Network security monitoring method and system
A network security and monitoring system technology, applied in the fields of identity authentication, access control, data monitoring methods and systems, can solve problems such as setting security policy obstacles
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
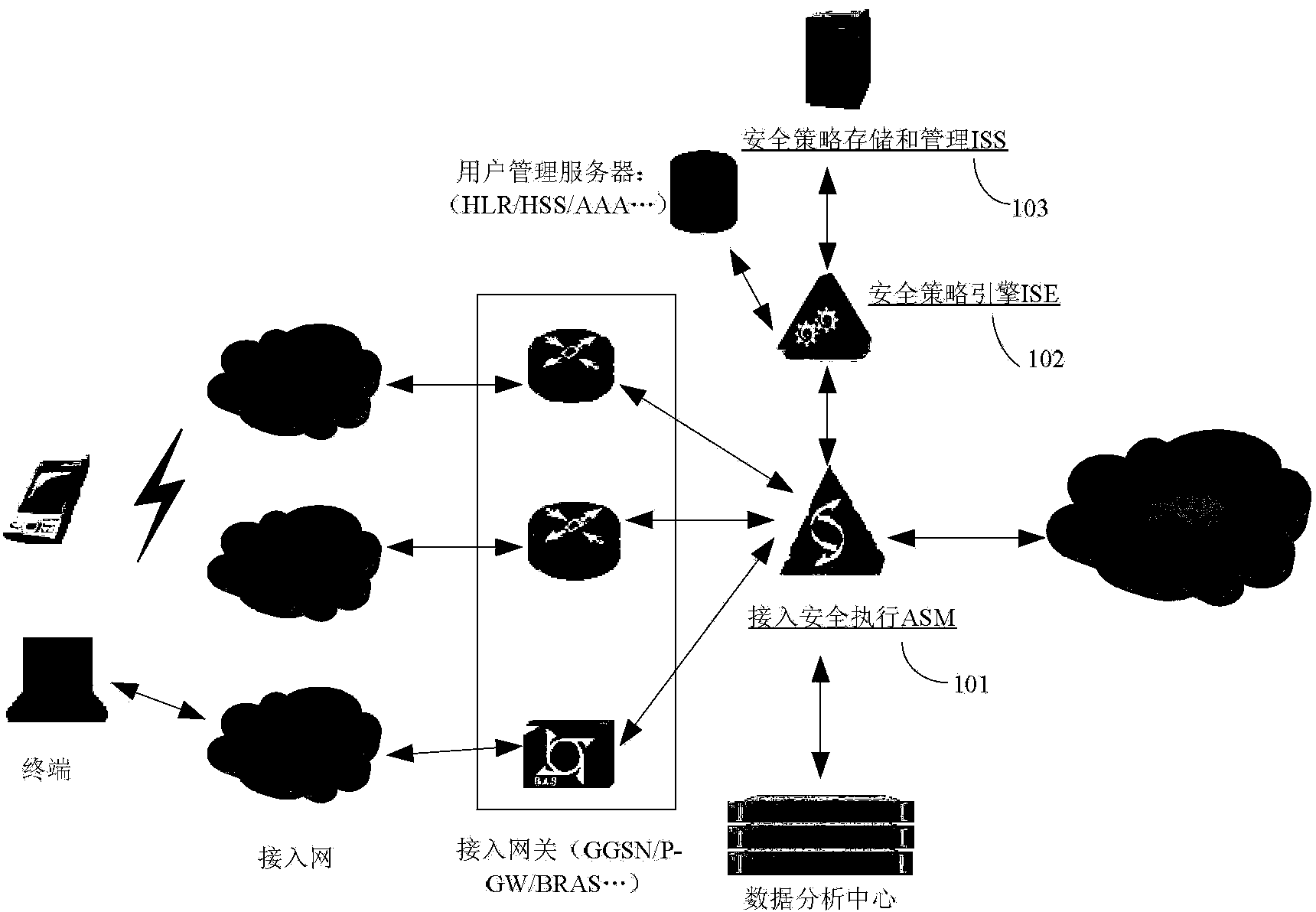
[0040] This embodiment provides a network security monitoring system, including an access security execution unit and a security policy engine unit.
