Method and system for quick comparison of online wanted men through hidden video
A wanted criminal and fast technology, applied in the field of identity recognition, can solve problems such as insecurity and unfavorable promotion, and achieve the effect of long disposal time, convenient on-site operation, and personal safety.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
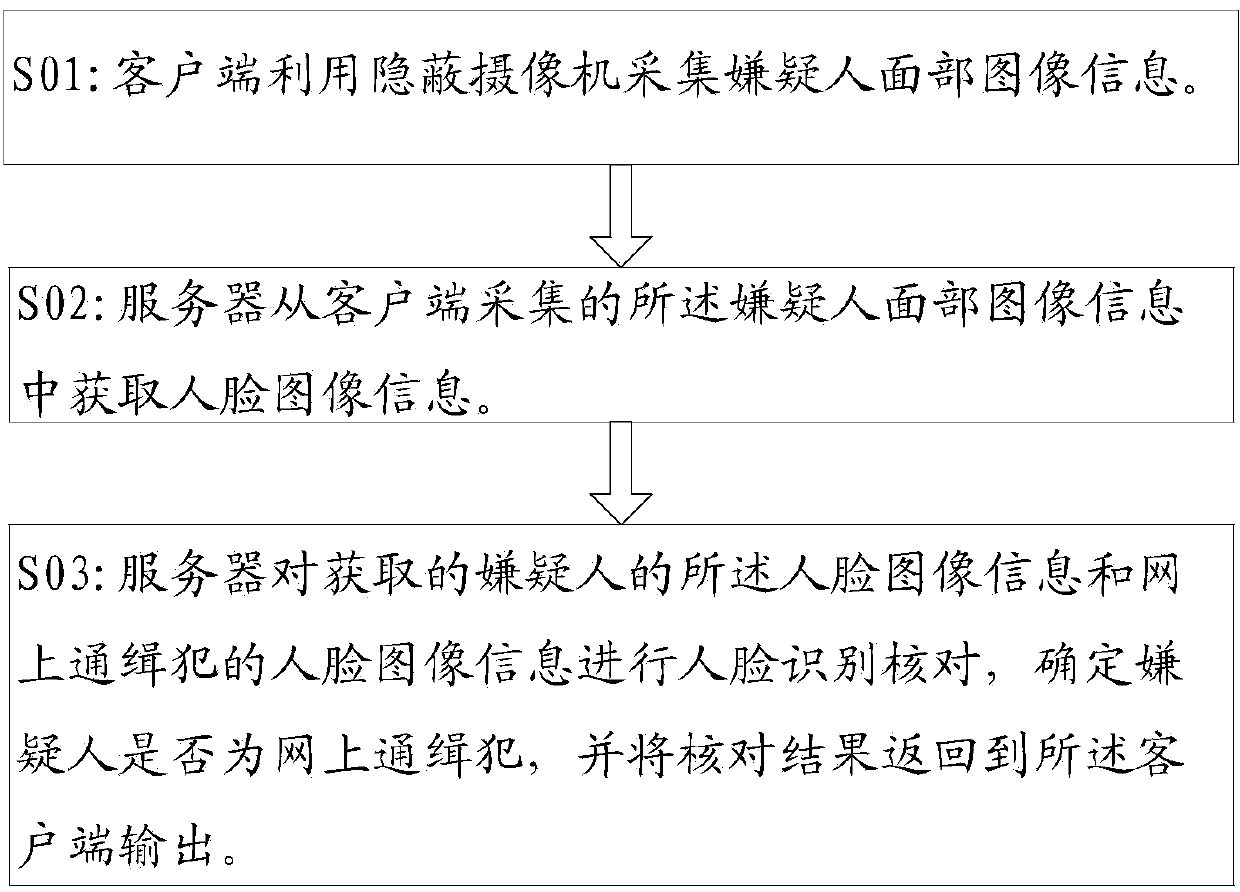
[0037] see figure 1 As shown, it is a method for quickly comparing wanted criminals on the Internet using covert video in an embodiment of the present invention, including the following steps:
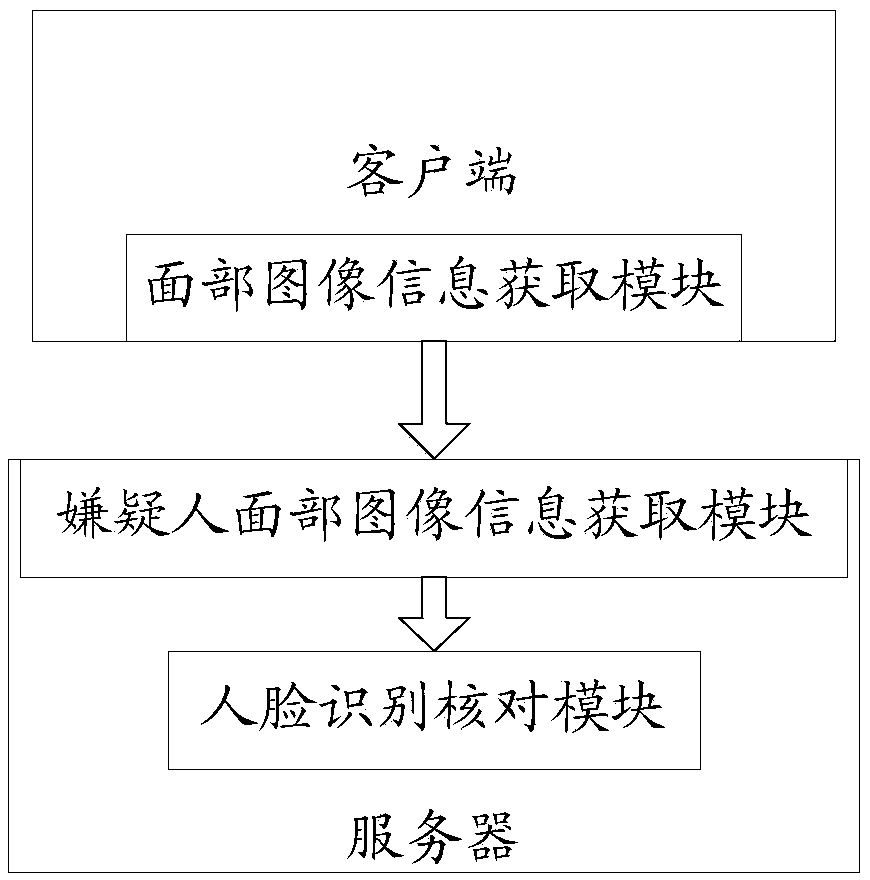
[0038] S01: The client uses a hidden camera to collect facial image information of the suspect.
[0039] S02: The server acquires face image information from the suspect's face image information collected by the client.
[0040] S03: The server performs face recognition check on the acquired suspect's facial image information and the online wanted criminal's facial image information, determines whether the suspect is an online wanted criminal, and returns the verification result to the client output .
Embodiment 2
[0042] As other embodiments of the present invention, the method for quickly comparing wanted criminals on the Internet using more concealed videos, on the basis of the above embodiments, also includes the following steps:
[0043] The client simultaneously collects the image information of the identity card of the suspect.
[0044] The server performs OCR recognition on the identity document image information collected by the client to obtain the identity document number.
[0045] The server compares the obtained ID card number with the ID card number stored in the ID card information database, determines the authenticity of the ID card, and returns information about whether the ID card is authentic to the client for output .
Embodiment 3
[0047] As a method for quickly comparing wanted criminals on the Internet using more covert video in other embodiments of the present invention, on the basis of any of the above embodiments, the client and the server communicate through wireless communication. Through the wireless communication method, no special communication line is needed, which makes the whole communication method simpler.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com