanced persistent threat attack
A discriminative method and continuous technology, applied in the field of information security, can solve problems such as increasing difficulty in maintaining rule bases, insufficient flexibility of rule bases, and limited detection capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The specific implementation manners of the present invention will be described below in conjunction with the accompanying drawings.
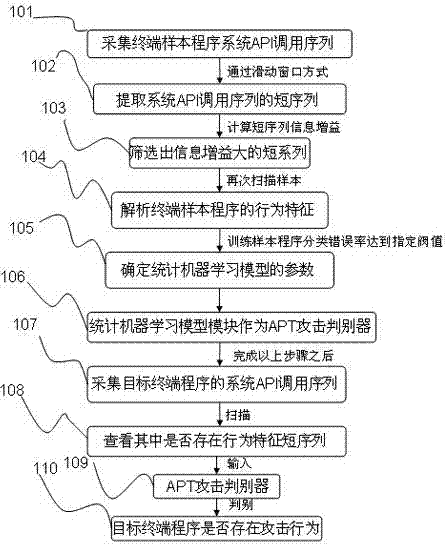
[0021] Such as figure 1 Shown is the method flowchart of the technical solution of the present invention, as can be seen from the figure, the present invention specifically comprises the following steps:
[0022] Step 101: collect each terminal sample program system API call sequence through the terminal program behavior collection module;
[0023] Step 102: Extract the short sequence of the system API call sequence by using the sliding window method through the MapReduce module;
[0024] Step 103: Calculate the short sequence information gain of each system API call, and select the short sequence with a large information gain value as the program behavior feature;
[0025] Step 104: Scan the system API call sequence of each terminal sample program again through the MapReduce module to obtain the behavioral characteristics of the termin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com