Data protecting method and device
A data protection and data technology, applied in the field of information security, can solve the problems of reducing the data viewing efficiency in the terminal and increasing the user operation path, so as to reduce the operation path and improve the reading efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
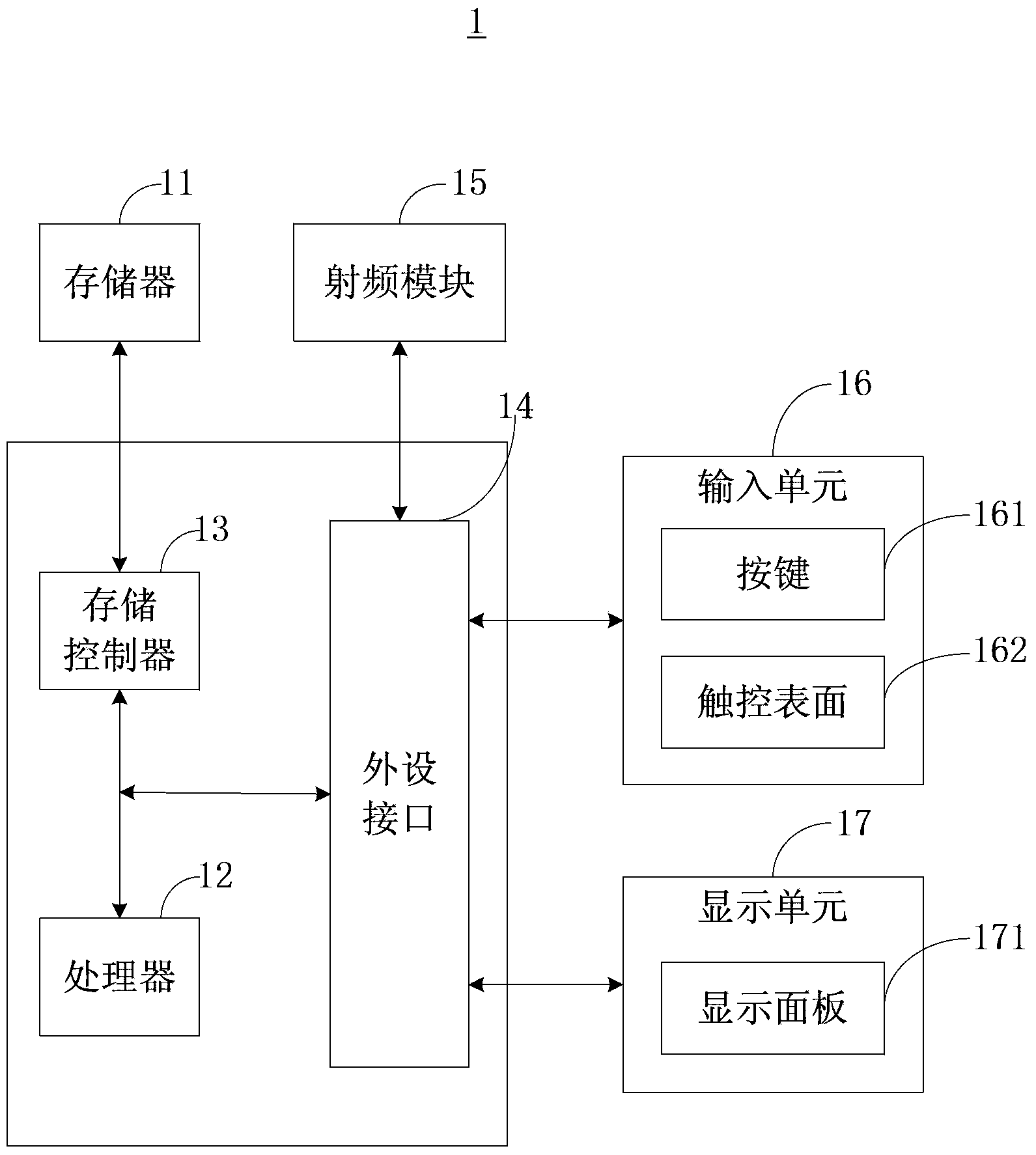
[0028] The first embodiment of the present invention provides a data protection method, which can be executed by the above-mentioned mobile terminal 1 and is used to protect data in the mobile terminal 1 . Specific examples of the mobile terminal 1 include but are not limited to handheld computers, mobile phones, personal digital assistants or other similar computing devices.
