Video security access system based on agency and isolation and method of video security access system
A security access and video technology, applied in image communication, selective content distribution, electrical components, etc., can solve the problems of weak security protection, intrusion, lack of security guarantee, etc., and achieve the effect of improving security level and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
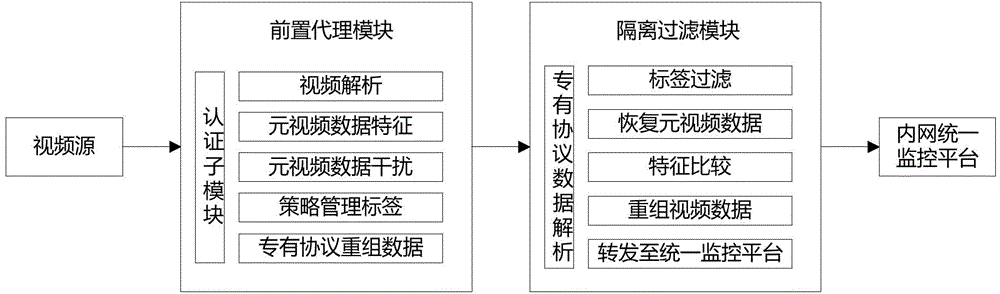
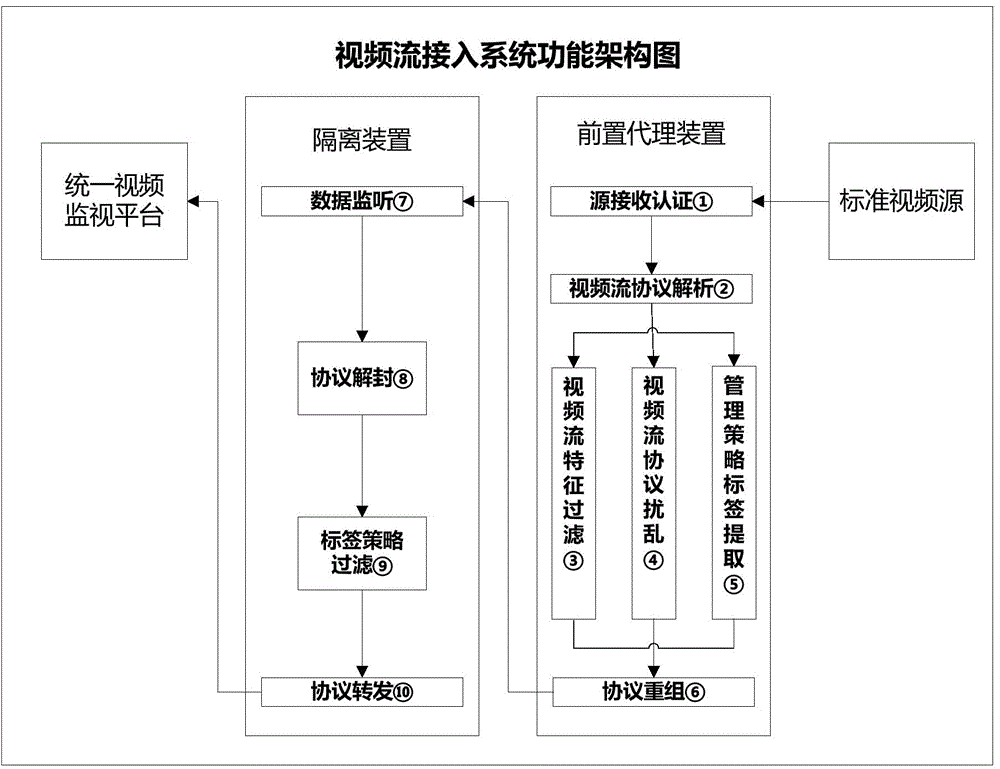
[0074] The present invention proposes a proxy and isolation-based video security access system, which realizes automatic protocol conversion through proxy technology, and the proxy and isolation filter modules jointly build a security channel through a dedicated protocol, thereby realizing efficient data access and protocol protection capabilities. After the front-end server performs feature filtering, scrambling and protocol reorganization on the video, it uploads to the isolation and filtering module through a secure channel based on a dedicated protocol; after the isolation and filtering module completes protocol decapsulation and security policy filtering, it is finally transmitted to the video-on-demand platform . The access system ensures the security of video data during the video access process. The whole system ensures the security, stability, reliability and controllability of video source access.
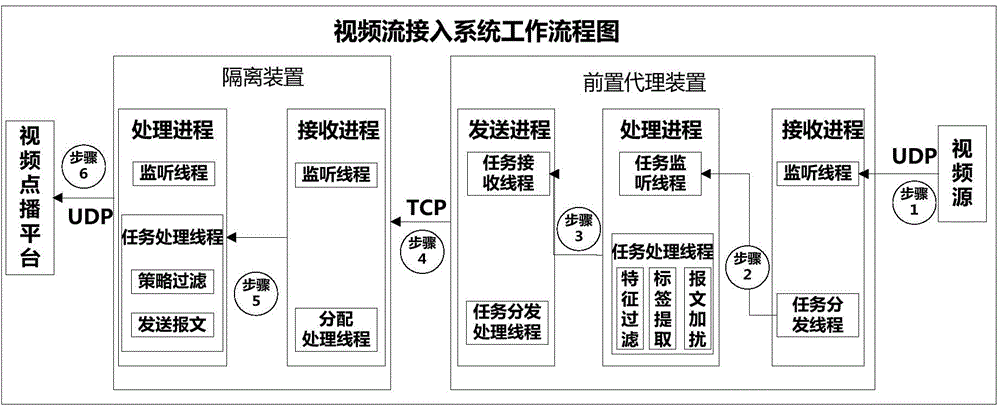
[0075] A proxy and isolation-based video security access method flo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com