Virtual machine access control system and method based on cloud computing environment
A cloud computing environment and access control technology, applied in the protection of internal/peripheral computer components, transmission systems, electrical components, etc., can solve problems such as system management program loopholes, and achieve the effect of isolation and crash prevention
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
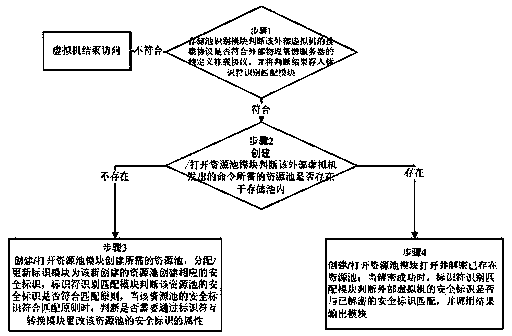
[0035] The present invention will be further elaborated below by describing a preferred specific embodiment in detail in conjunction with the accompanying drawings.
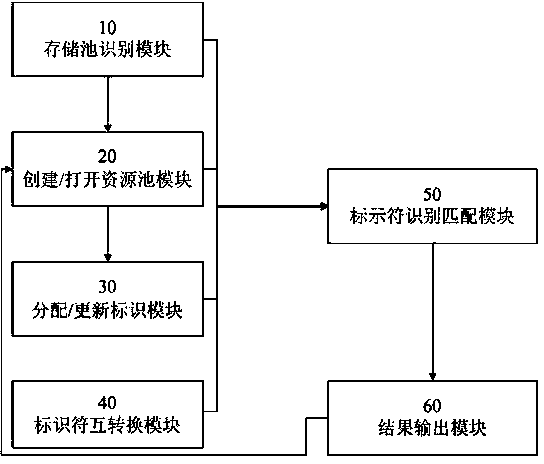
[0036] Such as figure 1 As shown, a virtual machine access control system based on a cloud computing environment, the control system includes: an identifier identification matching module 50, and a storage pool identification module 10 connected to it, a creation / opening resource pool module 20, an allocation / update identification Module 30 , identifier conversion module 40 and result output module 60 .
[0037] The above-mentioned storage pool identification module 10 , creation / opening resource pool module 20 , allocation / update identification module 30 , identifier conversion module 40 are sequentially connected; the above-mentioned result output module 60 is connected with the above-mentioned creation / opening resource pool module 20 .
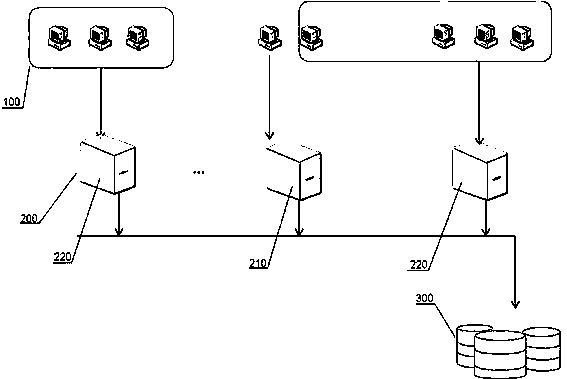
[0038] Such as figure 2 As shown, when multiple virtual machines based...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com