Alarming system and method
A technology of alarm system and components
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
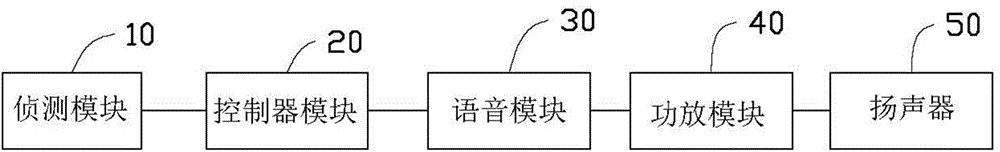
[0040] Please refer to Figure 4 , the preferred embodiment of the alarm method of the present invention comprises the following steps:
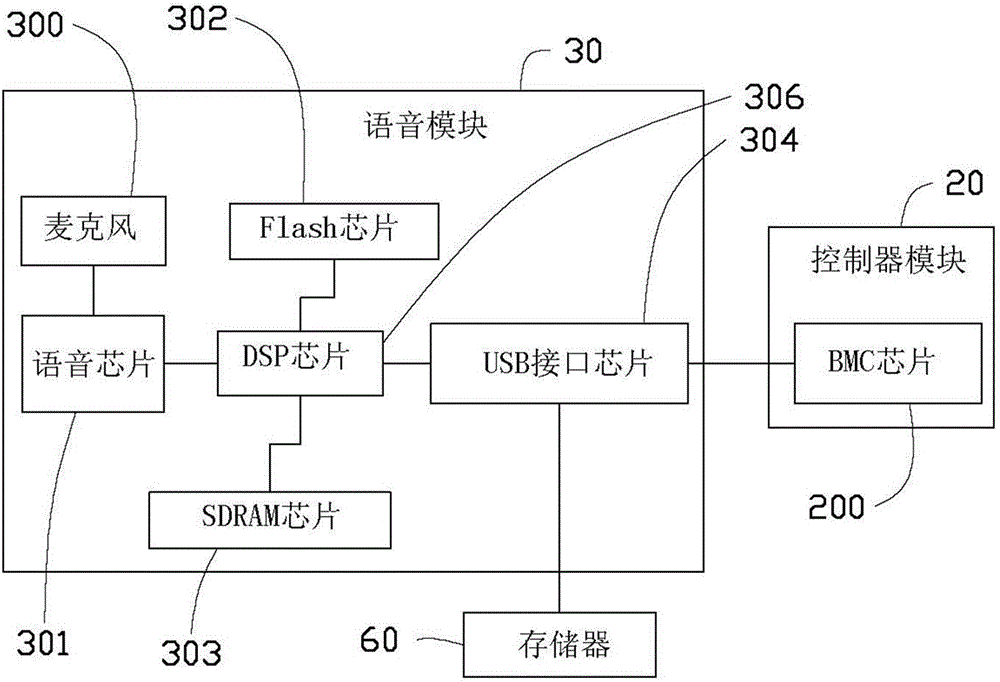
[0041] In step S1, the voice module 30 acquires voice signals corresponding to different abnormal signals.
[0042] Step S2, the voice module 30 samples the acquired voice signal to obtain corresponding voice data.
[0043] Step S3 , the voice module 30 stores each voice data in the memory 60 .
[0044] Step S4, the voice module 30 obtains the storage address of each voice data stored in the memory 60 .
[0045] Step S5 , the voice module 30 transmits the storage address of each voice data to the BMC chip 200 of the controller module 20 .
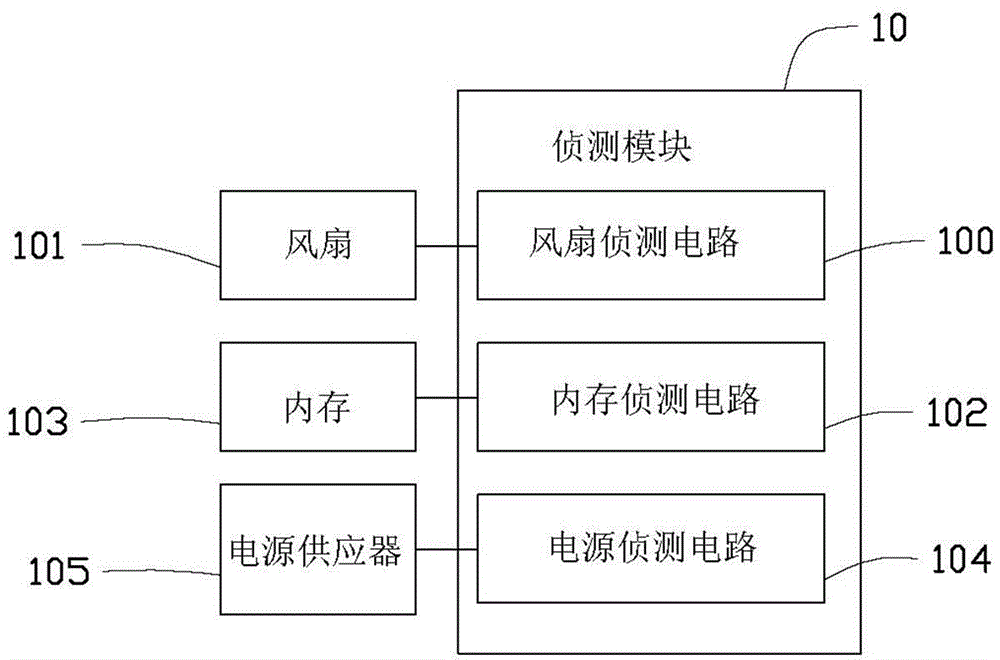
[0046] In step S6, the controller module 20 acquires different types of state information transmitted by the detection module 10 .
[0047] In step S7, the controller module 20 judges whether there is an abnormal component according to the received status information of different types. When there is...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com