Monitoring method based on intelligent part and intelligent part and security and protection monitoring system
An intelligent accessory and security monitoring technology, applied in the electronic field, can solve the problems such as the inability to remotely and conveniently view real-time security monitoring information and log records, the inability to provide users with personalized and customized services, and the limited information points of the security monitoring system. , to achieve the effect of improving security effect, improving security monitoring, and avoiding security loopholes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
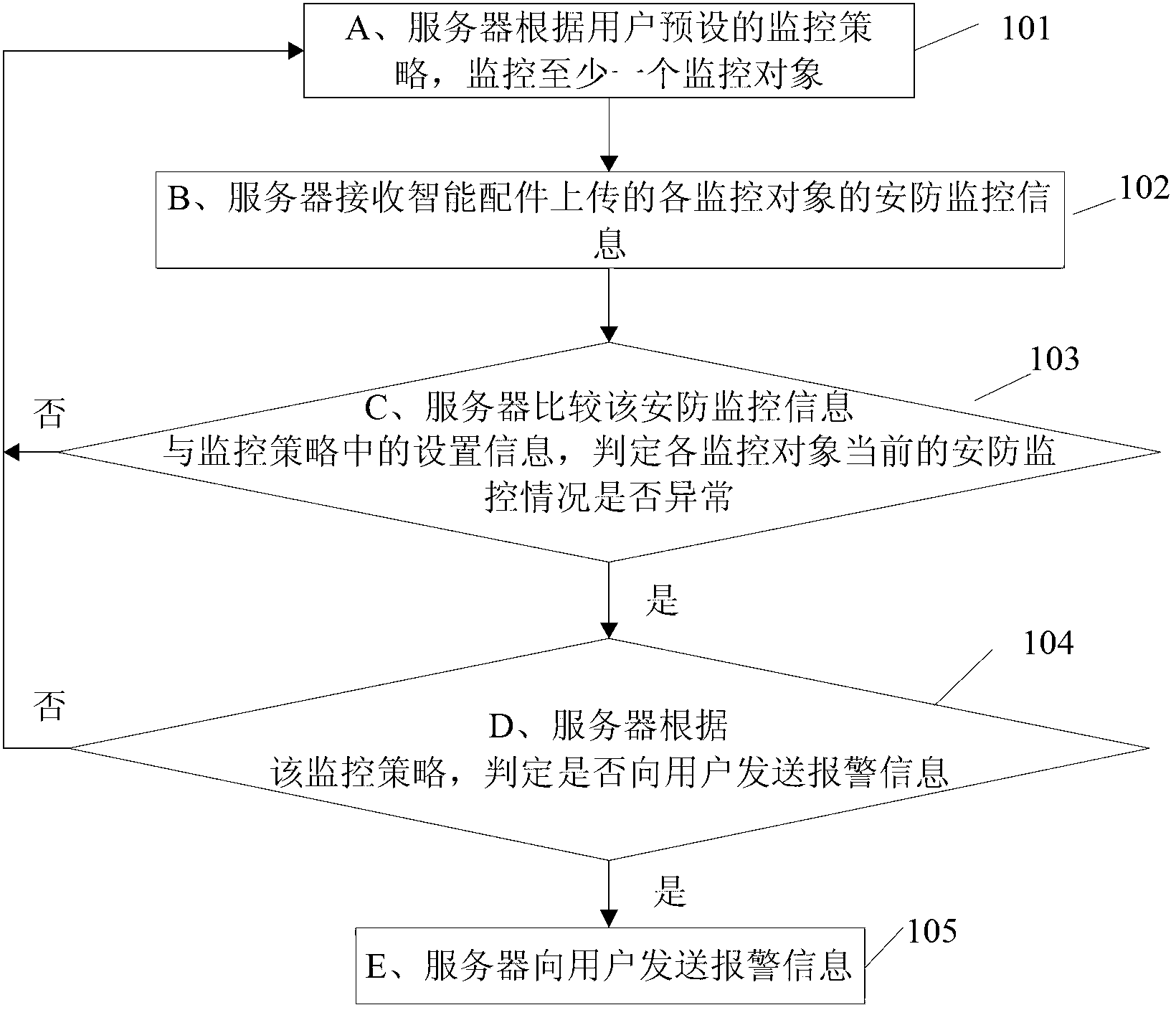
[0045] see figure 1 , this embodiment provides a monitoring method based on smart accessories, which is suitable for private residences or organizations with smart homes. The main steps and principles are as follows:
[0046] Step 101: A. The server monitors at least one monitoring object according to the monitoring policy preset by the user.
