Touch keyword using national cipher SM1 encryption chip and encryption method thereof
An encryption chip, touch keyboard technology, applied in the input/output of user/computer interaction, user identity/authority verification, protection of internal/peripheral computer components, etc., can solve problems such as encryption products that have not yet appeared, and achieve resistance to data replay The effect of attacking, avoiding leakage, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] In order to fully understand the technical content of the present invention, the technical solutions of the present invention will be further introduced and illustrated below in conjunction with specific examples, but not limited thereto.
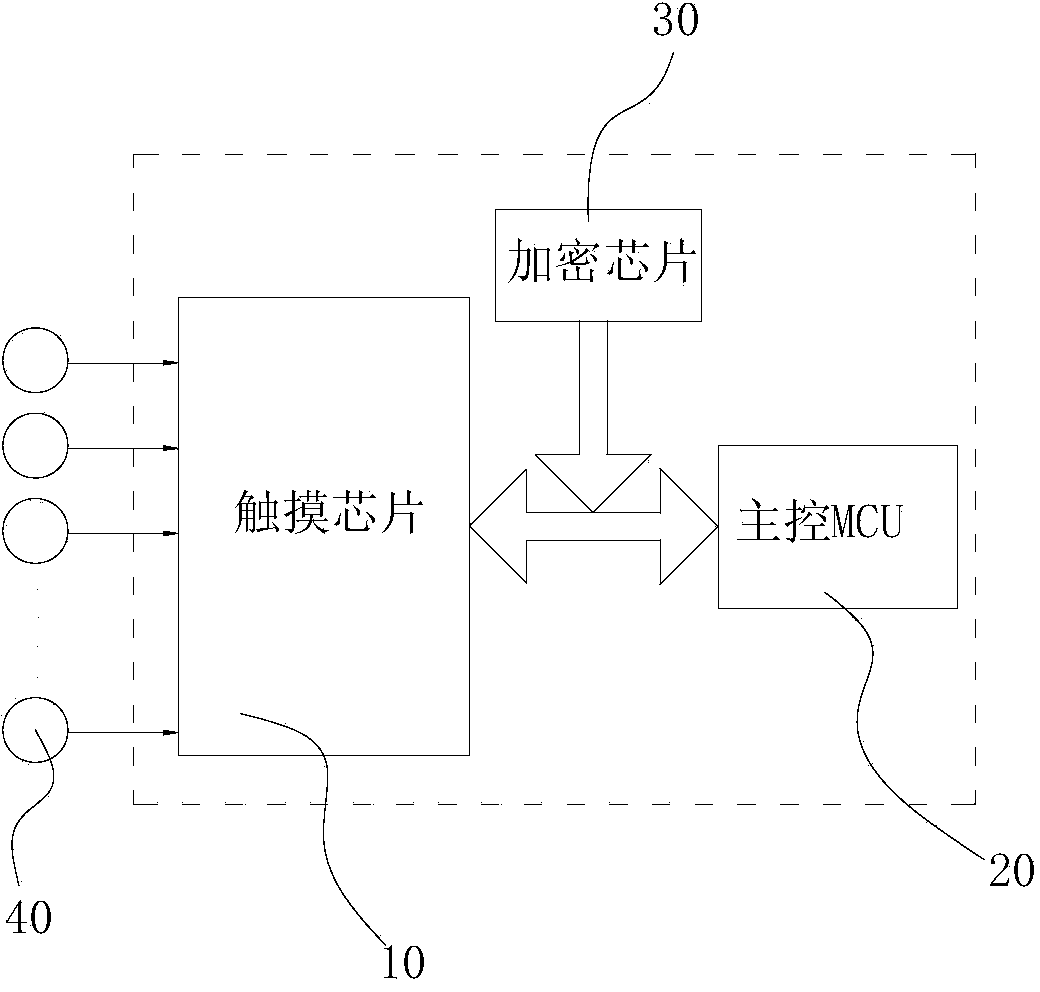
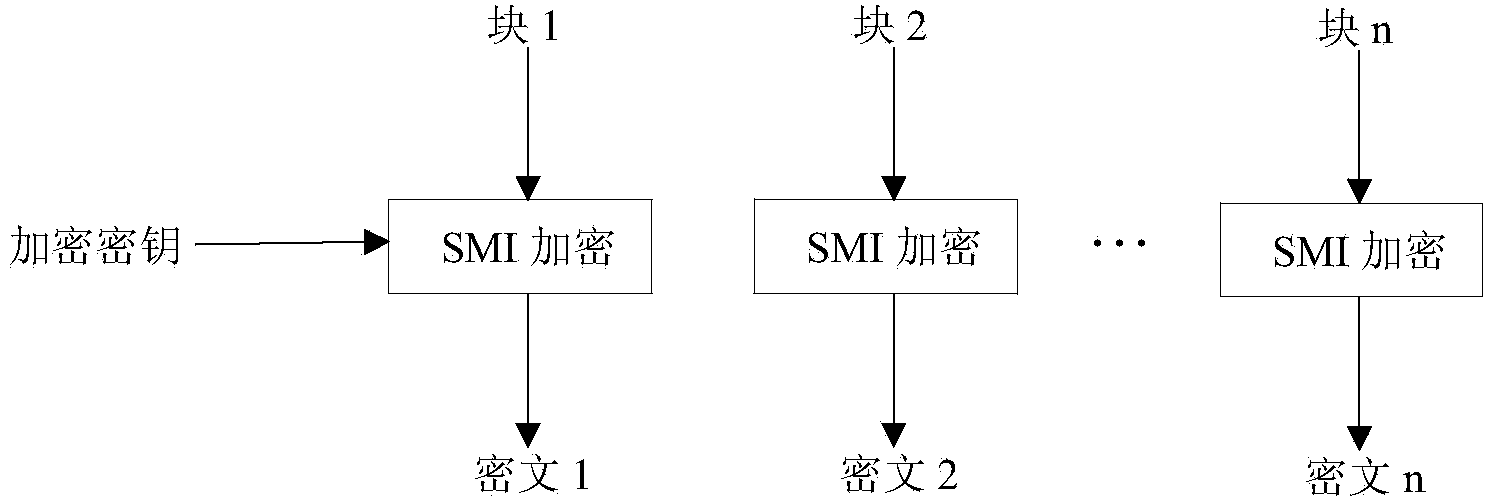