[0041] The access security execution unit obtains the network address or user ID of the user accessing the network, and sends a user security policy query request carrying the user ID and / or network address to the security policy engine unit, and from the security policy Obtain the corresponding user security policy from the user security policy query response returned by the engine unit, and execute the security policy for the user;
[0042] Among them, user identification includes but is not limited to any of the following:
[0043] Mobile phone number, landline phone number, International Mobile Subscriber Identity (IMSI) number, International Mobile Equipment Identity (IMEI) number, user registration name, user unique identifier of user digital certificate.
[0044] Network addresses include but are not limited to any one o...
Embodiment 2
[0069] This embodiment provides a network security monitoring method, the method includes the following operations:
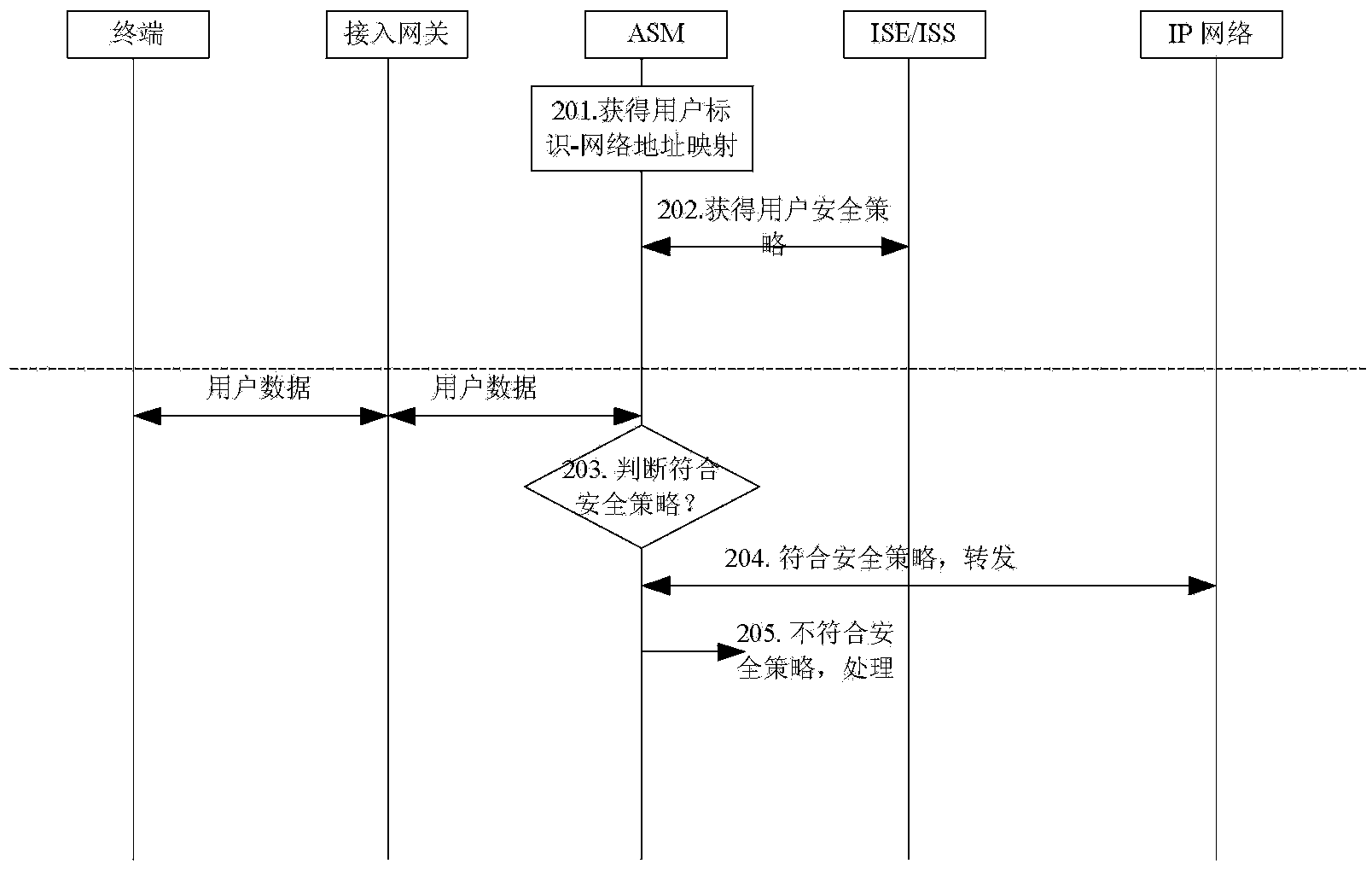
