Method and device for inquiring direct connection communication target terminal information
A target terminal and direct-connection communication technology, which is applied in the field of inquiry methods and devices for direct-connection communication target terminal information, and can solve problems such as the list is not saved
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
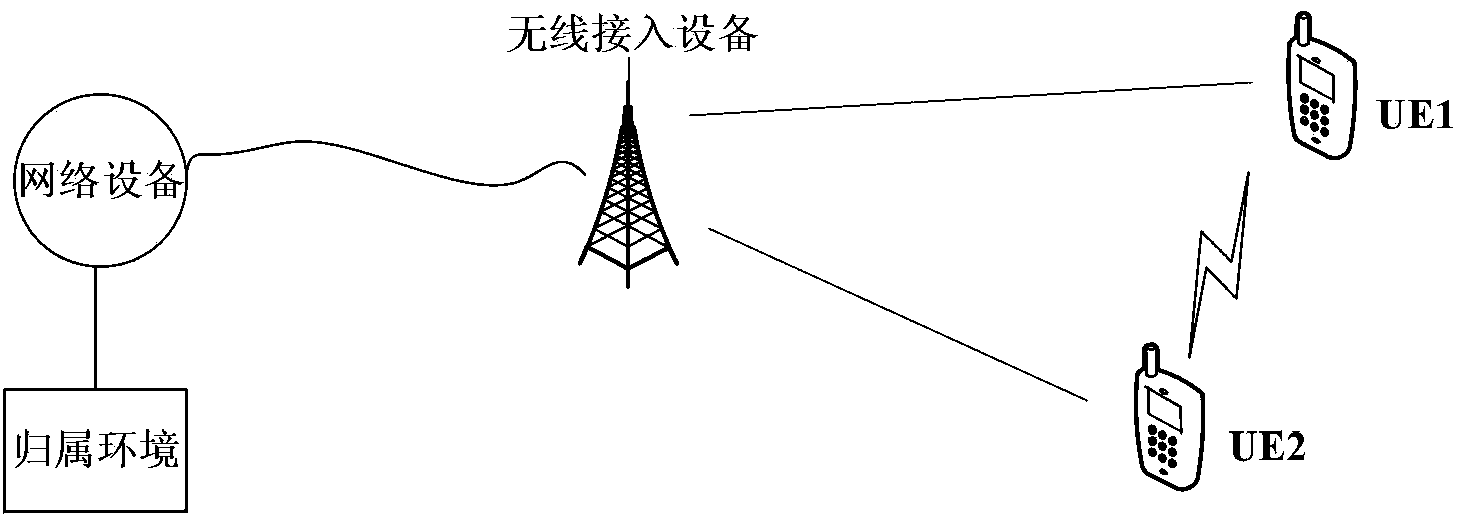
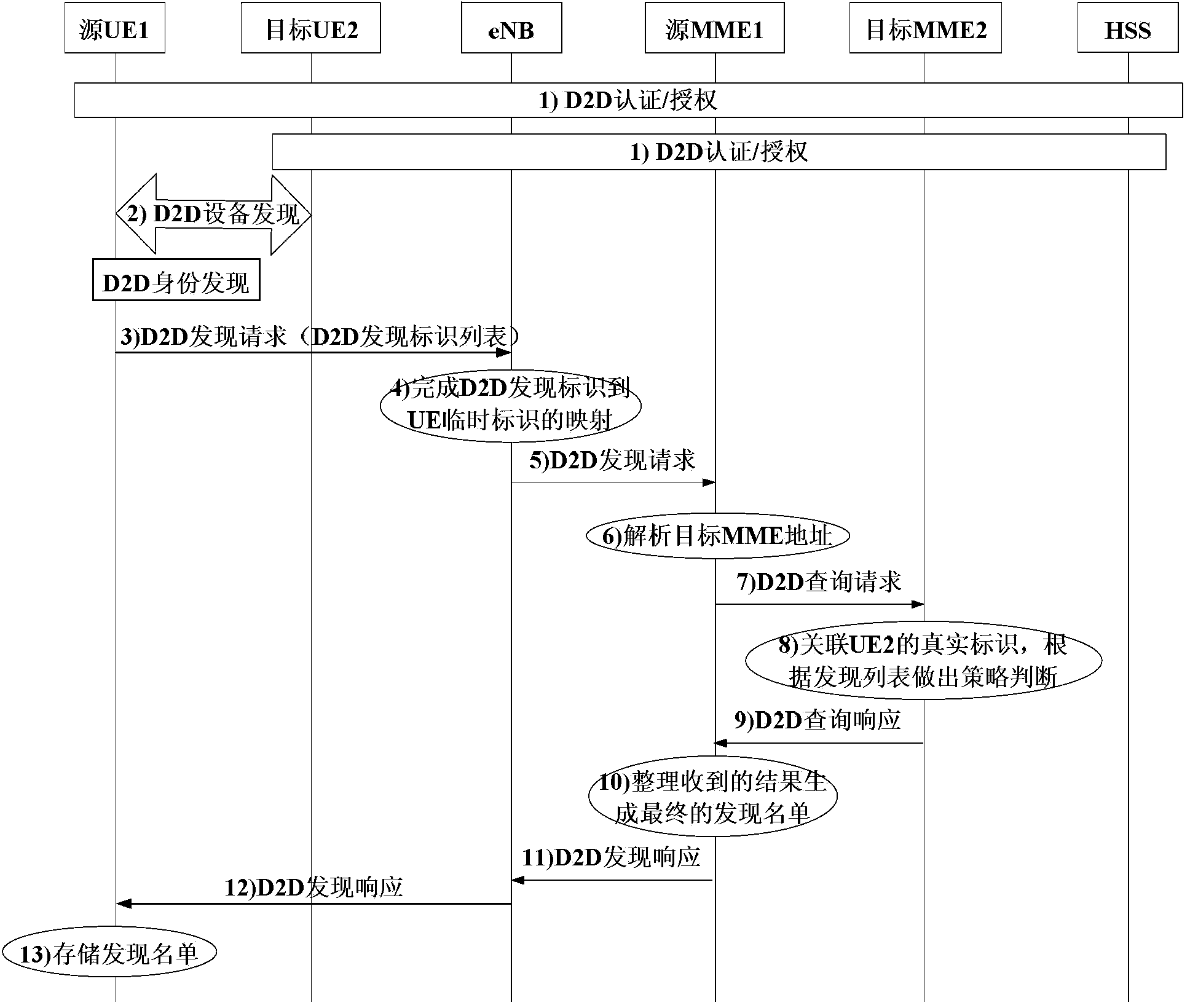
[0083] Such as figure 2 As shown, this embodiment shows a D2D discovery process in which the source UE1 discovers the target UE when the UE1 having the D2D function and the target UE are located in the same eNB range but under different MMEs. For simplicity, the schematic diagram only shows a scenario where there is one target UE. Wherein, the source UE1 is located under the management of the source MME1, and the target UE2 is located under the management of the target MME2. In this process, both the source UE1 and the target UE2 use the unique D2D discovery identifier allocated by the eNB to identify their D2D devices. The specific steps of the process are described as follows:
[0084] 1) When UE1 and UE2 start D2D services, UE1 and UE2 respectively perform D2D authentication and authorization with the network. In this process, the eNB assigns a unique D2D discovery ID to each UE authorized for D2D services. Optionally, the eNB reports the D2D discovery ID to the MME. ...
