WPKI security monitoring and control method and system based on mobile terminal
A security monitoring system and mobile terminal technology, applied in security devices, electrical components, wireless communications, etc., can solve the problems that users cannot understand detailed information, and it is inconvenient to know monitoring information in time, so as to achieve the effect of ensuring security and confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0022] A schematic diagram of the principle of a mobile terminal-based WPKI security monitoring method provided in this embodiment is as follows figure 1 As shown, the specific processing flow diagram is shown in figure 2 As shown, the following processing steps are included:
[0023] Step 21, the user sends a connection request to the security monitoring system through the mobile terminal.
[0024] The user sends a connection request to the security monitoring system through the mobile terminal according to the user's digital certificate. The connection request carries the digital certificate information of the user terminal, including digital certificate DN (Distinguished Name, identification name), validity period, extension options, etc.
[0025] The aforementioned mobile terminal may be a mobile smart terminal.
[0026] Step 22: After receiving the connection request, the security monitoring system obtains the digital certificate information of the user terminal, and s...
Embodiment 2
[0037] The schematic diagram of the processing flow of another mobile terminal-based WPKI security monitoring method provided in this embodiment is as follows: image 3 As shown, the following processing steps are included:
[0038] Step 31, the security monitoring system monitors the operation platform and the application server, and finds that there is alarm information that needs to be notified to the administrator user.
[0039] The security monitoring system collects alarm information, converts the alarm information into a report form, and obtains an alarm information report. The above-mentioned security monitoring system queries the information of the administrator who needs to be notified at the same time;
[0040] The security monitoring system finds the mobile terminal of the administrator user through the mobile network according to the mobile phone number of the administrator user;
[0041] Step 32, the security monitoring system sends a connection request and a u...
Embodiment 3
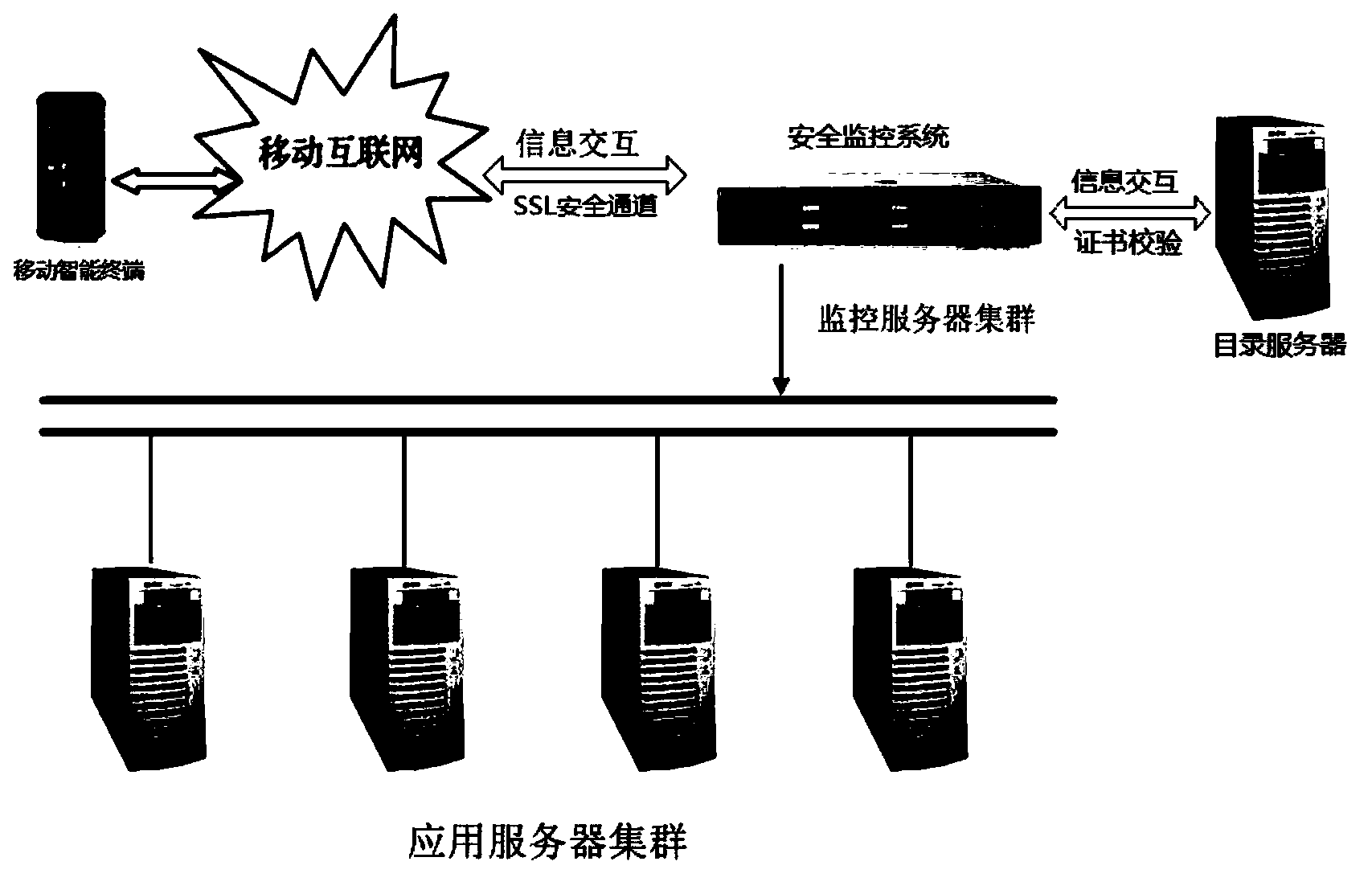
[0049] A schematic structural diagram of a mobile terminal-based WPKI security monitoring system provided in this embodiment is as follows Figure 4 As shown, the following modules are included:
[0050] The user's mobile terminal 41 is used to send a connection request to the security monitoring system, the connection request carries the digital certificate information of the user terminal, and the digital certificate is used to establish an SSL connection channel with the security monitoring system, through which the SSL connection The channel sends an operation query request to the security monitoring system;
[0051] The security monitoring system 42 verifies the digital certificate of the user terminal through the directory server. After the verification is passed, the security monitoring system returns a connection response to the mobile terminal, and returns a connection response to the mobile terminal through the SSL connection channel. information report.
[0052] F...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com