A trusted verification method based on dnssec and dane protocol
A verification method and a credible technology, applied in the network field, can solve problems such as forged product label barcodes and counterfeit label deception, and achieve the effect of preventing abuse
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
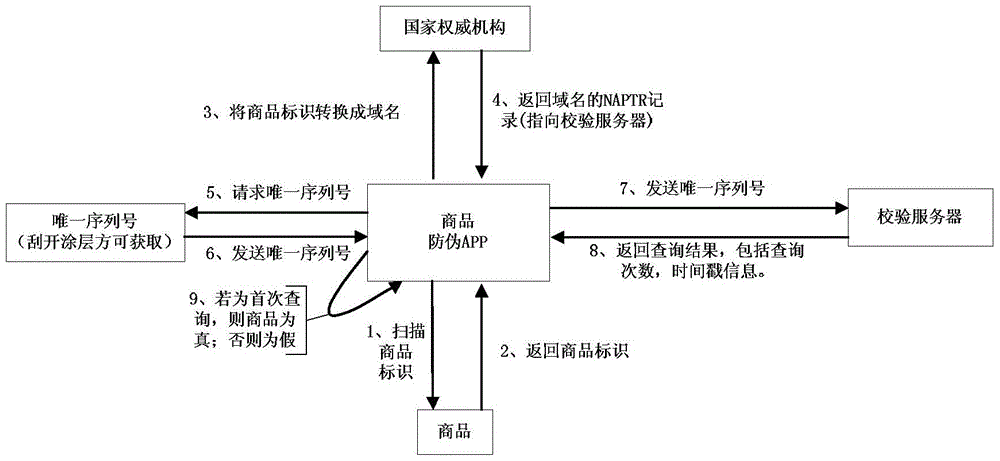
[0053] The following three specific examples are used to illustrate the content of the invention. Let's first introduce an example of dealer anti-counterfeiting. The anti-counterfeiting process is as follows: Figure 4 As shown, it can be divided into two stages: registration and query. In the registration stage, the dealer generates a pair of public and private keys, and submits the public key and the dealer's registration number to the national authority (here, it is assumed to be "National Internet of Things Identification Management Public Service Platform", the same below), The online identity management public service platform creates a TLSA resource record for the dealer, which contains the dealer's public key information. In the inquiry stage, the dealer anti-counterfeiting APP first scans the dealer logo, and converts the obtained dealer logo (here 5936) into a domain name (here 5936.gsh.niot.cn), and then reports to the National Internet of Things Logo Management T...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com