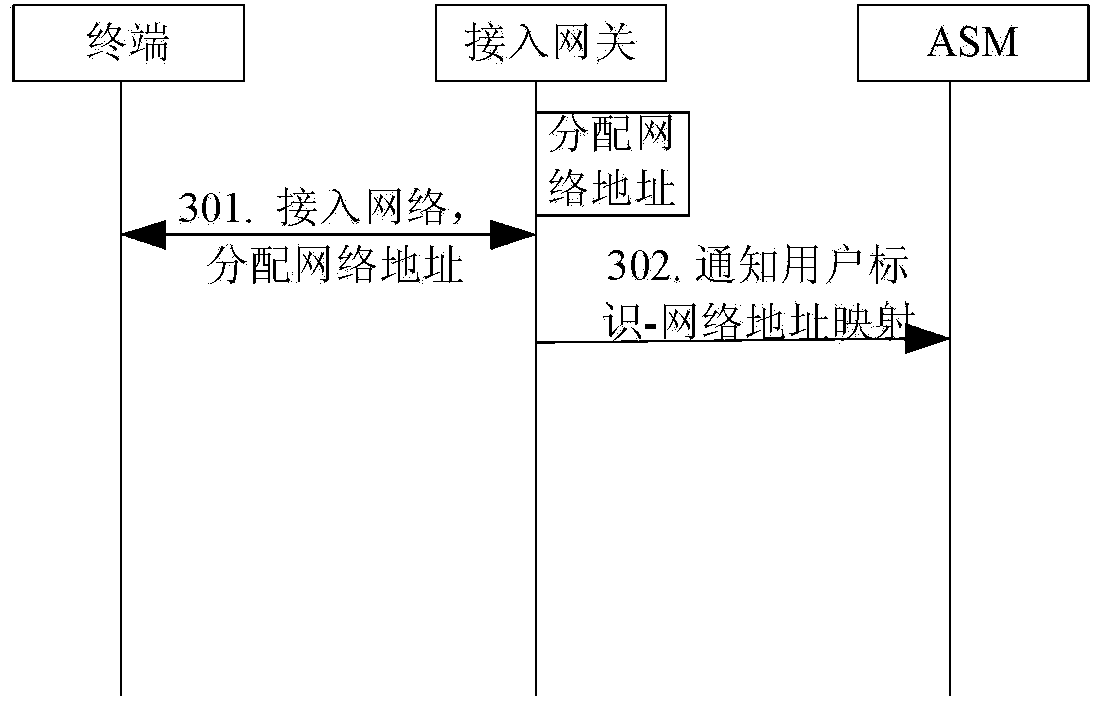
[0070] When a user accesses the network from a terminal, the network security monitoring system obtains the user's network address or user ID;
[0071] The network security monitoring system determines the user identity information corresponding to the user's network address or user ID, queries the user security policy of the user accessing the network according to the user identity information, and executes the security policy for the user.
[0072] The network security monitoring system involved in the above method can adopt the framework of the above embodiment 1, at least including an access security execution unit and a security policy engine unit, wherein:
[0073] Access to the security execution unit, obtain the network address or user ID of the user accessing the network, and send a user security policy query request carrying the user ID and / or network...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com