Security threat analyzing method based on service data stream model
A technology of threat analysis and data flow, applied in the field of security analysis of information technology, can solve problems such as lack of security risks, lack of pertinence of security threats, incomplete threat analysis, etc., and achieve the effect of enhancing overall security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment
[0090] A power company plans to build an electric vehicle charging management system to meet four-level applications at the headquarters, provinces, cities, and stations, and realize the operation and management of the electric vehicle intelligent charging and swapping service network. When analyzing the security requirements of the system, the system is analyzed according to a security threat analysis method based on the business data flow model of the present invention.
[0091] Its specific implementation plan is:
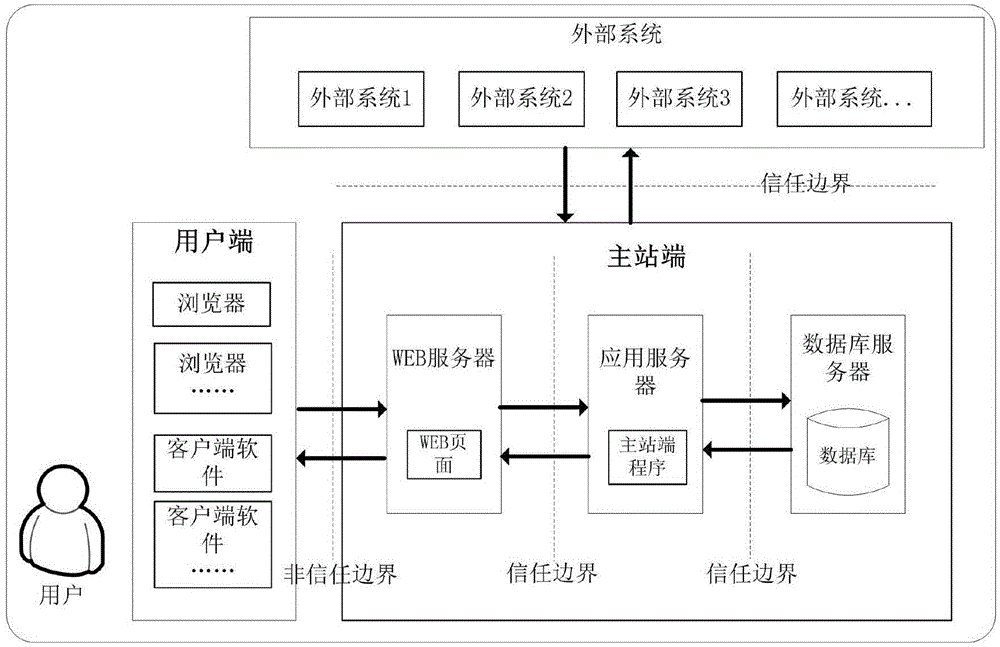
[0092] 1. Conduct research on the basic situation of the system and conduct system decomposition. The system users mainly include headquarters users, provincial users, prefecture-level users, and station-level users. Since the system belongs to the B / S system, the client side of the system mainly includes browsers, and the servers mainly include database servers, front-end servers, and application servers. , Web server, authentication server, workstation, the i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com