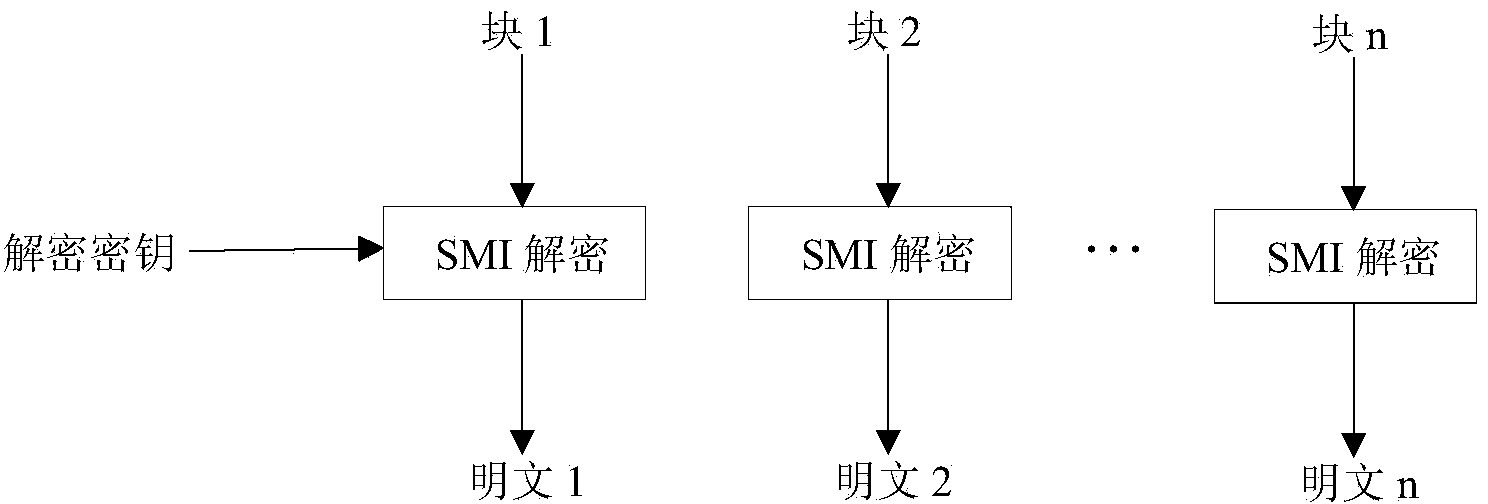
[0042] Such as Figure 1-Figure 2 The present invention shown is a touch keyboard using a national secret SM1 encryption chip, including a touch chip 10, a main control MCU 20 and a data wire for connecting the main control MCU 20 and the touch chip 10, and the data wire is a two-wire serial bus The I2C bus, the I2C bus is also connected with the national secret SM1 encryption chip 30. The touch chip 10 is also connected with a key sensor pad 40 . Wherein, the collection data packet collected by the touch chip 10 is encrypted by the encryption chip 30 to generate a ciphertext data packet, which is transmitted to the main control MCU 20, and the ciphertext data packet received by the main control MCU is decrypted by the encryption ch...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com