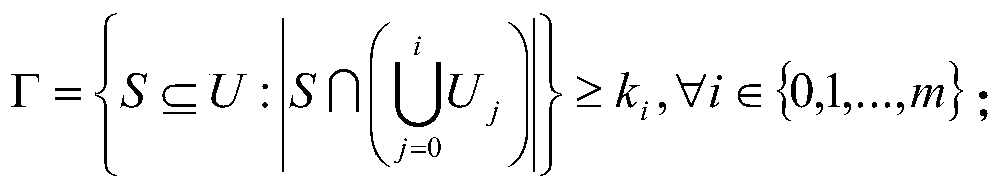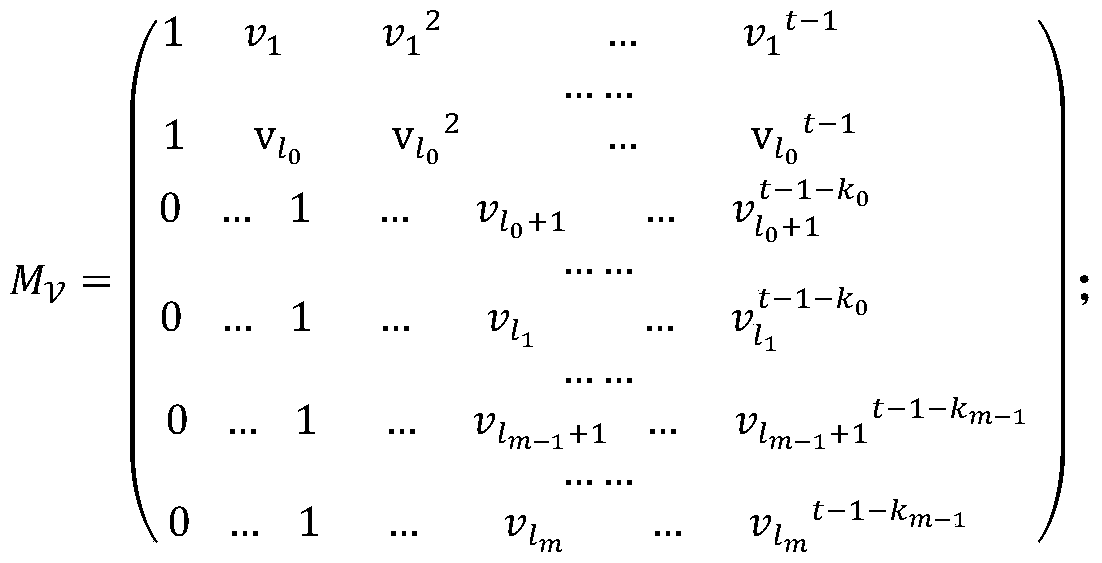A Hierarchical Attribute Encryption Scheme
An encryption scheme, a technology of layered attributes, applied in the usage of multiple keys/algorithms, transmission systems, electrical components, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0073] The present invention will be further described below in conjunction with the accompanying drawings. It should be noted that this embodiment is based on the technical solution, and provides detailed implementation and specific operation process, but the protection scope of the present invention is not limited to the present invention. Example.
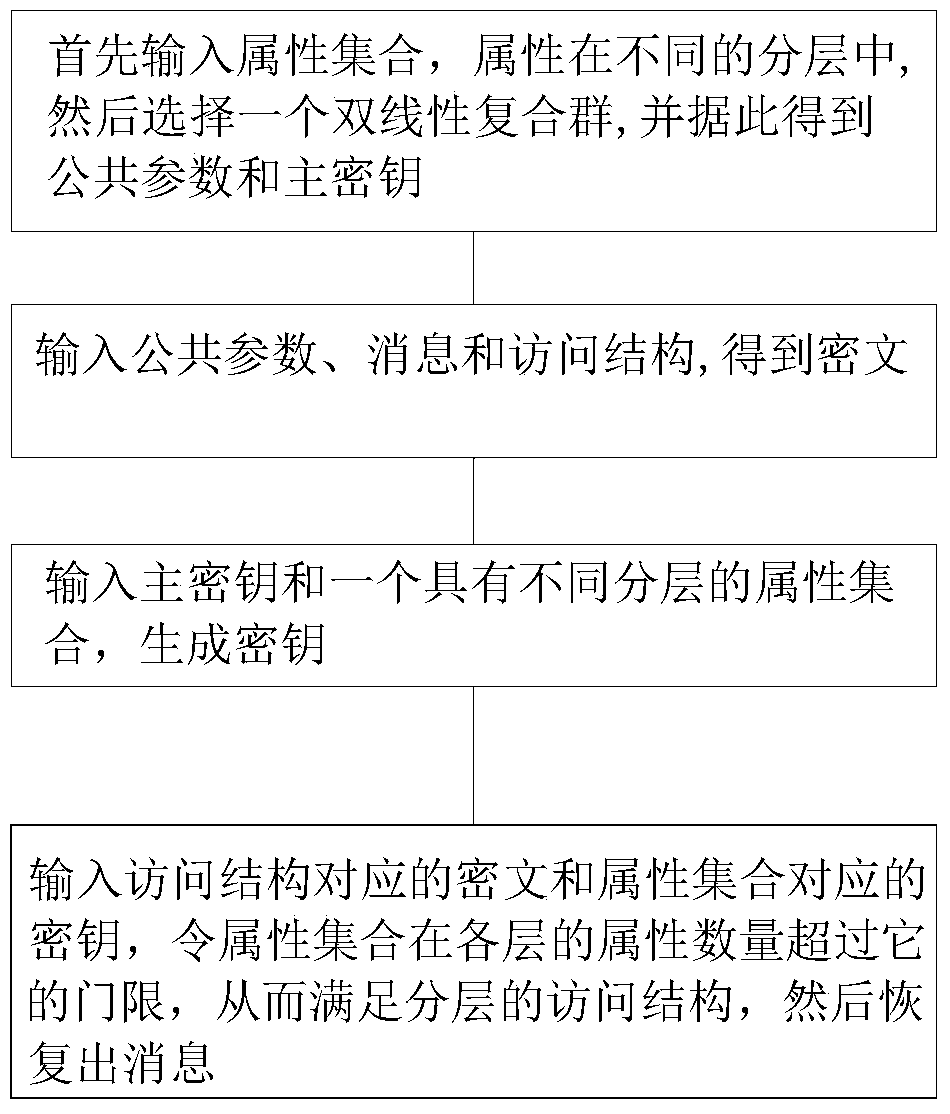
[0074] Such as figure 1 As shown, a layered attribute encryption scheme includes a message M; the scheme includes the following steps:
[0075] S1 initialization and establishment algorithm: first input the attribute set U containing all attributes, and the attributes are in different layers; then select an order of N=p 1 p 2 p 3 Bilinear composite group G, p 1 ,p 2 ,p 3 are different prime numbers, let Indicates that the order is p i The subgroup of , i=1,2,3; then choose random exponents a and α, random group elements where a,α∈Z N ,Z N Represents an integer from 1 to N-1; for |U| attribute elements in U, select t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com