Cloud Security Malicious Program Judgment System and Method
A malicious program and security technology, applied in transmission systems, electrical components, etc., can solve problems such as ineffectiveness, high network bandwidth requirements, large harm and loss, etc., to avoid access bottlenecks, ensure offline security, and improve accuracy. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
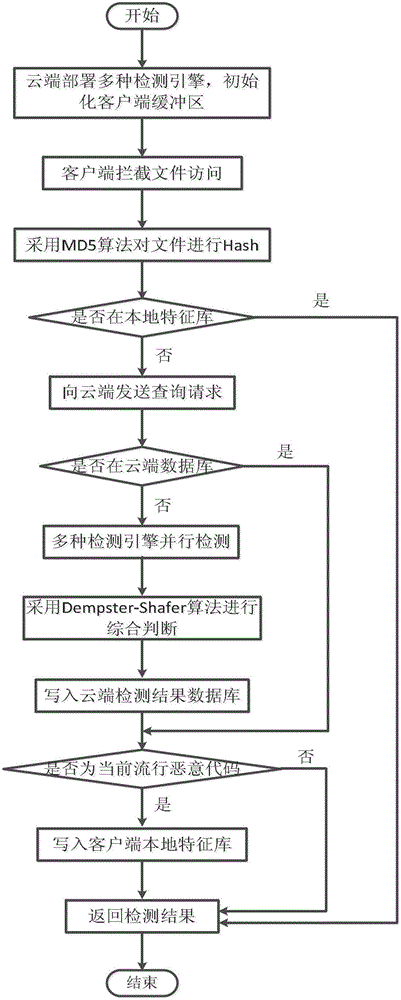
[0059] The present invention will be further described in detail below in conjunction with the accompanying drawings.
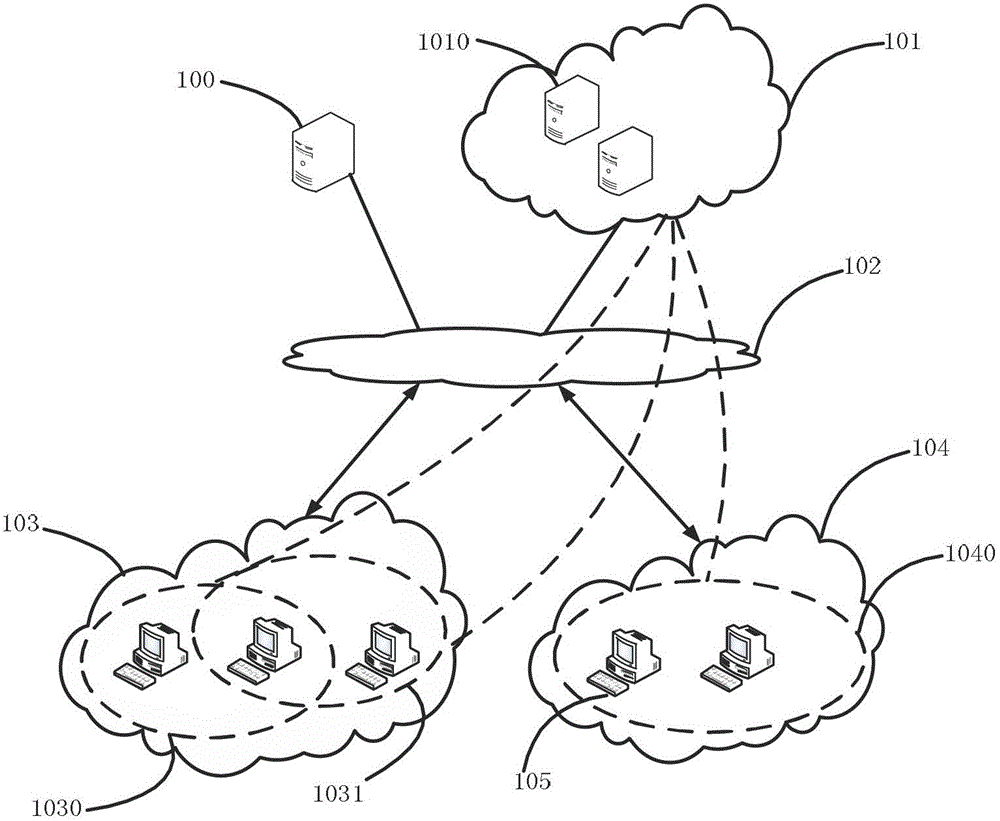
[0060] figure 1 The network topology diagram of the cloud security malicious program judgment system is illustrated. The client 105 is connected to the cloud 101 and the site 100 through the Internet 102. The site 100 is a resource library for the client 105 to browse and download information, and the cloud 101 is responsible for processing the client 105. Malicious risk requests submitted daily. The clients 105 are organized in the form of a virtual defense group 1040, and a virtual defense group 1040 is generally small-scale clients 105 that belong to the same local area network and are geographically concentrated. For example, a local area network (103) with a large scale (that is, a large number of clients) can be divided into a first virtual defense group (1030) and a second virtual defense group (1031) with an equivalent number of clients, wherein the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com