[0029] Below in conjunction with specific embodiment the above-mentioned data protection method is described in detail as follows:
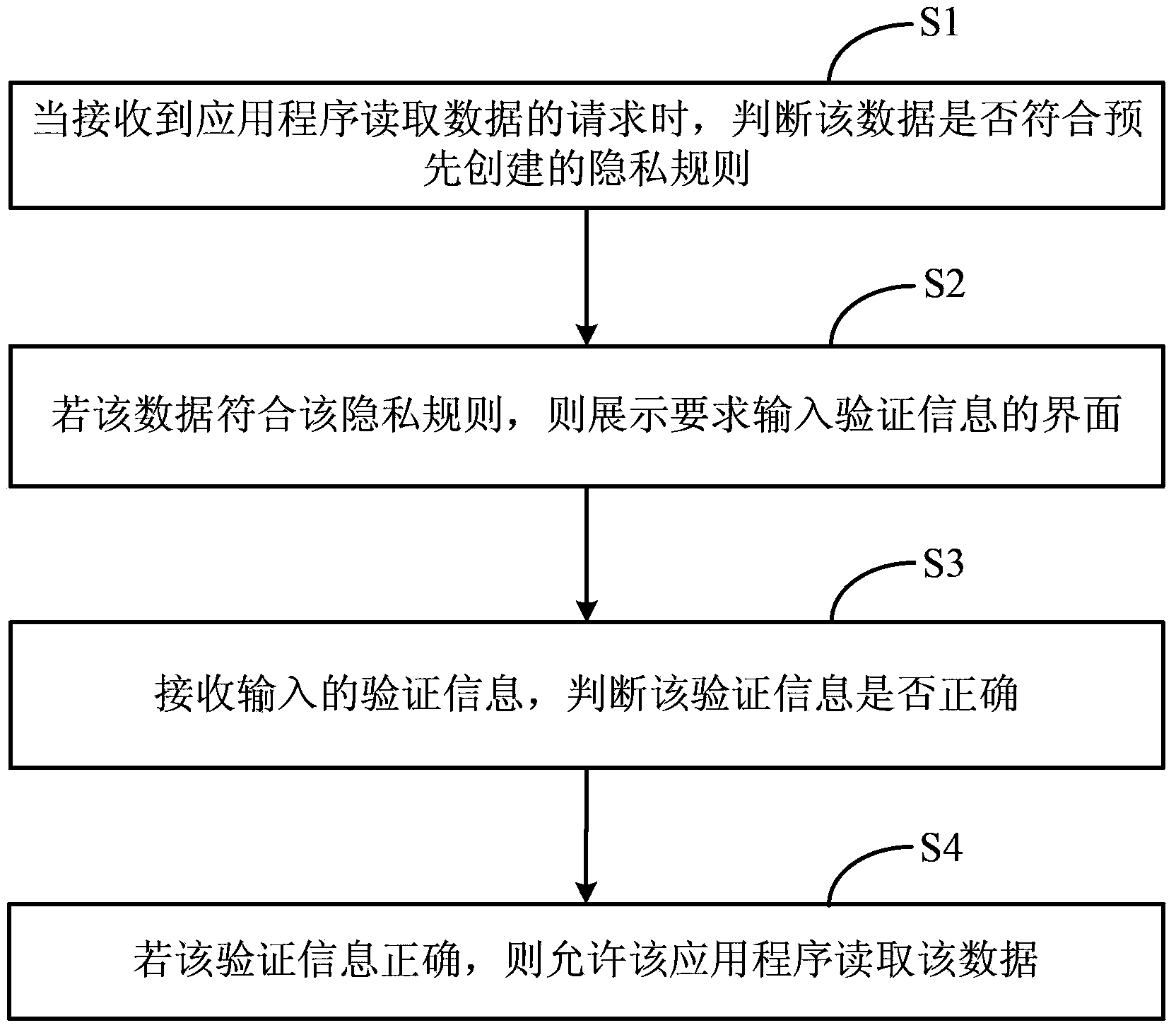
[0030] figure 2 A flow chart of the data protection method provided in the first embodiment, the data protection method includes the following steps:
[0031] Step S1, when receiving a request from an application program to read data, determine whether the data complies with a pre-created privacy rule;
[0032] Step S2, if the data complies with the privacy rule, display an interface requiring input of verification information;
[0033] Step S3, receiving the input verif...
no. 2 example
[0060] In order to improve the efficiency of judging whether the data conforms to the privacy rule in step S1 of the first embodiment, avoid checking the created privacy rules one by one every time the data needs to be read, so as to find the privacy rule that the data conforms to or demonstrate that the data does not comply with any privacy rules, see Image 6 As shown, the second embodiment of the present invention provides a data protection method, which, compared with the data protection method of the first embodiment, also includes before the step S1:
[0061] Step S1.1, when data input is received, judge whether the data complies with a certain privacy rule, if so, store the data, and set a flag corresponding to the privacy rule complied with for the data. For example, when an incoming call is received, it is judged whether the calling record of the calling party complies with a certain privacy rule, and if so, the information of the incoming call is stored, including th...
no. 3 example
[0064] According to the data protection method provided in the second embodiment to protect data, the user needs to input correct verification information to allow the application program to read the data, which can prevent people who do not have access to the data from accessing the data, but cannot prevent some users Unwanted applications, such as some malicious programs that steal user privacy, read this data.
[0065] In order to further solve the above problems and improve data security, please refer to Figure 7 , Figure 8 with Figure 9 As shown, the third embodiment of the present invention provides a data protection method. Compared with the data protection method in the second embodiment, before the step of allowing the application to read the data in step S4, it further includes:
[0066] Step S4.1, judging whether the application program has the read permission of the type to which the data belongs. If not, end the process, if so, allow the application to read ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com