[0047] In this embodiment, the server is a security monitoring master station, which can communicate with smart meters and smart accessories through a wide area network. The monitoring objects are smart homes in the user's home, such as smart TVs, smart refrigerators, smart air conditioners, etc., or monitoring equipment such as electronic access control, video surveillance, etc., or sensors such as smoke sensors, pressure sensors, infrared sensors, etc. Each smart home can Communicate with smart accessories via LAN. Users can log in to the server through the WAN, design the architecture of the security monitoring system, customize pe...
Embodiment 2
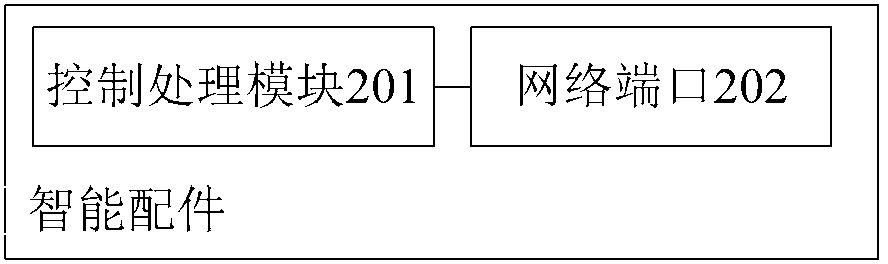
[0060] see figure 2 , this embodiment provides a smart accessory, which is suitable for security monitoring of private homes or organizations, and mainly includes: a control processing module 201 and a network port 202 .
[0061] The connection structure and working principle of each part are as follows:
[0062] The control processing module 201 is connected with the network port 202, and is used for controlling the network port 202 to receive the security monitoring information uploaded by at least one monitoring object, and for controlling the network port 202 to upload the security monitoring information to the server.
[0063] In this embodiment, the security monitoring information includes: security data of each of the monitoring objects, and power consumption information of each of the monitoring objects.
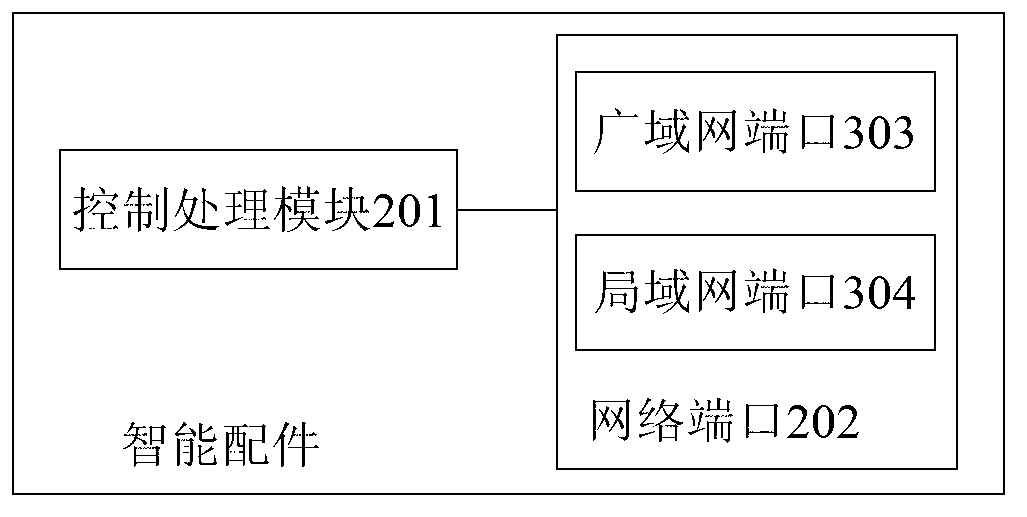
[0064] The network port 202 communicates with external servers and external monitoring objects respectively. During security monitoring, the control processing mo...
Embodiment 3
[0070] see Figure 4 , this embodiment provides a security monitoring system, which is suitable for security monitoring of private homes or organizations, including: a server 401 , a smart meter 402 , a smart accessory 403 , and at least one monitoring object 404 .
[0071] The main connection structure and working principle of each part are as follows:
[0072] The server 401 is connected to the smart meter 402 and the smart accessory 403 respectively through a wide area network communication, and is used to receive the security monitoring information of each monitoring object uploaded by the smart accessory, and compare the security monitoring information with the setting information in the monitoring strategy, and determine the current status of each monitoring object. Whether the security situation is abnormal, and when it is determined that there is an abnormality, according to the monitoring strategy and each security monitoring situation is an abnormal monitoring object...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com