Anti-fake verification method
A verification method and verification key technology, which is applied in business, equipment, digital data authentication, etc., can solve the problems of inability to perform repeated verification, inconvenience for consumers, and inability to truly prevent the circulation of counterfeit products, so as to ensure uniqueness and Identity determinability, ease of use, and the effect of expanding application scenarios
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0012] The present invention will be described in detail below with reference to the drawings and examples.
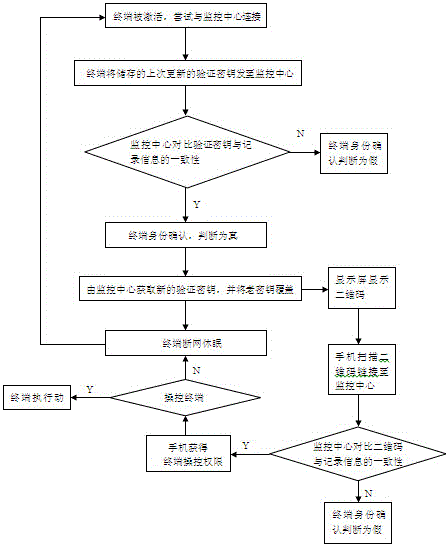
[0013] like figure 1 As shown, in the anti-counterfeiting verification method of the present invention, the terminal intermittently performs data connection with the remote monitoring center through the network. When the terminal disconnects from the network connection, some applications can be closed to increase battery life. Activate, when activated, exchange data with the monitoring center, and store the verification key representing its identity in the terminal. The verification key is in the data form of a two-dimensional code, which is generated by the monitoring center and obtained spontaneously by the terminal when it is connected. And the monitoring center will update and transform it in real time, and the monitoring center will record the relevant information of each terminal obtaining the key; when the user activates the terminal, the terminal will connect t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com