Implementation method, equipment and system of secure communication service
A technology of secure communication and implementation method, which is applied in the field of information security, can solve the problem of low security of user communication services, achieve the effect of improving security and meeting the needs of communication with different security levels
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
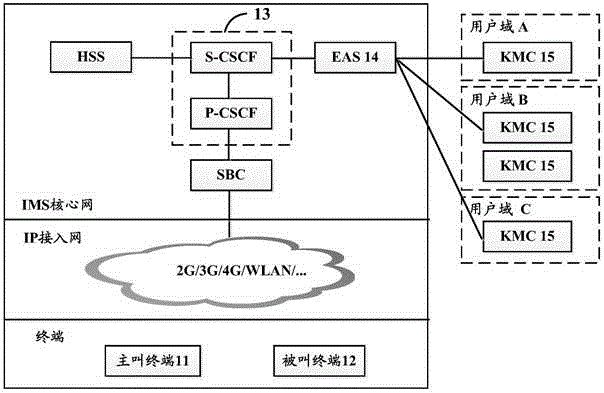
[0106] Such as Figure 4 As shown, it is a schematic flowchart of the implementation method of the secure communication service in Embodiment 1 of the present invention, and the implementation method of the secure communication service can be applied to image 3 In the confidential communication business system shown. Specifically, the method may include the following steps:
[0107] Step 101: The EAS receives an initial session request message from the calling terminal forwarded by the call session control unit at the network side, and the initial session request message carries confidential communication indication information for indicating that the call is an encrypted call.
[0108] Specifically, the initial session request message may generally be an initial session request message based on the SIP protocol, including an INVITE message and a MESSAGE message, etc., which is not limited in this embodiment of the present invention.
[0109] Further, in the embodiment of t...
Embodiment 2
[0201] Embodiment 2 of the present invention further describes the implementation method of the secure communication service described in Embodiment 1 of the present invention by taking the action execution party as an example of a call session control unit at the network side. Such as Figure 5 As shown in , it is a schematic flowchart of the implementation method of the secure communication service described in Embodiment 2 of the present invention, and the implementation method of the secure communication service can be applied to image 3 In the confidential communication business system shown. Specifically, the method may include the following steps:
[0202] Step 201: The call session control unit at the network side receives the initial session request message initiated by the calling terminal, and the initial session request message carries confidential communication indication information for indicating that this call is an encrypted call.
[0203] Specifically, sim...
Embodiment 3
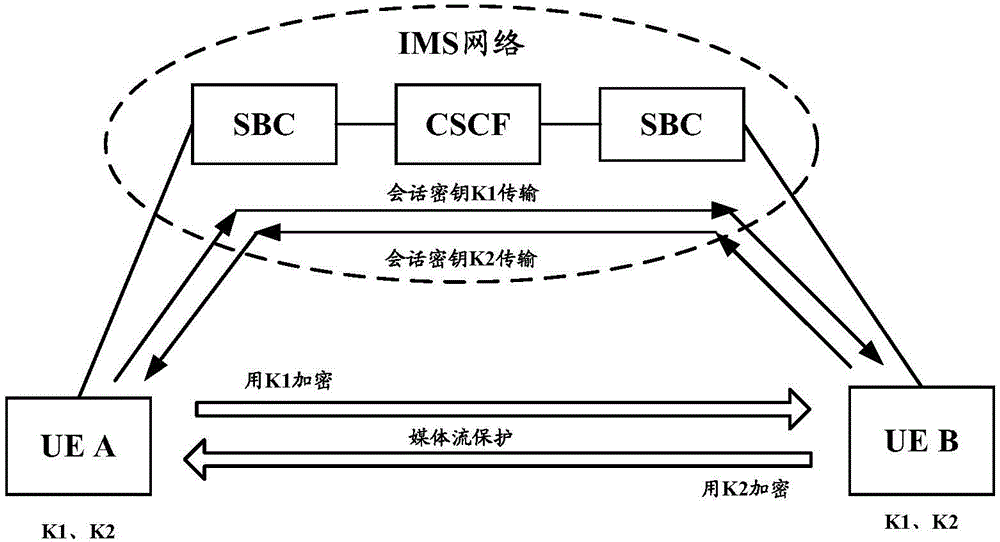
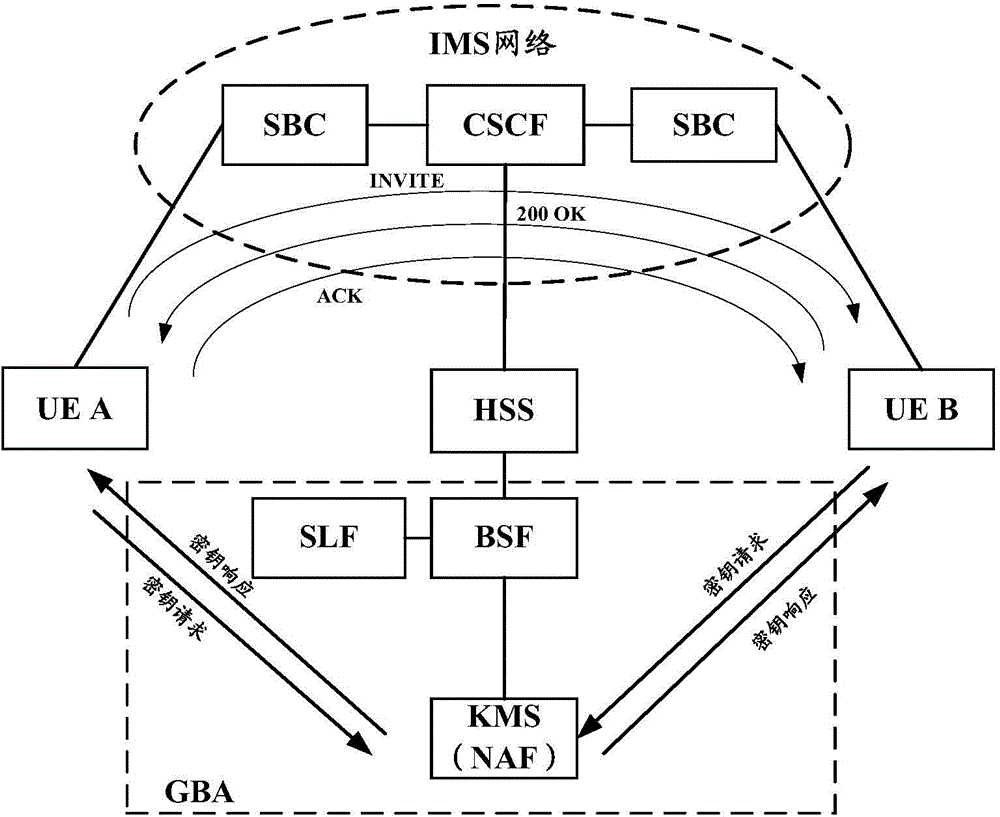
[0224] The third embodiment of the present invention is based on image 3 The system architecture diagram of the secure communication service shown is taken as an example to further describe the implementation method of the secure communication service described in Embodiment 1 or Embodiment 2 of the present invention. Assume that end user A and end user B have subscribed to the secure communication service and belong to the same user domain, and two KMCs with different security levels are deployed in the user domain, which are used to support the commercial encryption algorithm (KMC1) and the common encryption algorithm ( KMC2) Two confidential communication services with different security levels; and, assuming that in the third embodiment of the present invention, the same INVITE message can be used to simultaneously complete the call establishment between the calling and called terminals and trigger EAS to select the corresponding KMC to Generate keys and other operations....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com