Information security audit system and method thereof
A technology of information security and management and control system, applied in the field of information security auditing, can solve problems such as inability to efficiently control, single weakness or important asset evaluation, and inability to be organized or provided by enterprises
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
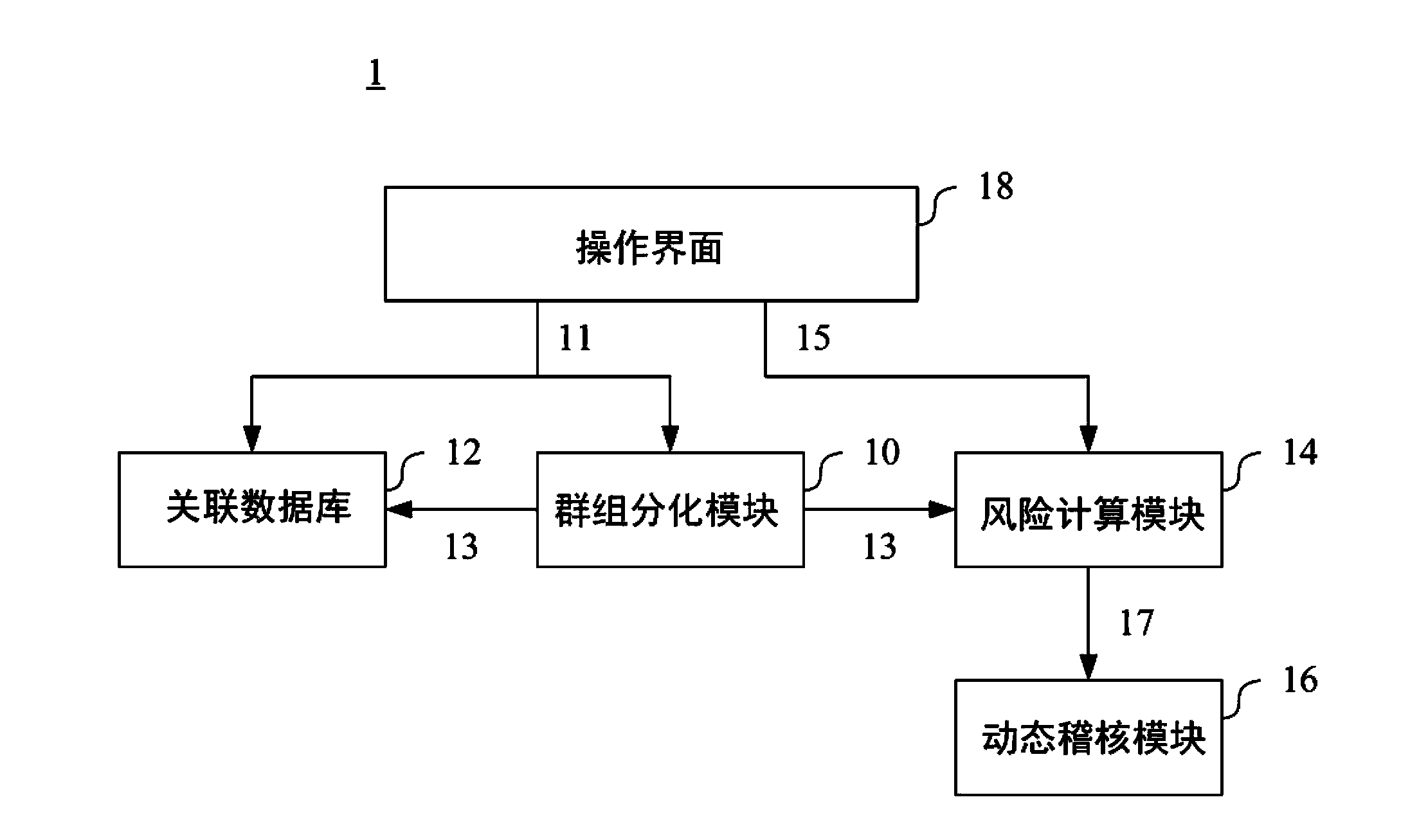
[0039] Please refer to figure 1 . figure 1 It is a block diagram of an information security audit management and control system 1 in an embodiment of the present invention. The information security audit management and control system 1 includes: a group differentiation module 10 , an associated database 12 , a risk calculation module 14 , a dynamic audit module 16 and an operation interface 18 .
