A copyright authentication method for gis vector data based on fcm clustering features
A technology for copyright authentication and vector data, applied in the field of geographic information security, which can solve the problems of algorithm robustness difficult to meet copyright protection, distortion, data interference, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] Further detailed description will be given below in conjunction with the accompanying drawings and embodiments.
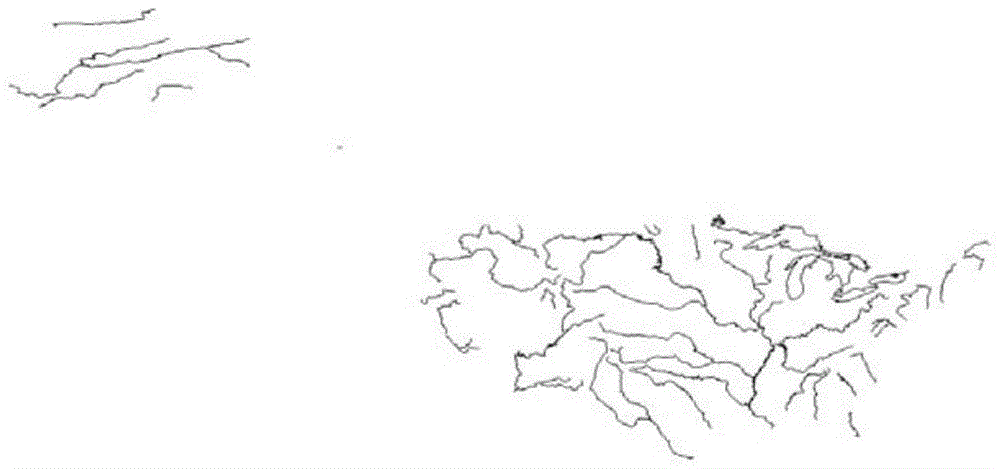
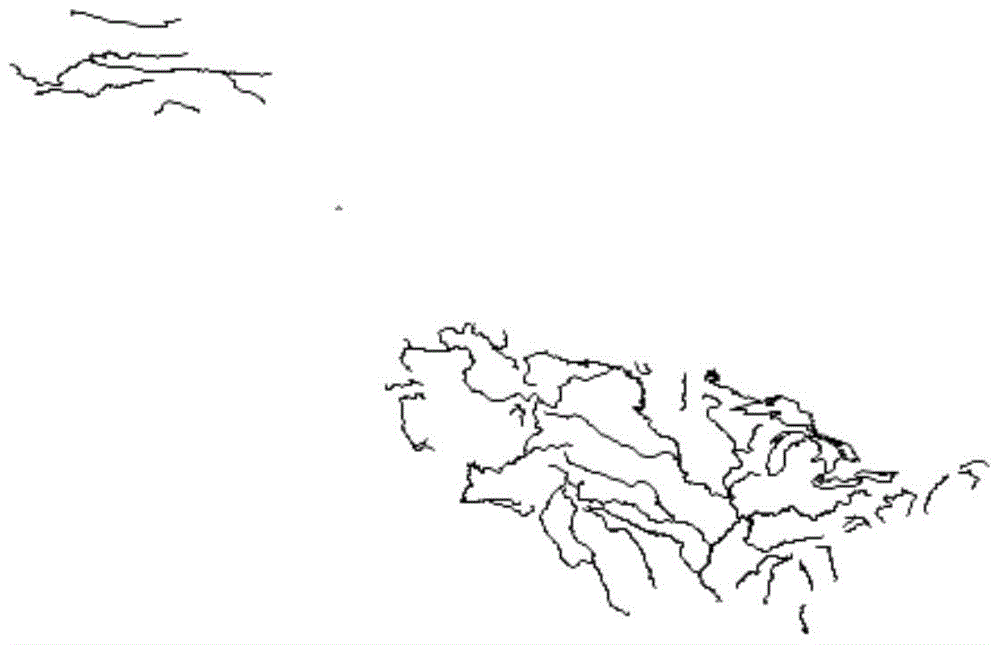
[0037] This example selects a typical shp surface layer data, and further describes the present invention in detail for the entire process of data reading, copyright mark generation, and copyright mark authentication. This embodiment selects the water system linear layer data of the United States (such as figure 1 ) as experimental data, figure 2 It is the data generated after the experimental data is subjected to the rotation attack. The key value is "10010101", and the recognition threshold is 0.85.
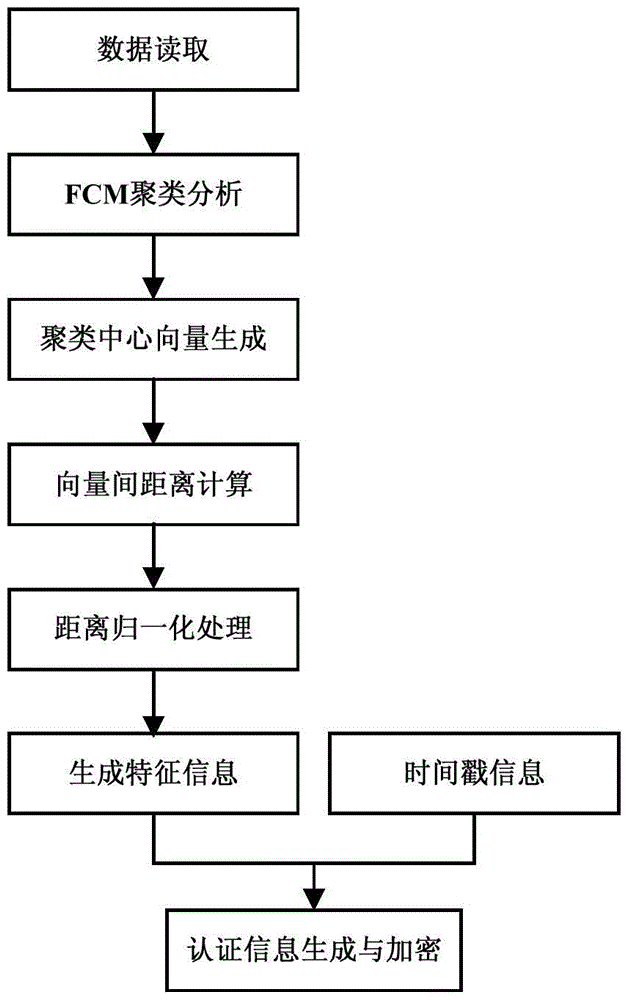
[0038] (1) Copyright mark generation process.
[0039] Step 1: Set the number of clusters c=8 and the weight parameter m=2.
[0040] Step 2: Open the US water system line layer file F; read the horizontal and vertical coordinate information of each element node in the file into the two-dimensional array D, and the number of nodes in this embodiment is 64...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com