Encryption and decryption achieving method and device
A technology for encrypting and processing data to be encrypted. It is applied in the field of cryptography and can solve problems that affect the hardware implementation performance of encryption and decryption, low data throughput rate, and occupying more hardware resources.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
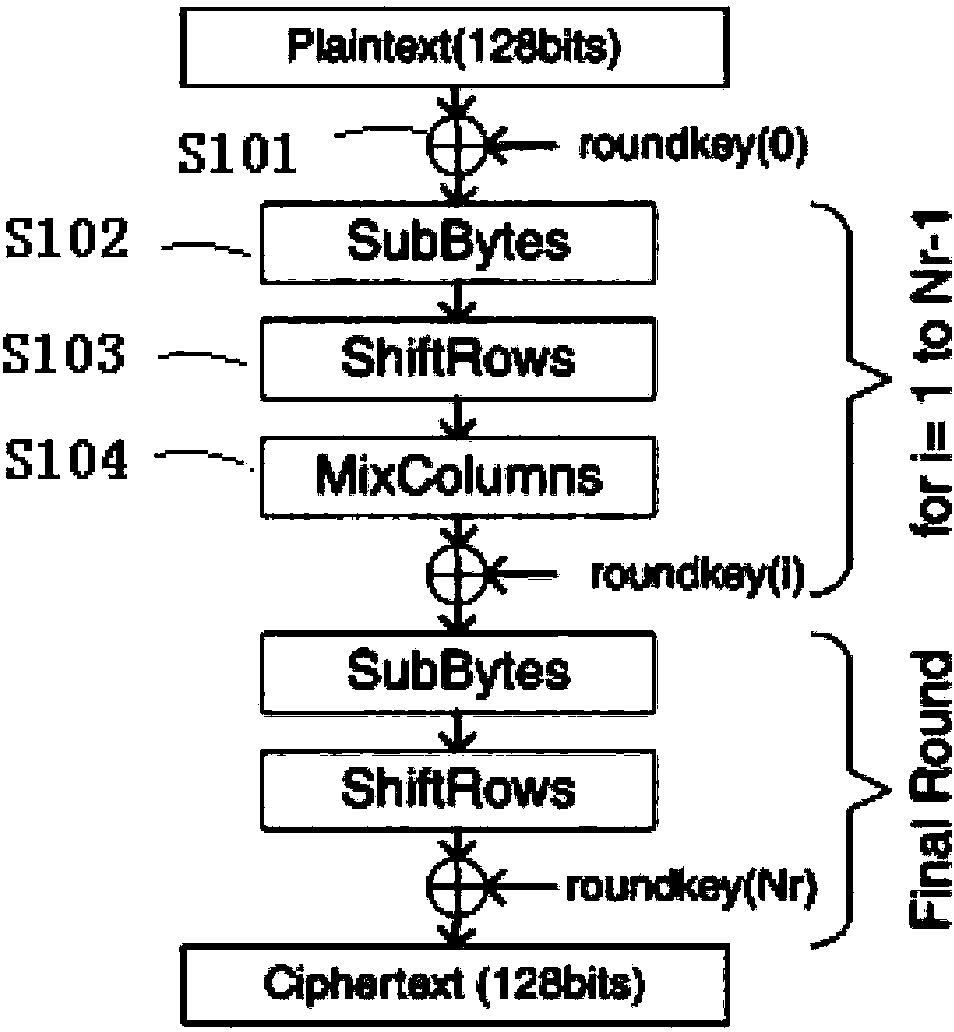
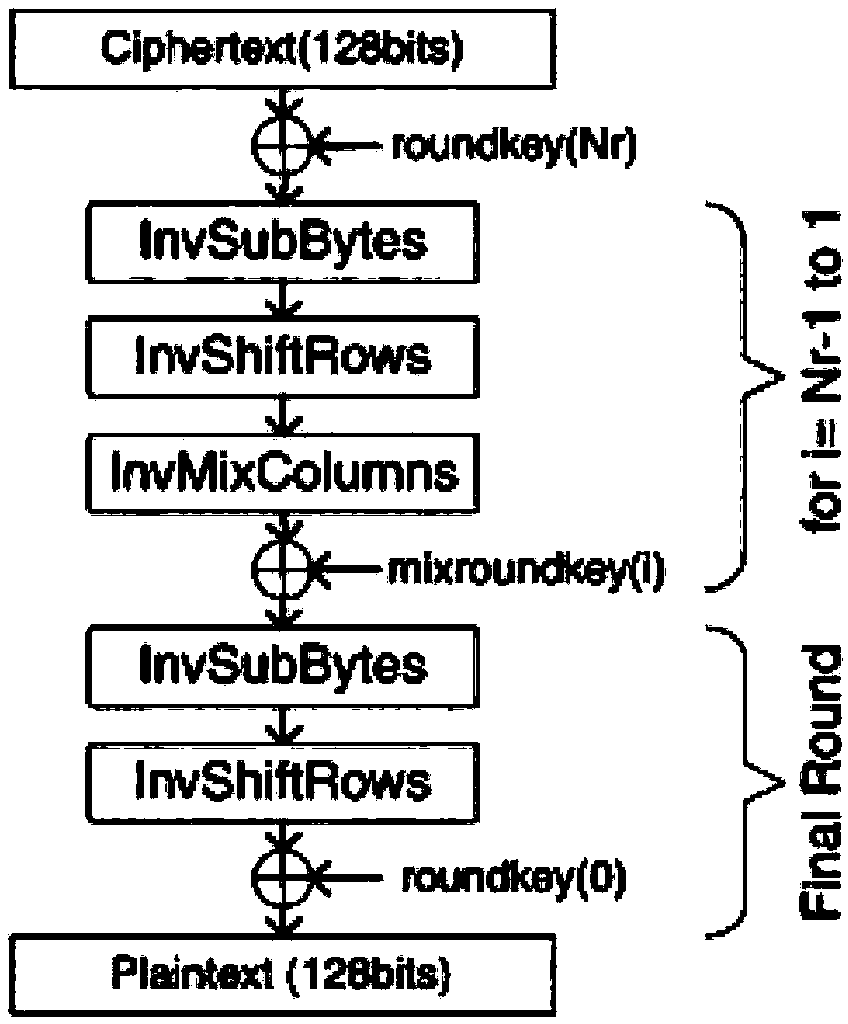
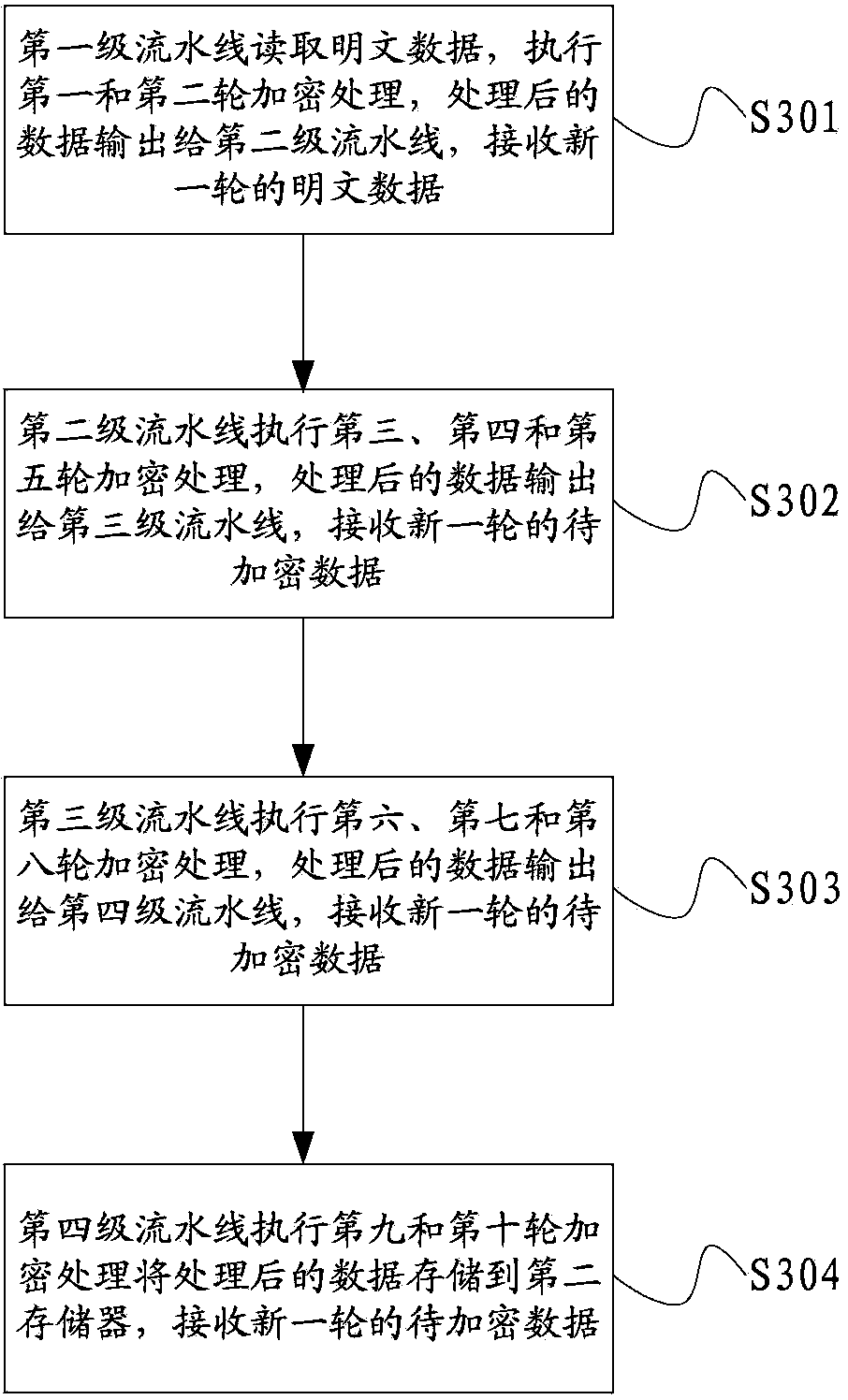
[0071] A method for implementing encryption provided by the present invention is to use a multi-stage pipeline to perform multi-stage encryption processing on the received data to be encrypted, wherein:
[0072] The current pipeline that receives the data to be encrypted, performs corresponding processing on the data including at least one round of encryption processing according to the number of stages of the current pipeline, and outputs the processed data as the data to be encrypted in the next pipeline until the end The corresponding processing of the first-level pipeline is completed; wherein, the total duration of the corresponding processing by the pipelines of each level is equal, and the sum of the total rounds of the encryption processing performed by the pipelines of each level is the total number of rounds to be executed for data encryption.
[0073] After outputting the processed data as the data to be encrypted in the next stage of the pipeline, it may further inc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com