Embodiment 2
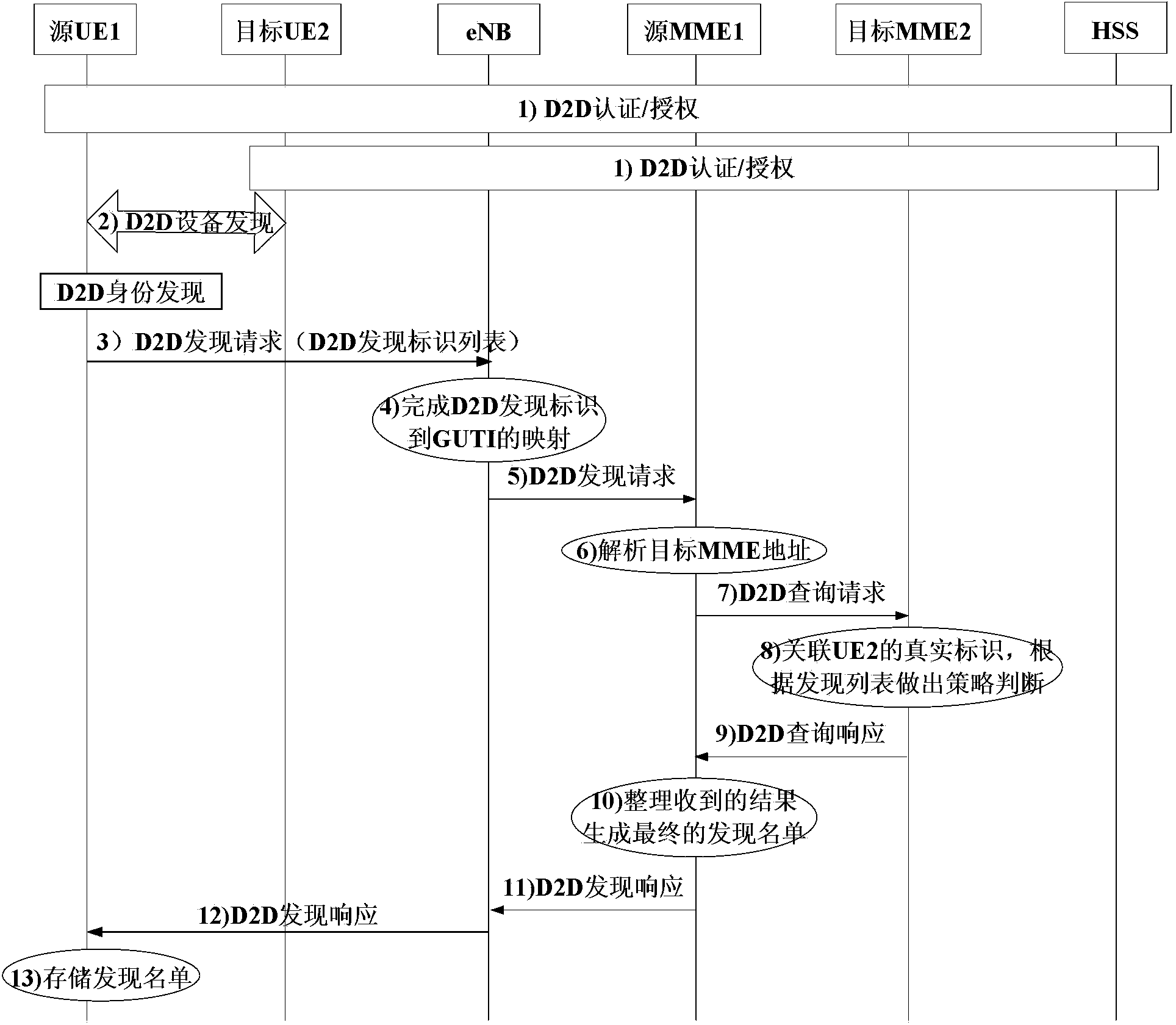
[0108] Such as image 3 As shown, this embodiment shows the D2D discovery process of the source UE1 discovering the target UE when the UE1 capable of D2D function and the target UE are located in the same eNB range but under different MMEs. For simplicity, the schematic diagram only shows a scenario where there is one target UE. Wherein, the source UE1 is located under the management of the source MME1, and the target UE2 is located under the management of the target MME2. In this process, both the source UE1 and the target UE2 use the unique D2D discovery identifier allocated by the eNB to identify their D2D devices. The specific steps of the process are described as follows:
[0109] 1)-2) are the same as step 1-3) in Example 1.
[0110] 4) After receiving the D2D discovery request message sent by the source UE1, the eNB associates with the temporary identity GUTI of the discovered target UE according to the D2D discovery identity of the discovered target UE.
[0111] Wh...
Embodiment 3
[0120] Such as Figure 4 As shown, this embodiment shows the D2D discovery process of the source UE1 discovering the target UE when the UE1 capable of D2D function and the target UE are located in the same eNB range but under different MMEs in the network sharing scenario. For simplicity, the schematic diagram only shows a scenario where there is one target UE. Wherein, the source UE1 is located under the management of the source MME1, and the target UE2 is located under the management of the target MME2. There is a special entity in the core network to manage the D2D service, that is, a D2D server (D2D Server). The D2D discovery list information of the UE is uniformly stored at the D2D server. In this process, both the source UE1 and the target UE2 use the unique D2D discovery identifier allocated by the eNB to identify their D2D devices. The specific steps of the process are described as follows:
[0121] 1)-5) are the same as steps 1-5) of Embodiment 1.
[0122]6) The ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com