Key agreement method and device in wireless network
A key negotiation and wireless network technology, applied in the field of key negotiation, which can solve the problems of inaccessibility and wireless client authentication failure.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
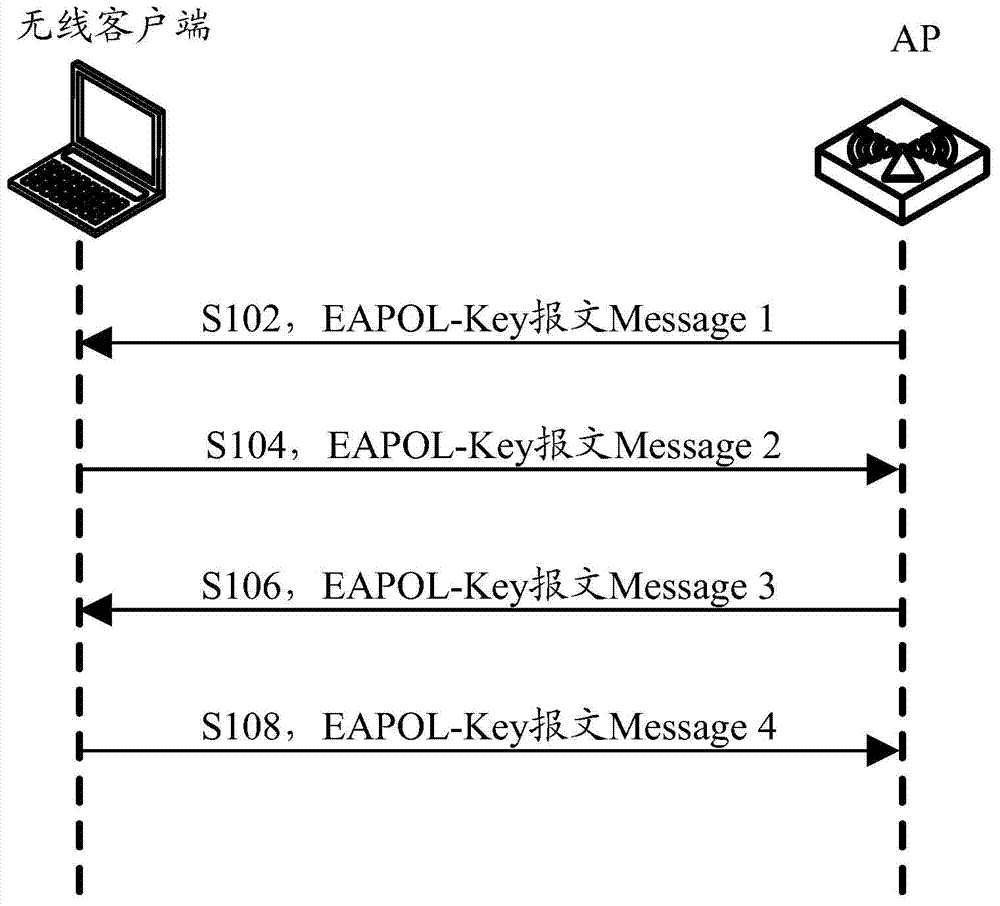
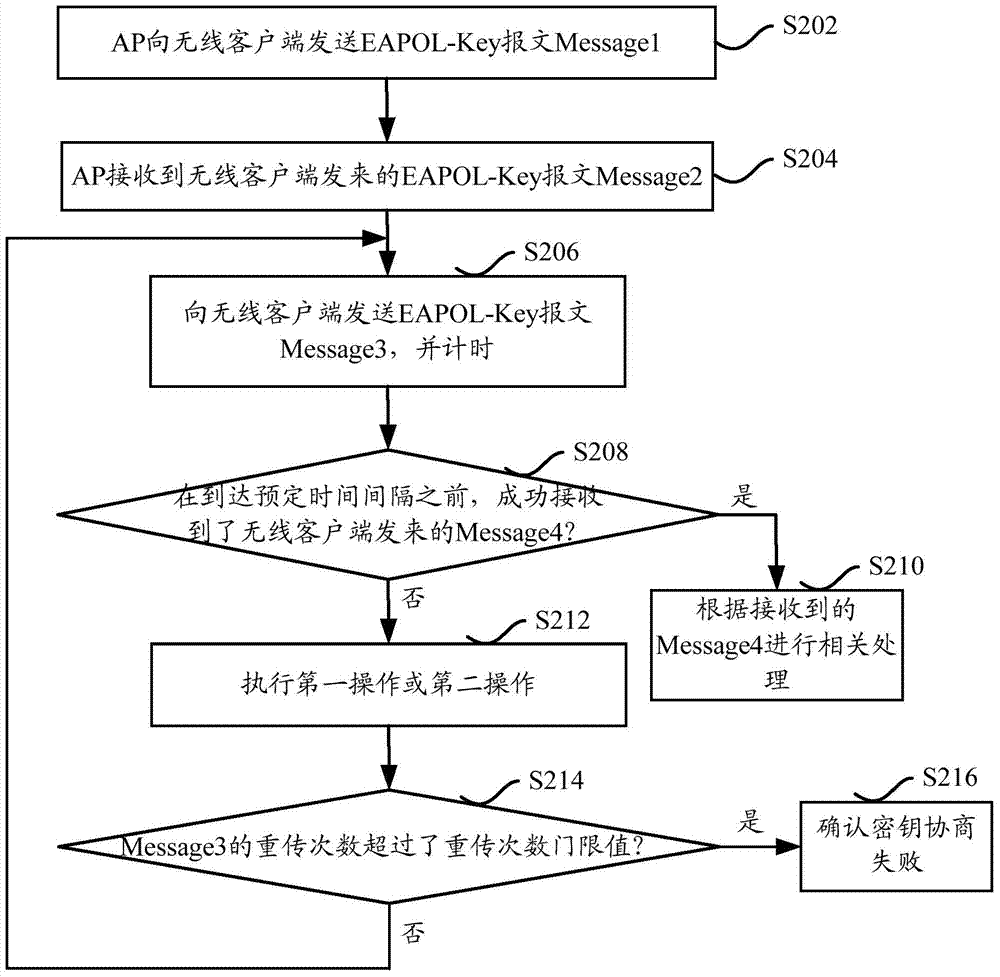
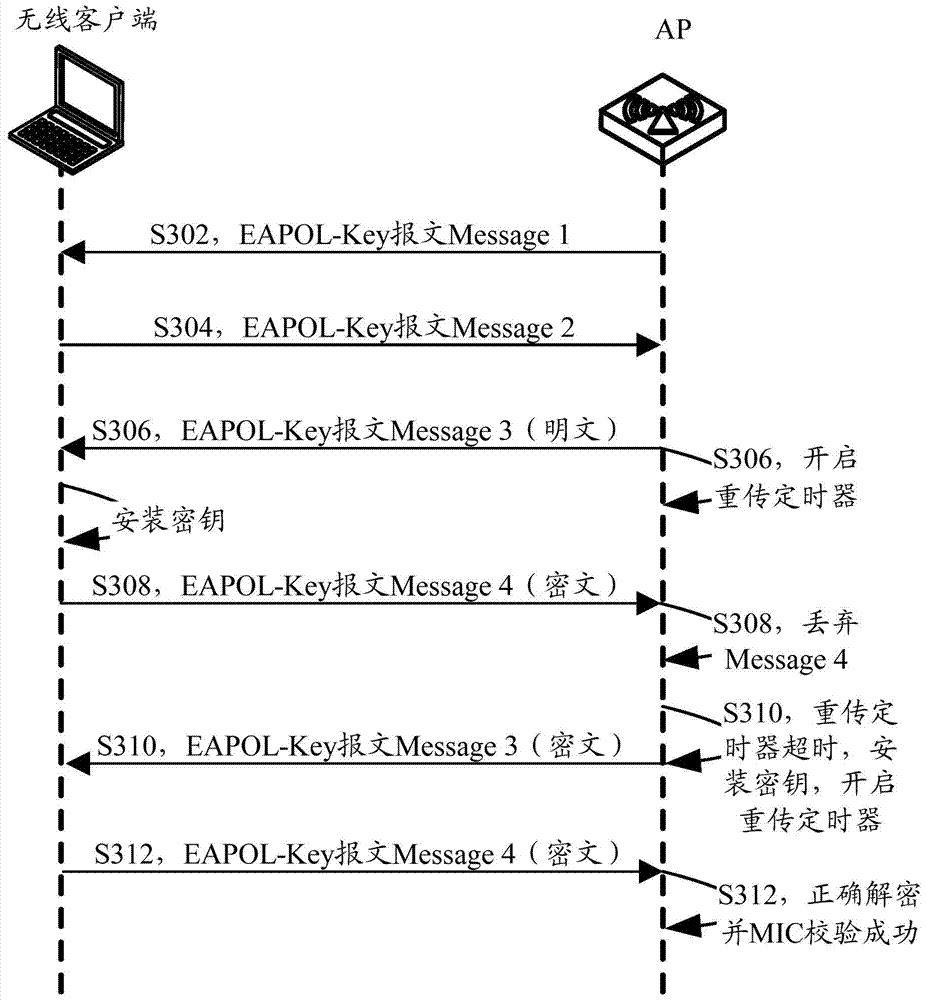
[0022] like figure 1 As shown, the key agreement process of the RSN mode of the prior art includes the following four steps:
[0023] Step S102, the AP sends the EAPOL-Key message Message1 carrying the random number ANonce to the wireless client;
[0024] Step S104, after the wireless client receives Message1, use the random number SNonce generated by the wireless client, the negotiated PMK (Pairwise Master Key, paired master key), and the random number ANonce carried in Message1 to calculate and generate PTK, then use KCK (EAPOL-Key Confirmation Key, LAN-based Extended Authentication Protocol-Key Confirmation Key) in the generated PTK to get MIC (Message Integrity Check, information integrity check), and send a random number to the AP EAPOL-Key message Message2 of SNonce and MIC;
[0025] Step S106, after the AP receives Message2, it uses the random number ANonce, the negotiated PMK, and the random number SNonce carried in Message2 to calculate and generate a PTK, then uses...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com