Leaky cable perimeter intrusion detection system
A detection system and technology for leaking cables, applied in the field of radio detection, can solve the problems of high use cost, low anti-interference ability, complicated installation and manufacturing, etc., and achieve low false alarm rate and false alarm rate, strong anti-interference ability, and positioning accuracy. high effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
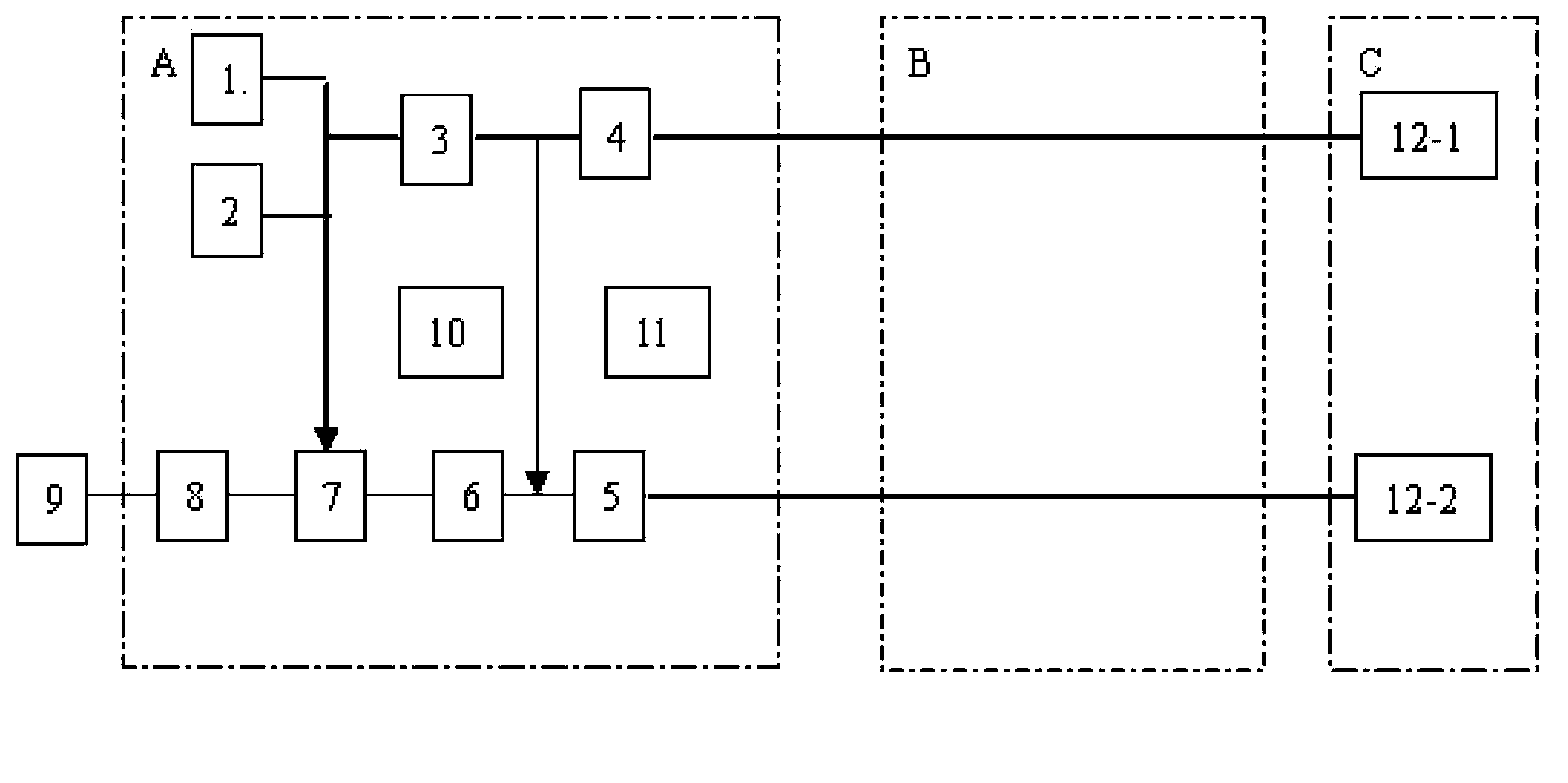
[0011] The present invention will be further described below in conjunction with the accompanying drawings.
[0012] figure 1 It is the leaky cable perimeter intrusion detection system according to the present invention. The system is composed of three parts: a detection system host A, a leaky cable module B and a terminal module C. The detection system host A is the center of the leaky cable perimeter intrusion detection system. processor. The detection system host A includes many small modules, which are: carrier signal generation module 1, pseudo-random code generation module 2, transmission signal synthesis module 3, signal transmission module 4, signal reception module 5, signal processing module 6, information Processing module 7 , alarm module 8 , display module 9 , power supply module 10 and lightning protection module 11 . The leaky cable module B is provided with two leaky cables, which are a transmitting cable and a receiving cable respectively. Two matching resi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com