Method and device for storing and transmitting information using digital images
A digital image and information transmission technology, applied in the field of information transmission, can solve the problem of low security in the application of information hiding technology, achieve the effect of effective transmission and storage of information, and solve the problem of forgery
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0020] The method for storing and transmitting information by using a digital image in the embodiment of the present invention includes two processes of embedding information in the digital image and extracting information from the digital image. The foregoing information is usually secret information, and the following uses secret information as an example to illustrate the embodiments of the present invention.
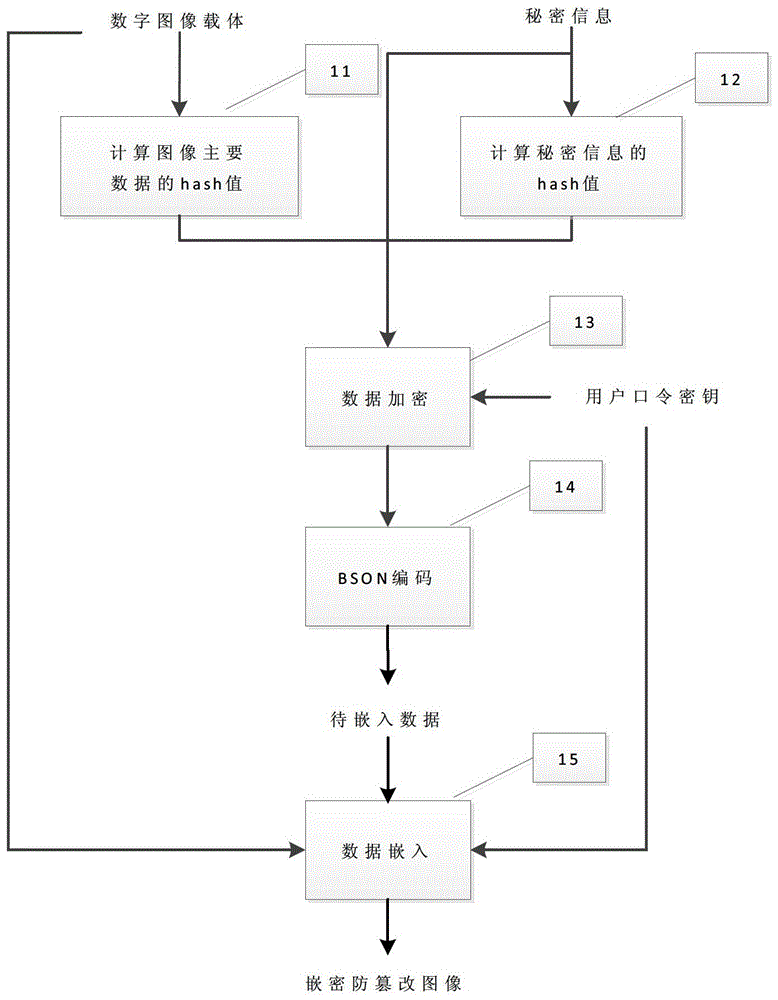
[0021] The specific processing flow of a method for embedding secret information in a digital image provided by this embodiment is as follows figure 1 As shown, the following processing steps are included:
[0022] Step 11, the embodiment of the present invention selects a digital image as a digital carrier embedded with secret information.
[0023] A color digital image can be represented by a three-dimensional grayscale image. For example, a color digital image can be represented in RGB three-dimensional space, and any dimension can be considered as a grayscale im...
Embodiment 2
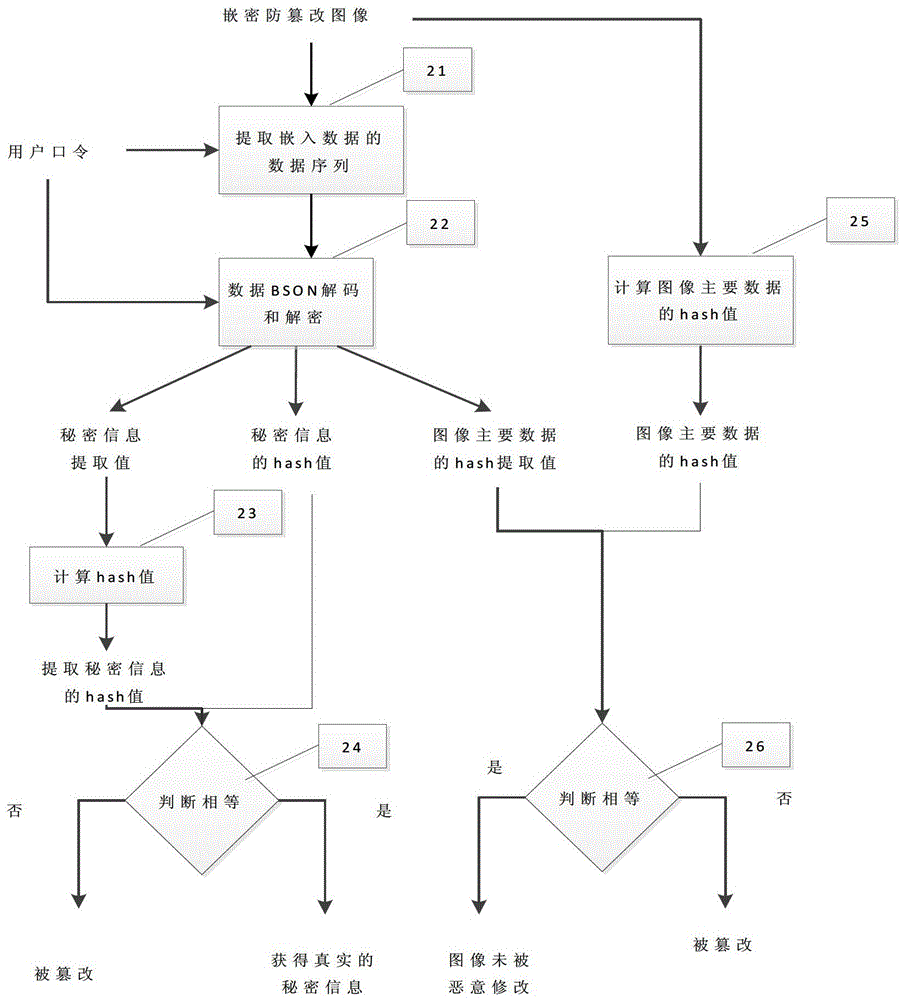
[0044] The specific processing flow of a method for extracting secret information from digital images provided by this embodiment is as follows: figure 2 As shown, the following processing steps are included:
[0045] Step 21. After receiving the pixel value sequence of the above-mentioned digital image containing secret information, the receiver extracts the first 4 bits of the embedded data sequence and calculates the length of the embedded data sequence according to the user password, and converts the above user password into and calculates The obtained embedded data sequence is a binary password sequence consisting of 0 and 1 bits of the same length, and then, according to the specific numbers (ie 0 or 1) in the above password sequence, determine the 8 of each pixel value in the above pixel value sequence in turn. The location and specific number of embedded secret information in a binary number of bits.
[0046]For example, if the first number in the above password sequ...
Embodiment 3
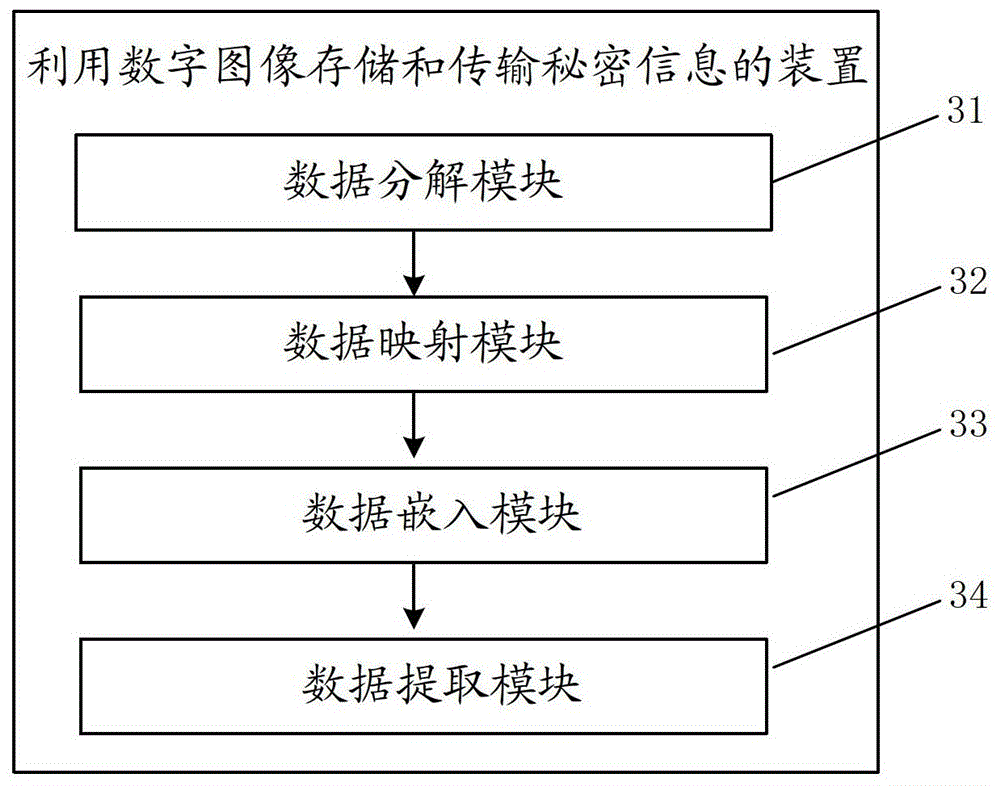
[0055] This embodiment provides a device for storing and transmitting secret information using digital images, and its specific structure is as follows: image 3 As shown, the following modules are included:
[0056] The data decomposition module 31 is used to decompose the digital image data into a sequence of pixel values, convert each pixel value in the sequence of pixel values into a binary number with a set number of bits, and convert the secret information into a binary number to be embedded. data sequence;
[0057] A data mapping module 32, configured to correspond to the numbers to be embedded in the data sequence and the pixel values in the pixel value sequence according to the set data mapping rules;
[0058] The data embedding module 33 is configured to embed each number in the data sequence to be embedded into a binary number corresponding to a corresponding pixel value according to a set data embedding rule.
[0059] Specifically, the data decomposition modu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com