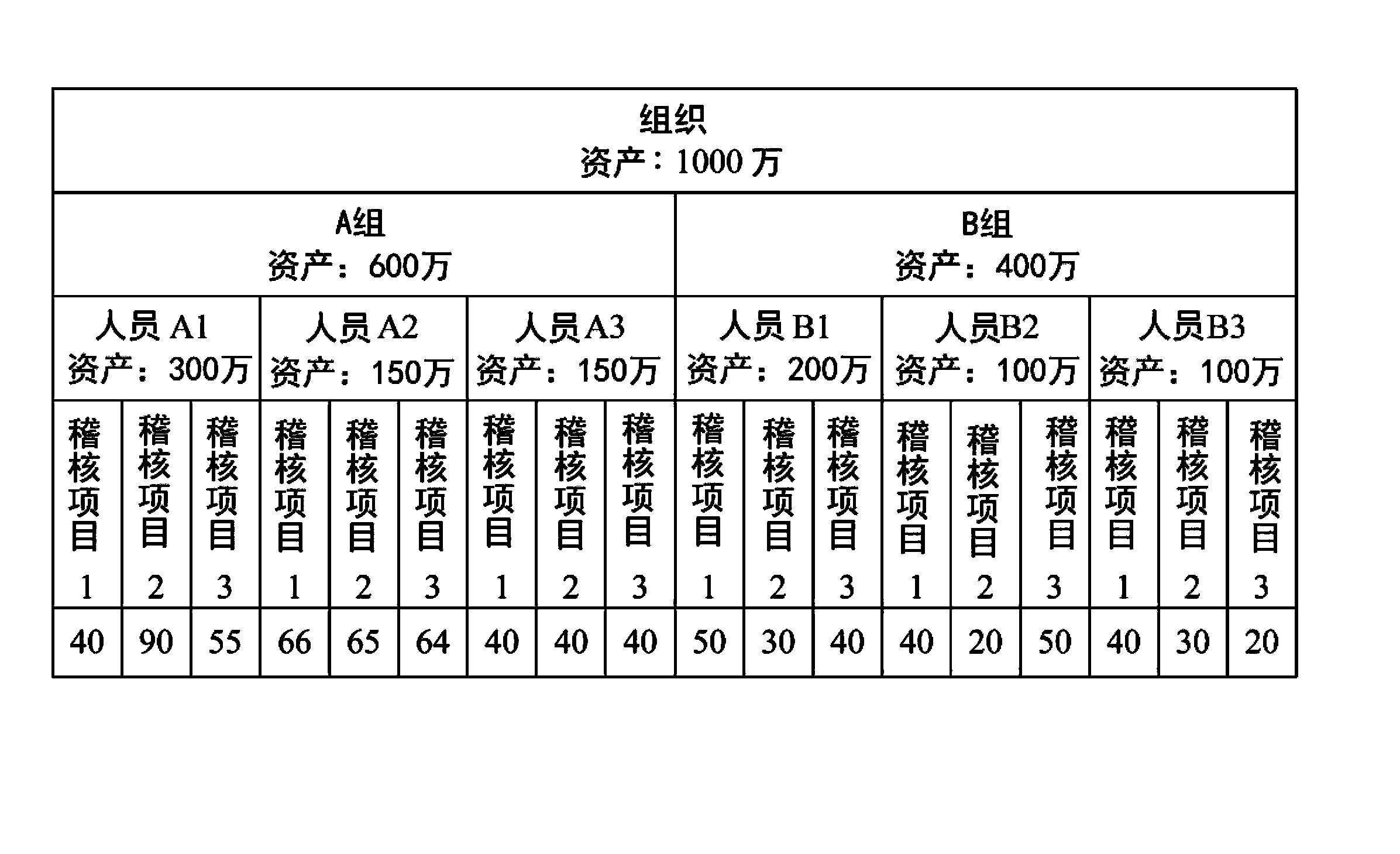
[0040] The operation interface 18 can be used for the user to input the organization information 11 of an organization, including the structure levels and at least one feature corresponding to each of the members of the organization. Among them, the word "organization" can be, for example but not limited to, a company, an association or an institution, and the structural level of its members can be grouped from members of high structural level (such as business groups, departments, etc.) to members of low structural level (e.g. group, individual, etc.). Moreover, members of an org...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com