Method for establishing hadoop identity authentication mechanism
A hadoop cluster and identity authentication technology, applied in user identity/authority verification, electrical components, transmission systems, etc., can solve problems such as cluster node impersonation, hadoop access control insecurity, etc., achieve efficient operation and ensure reliable security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0012] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0013] Take the following existing environment as an example: an available system package yum source (both local and network); an available three-node hadoop cluster environment, and the host names of the three nodes are: node01.test .com, node02.test.com, node03.test.com.
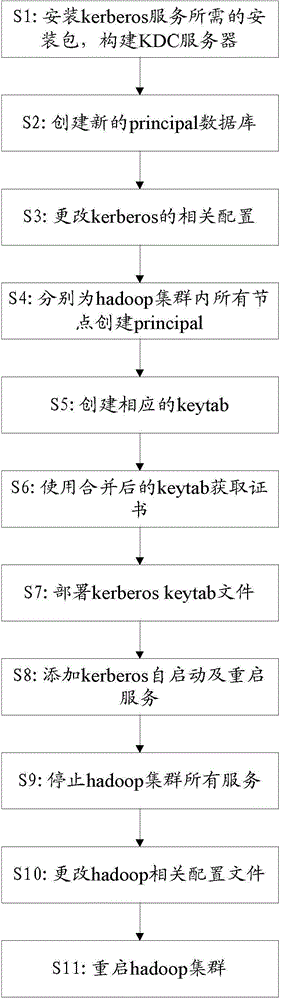
[0014] Such as figure 1 As shown, the specific steps are described below.
[0015] In step S1, the installation package required by the kerberos service is installed, and related configuration files are modified to build a key distribution center (KDC) server. Specifically, all nodes install krb5-workstation, krb5-workstation and their dependent packages, and KDC nodes also install krb5-server.
[0016] In step S2, a new principal database is created for use by the hadoop cluster. Wherein, principal represents a basic entity (for example, a client or a server)...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com