A real-time big data privacy protection method based on symmetric encryption
A privacy protection and symmetric encryption technology, applied in the field of information security, can solve the problems of ignoring the importance of data change trends and the inefficiency of big data protection, etc., to reduce the cost of privacy protection, resist attacks without background knowledge, and simplify operations Efficient effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
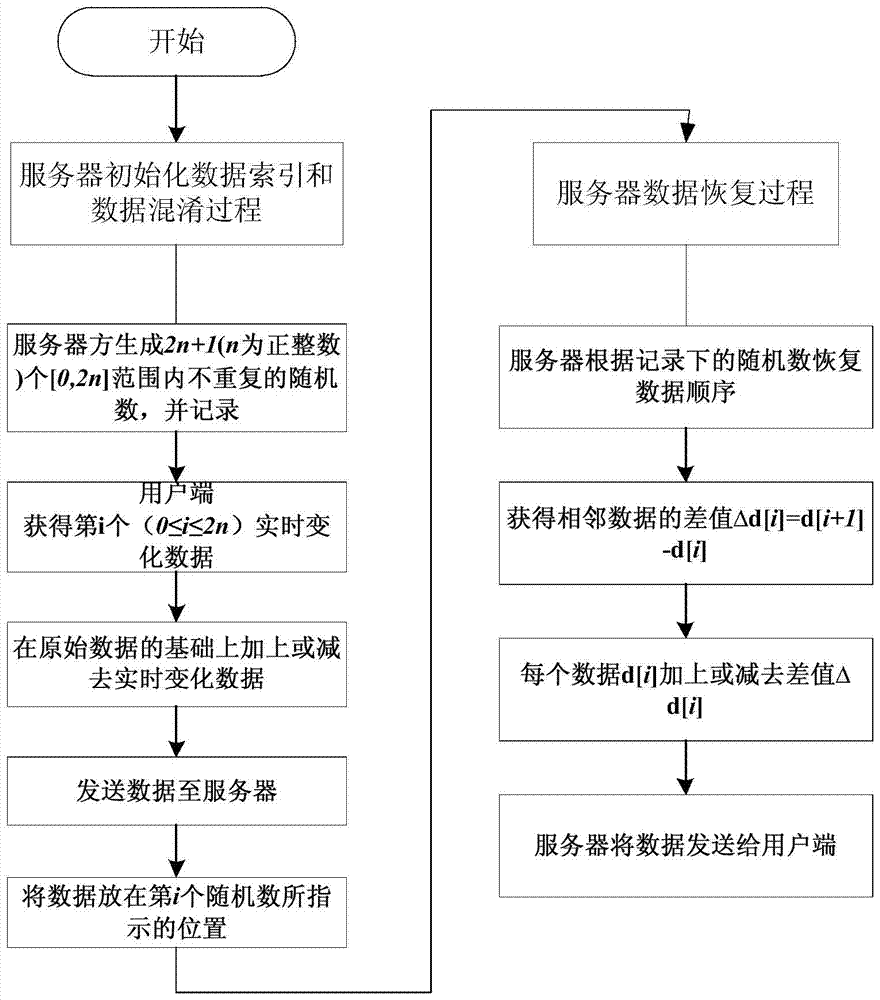
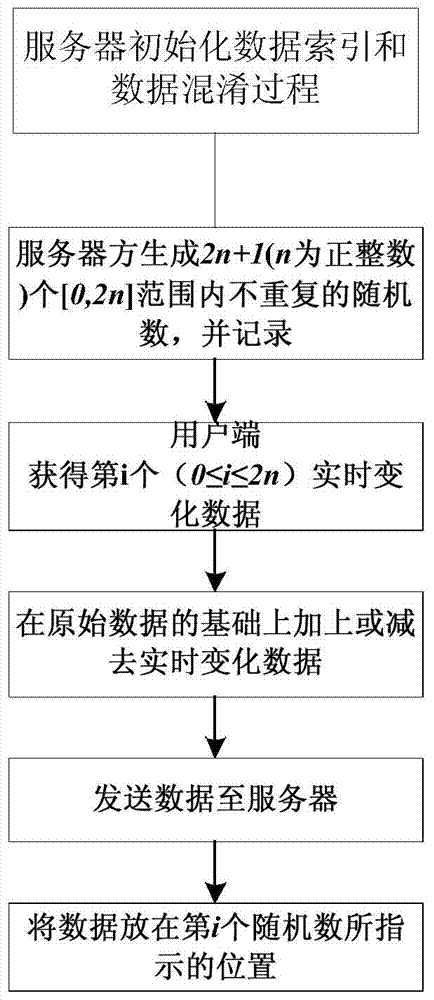
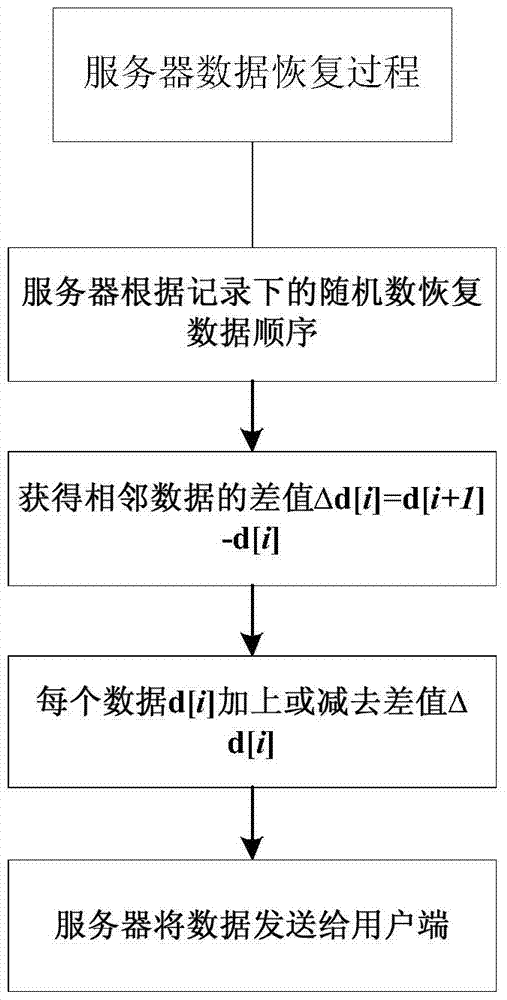
[0073] The computational overhead of this method can be divided into two parts. The first part is the server's overhead of initializing data indexes and confusing data; the second part is mainly the server's overhead of restoring data order and real data values. The method of this embodiment completes the comparative simulation experiment with the existing symmetric encryption method DES on a machine with a Corei3 processor and a main frequency of 2.53 GHz in C language. The simulation comparison experiment uses a file to input 100,000 integer data, and compares the time overhead of encryption and decryption of the two methods. The average test results are as follows:
[0074] This embodiment DES Encryption time (ms) 102.8 1577.3 Decryption time (ms) 91.6 1582.4
[0075] It can be seen from the above results that the encryption and decryption time overhead of this embodiment is far superior to that of the DES symmetric encryption algorithm, the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com