Data interaction method, equipment and system
A data interaction and transaction technology, applied in the field of communication, can solve problems such as harming the interests of users
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
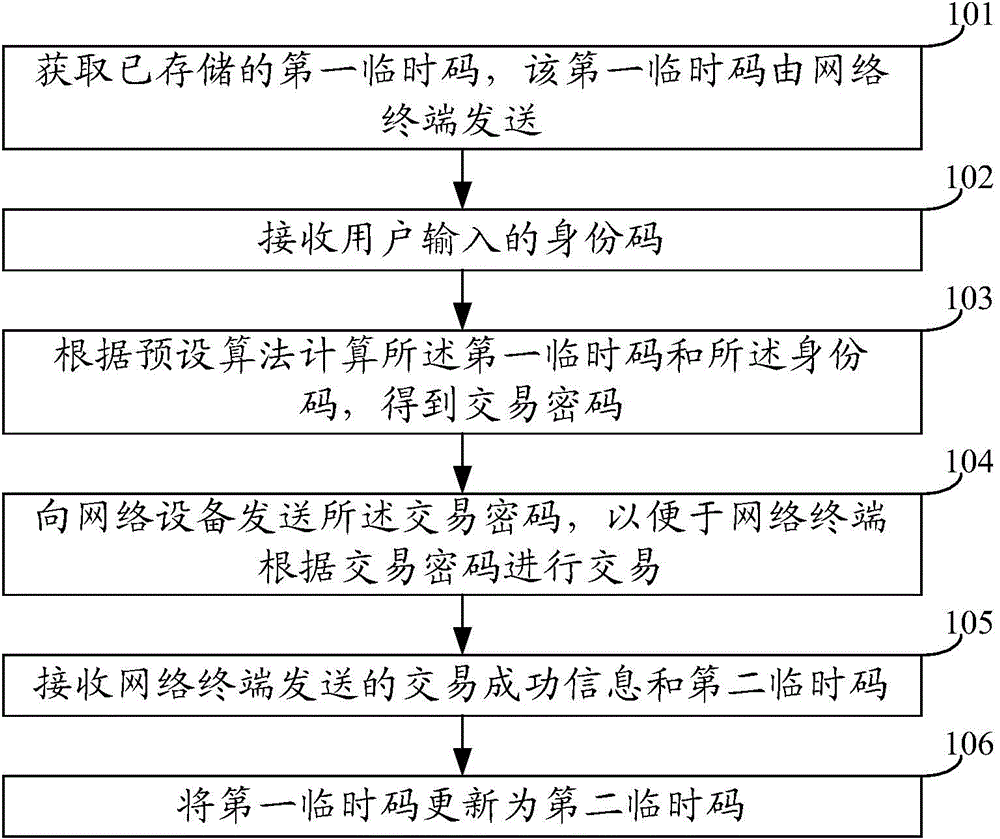
[0051] An embodiment of the present invention provides a data interaction method, which is applied to a user terminal, and the user terminal may include a mobile phone, a tablet computer, a notebook computer, a desktop computer, etc., such as figure 1 As shown, can include:
[0052] Step 101. Obtain a stored first temporary code, which is sent by a network terminal.
[0053] Step 102, receiving the identity code input by the user.
[0054] Step 103: Calculate the first temporary code and the identity code according to a preset algorithm to obtain a transaction password.
[0055] Step 104, sending the transaction password to the network terminal, so that the network terminal can conduct transactions according to the transaction password.
[0056] Step 105, receiving the transaction success information and the second temporary code sent by the network terminal.
[0057] Step 106, updating the first temporary code to the second temporary code.
[0058]In this way, after each ...
Embodiment 2
[0062] An embodiment of the present invention provides a data interaction method, such as figure 2 As shown, can include:
[0063] Step 201: Receive the first transaction password sent by the user terminal, the first transaction password is obtained by the user terminal calculating the first temporary code and the identity code according to a preset algorithm.
[0064] Step 202: Determine the identity code corresponding to the first transaction password according to the correspondence between the stored first transaction password and the stored identity code.
[0065] Step 203, complete the transaction according to the identity code.
[0066] Step 204, sending the transaction success information and the second temporary code to the user terminal.
[0067] Step 205: Calculate the second temporary code and the identity code according to the preset algorithm to obtain the second transaction password.
[0068] Step 206, generating a correspondence between the second transactio...
Embodiment 3
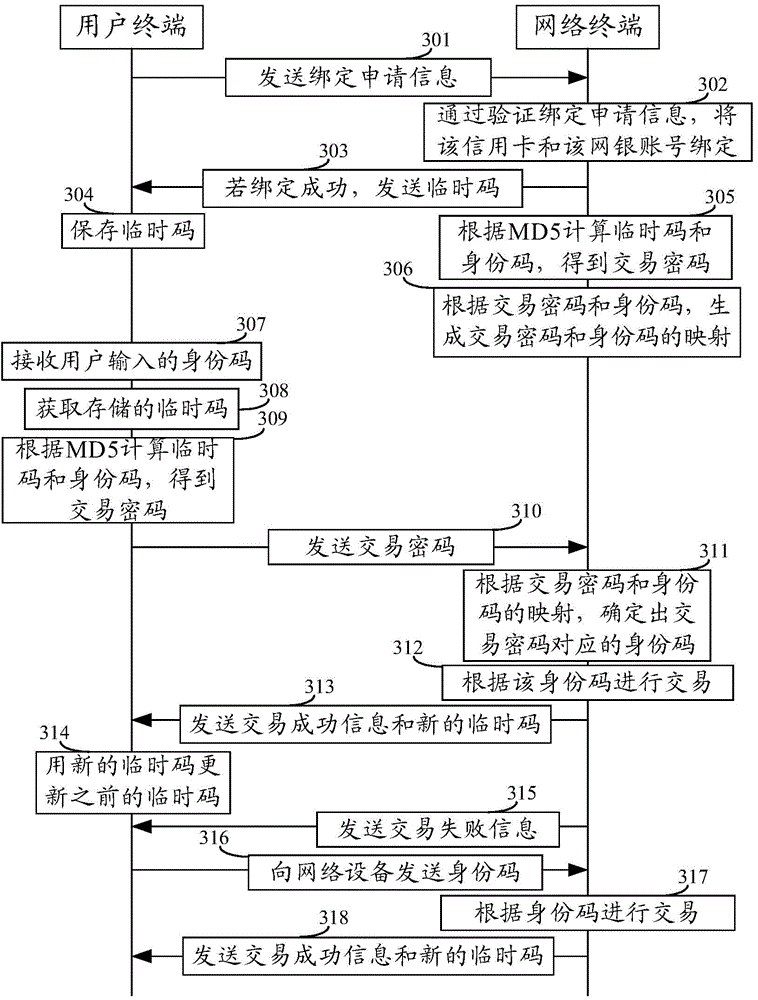
[0073] An embodiment of the present invention provides a data interaction method, which is applied to a data exchange system. The system may include a user terminal and a network terminal. It is assumed that the data exchange system is a system for online payment. Assume that the user pays for an item purchased in an online shopping mall by credit card for the first time. The preset algorithm of this embodiment takes MD5 as an example, such as image 3 As shown, the method includes:
[0074] Step 301, the user terminal sends binding application information to the network terminal.
[0075] The binding application information includes the user's online banking account number, credit card number, credit card password, ID number, name corresponding to the ID number, verification code received by the user terminal, and ID code input by the user. The verification code is a credit card verification code received by the user terminal after the user enters the mobile phone number bo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com