Vulnerability scanning method based on movable agent
A vulnerability scanning and mobile agent technology, applied in the field of information security, to achieve the effect of easy expansion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The technical solutions of the present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
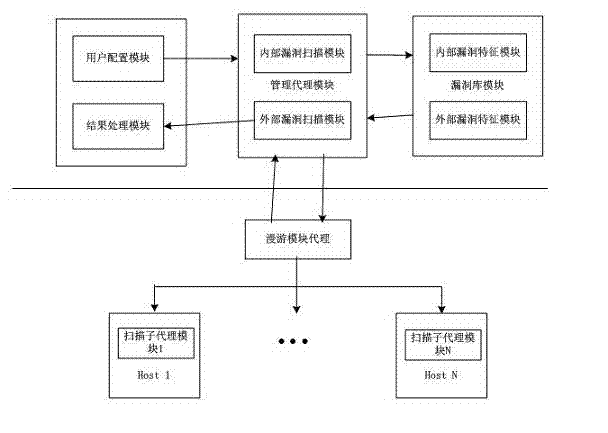
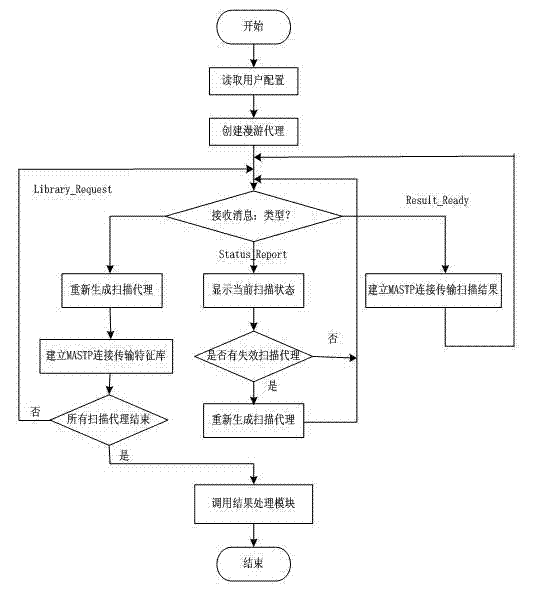
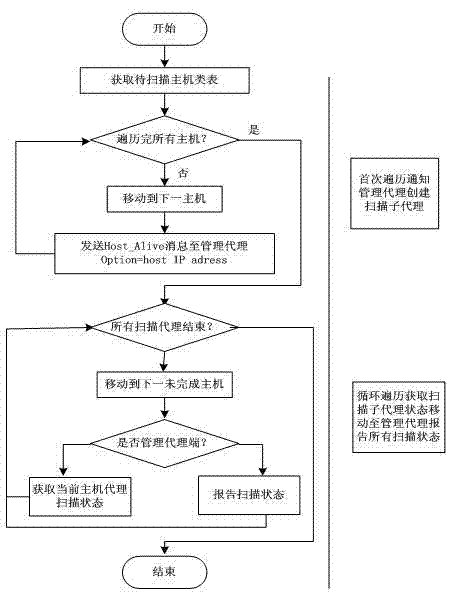
[0019] The present invention is used as an automated information system security assessment tool, such as figure 1 As shown, its entire architecture includes a user configuration module, a management agent module, a roaming agent module, a vulnerability database module and a result processing module, where the management agent module is the command and control layer in the hierarchical architecture, and the management agent module generates roam After proxying, it is sent to the network, and the roaming proxy is cyclically migrating among all scanning hosts in the network to collect the running status of each scanning sub-agent module.
[0020] The present invention adopts the Agent Tcl system of Dartmouth University as the mobile agent environment. Agent Tcl system not only provides mobile agent mechanism, but als...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com