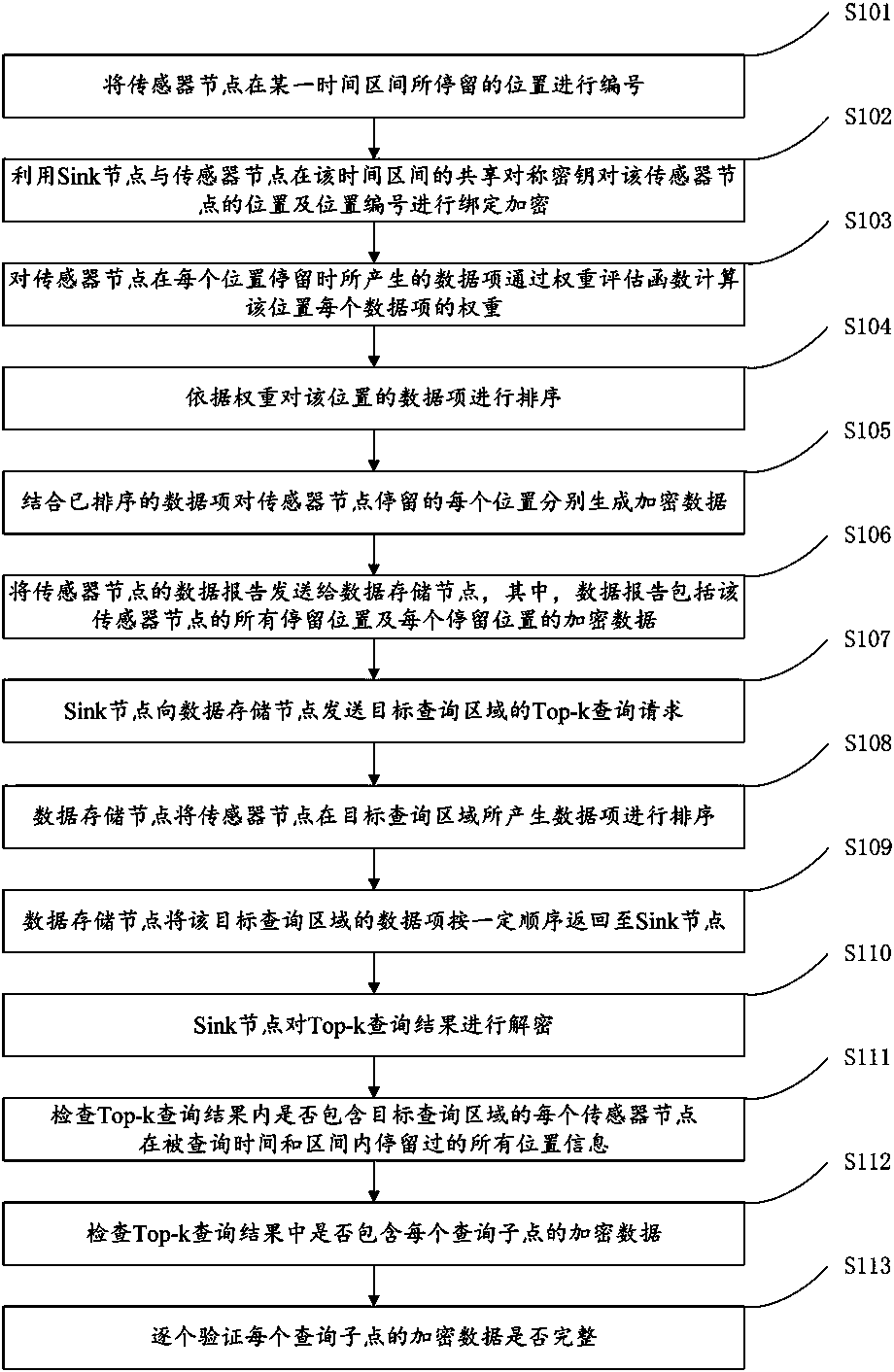
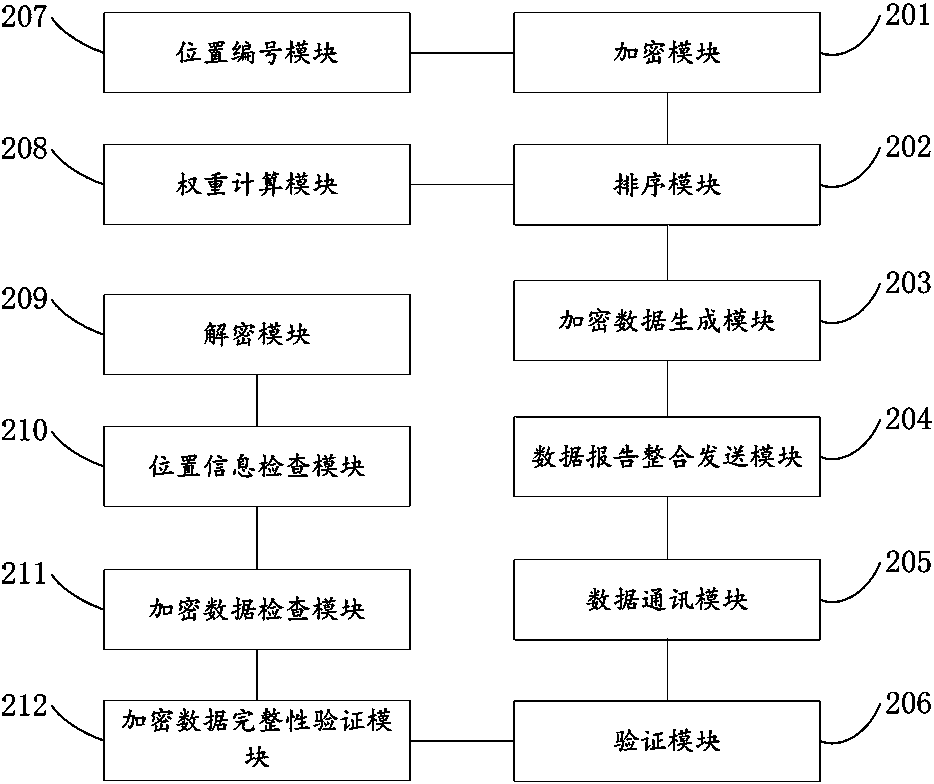
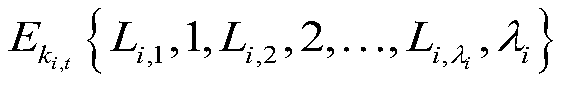Time-space top-k query data integrity protection method and device based on tmwsns
A technology for integrity protection and data query, applied in security devices, database query, structured data retrieval, etc., can solve the problems of redundant information for security verification, increase of additional network communication overhead, and failure to prevent mutual substitution, etc. achieve high energy efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
[0079] 1. Network model description of TMWSNs:
[0080] The network model of TMWSNs is divided into two layers, L1 and L2. The L1 layer is a multi-hop self-organizing network composed of movable sensor nodes with limited resources and a short communication radius, and the L2 layer is a Mesh network composed of multiple data storage nodes with abundant resources and a long communication radius. The entire monitored area is divided into M units, and a data storage node H is deployed in any unit c (1≤c≤M) and N sensorable nodes {S 1,c ,S 2,c ,S 3,c ,...,S N-1,c ,S N,c} (which contains some or all of the movable sensor nodes). S i,c (1≤i≤N, 1≤c≤M) can communicate with H through single-hop or multi-hop c Carry out communication, and be able to move to the target position according to the application needs, stop moving after reaching the target position and start monitoring the target thing. This paper assumes that S i,c move only within its owning cell, and assume that S ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com