Systems and methods for creating customized confidence bands for use in malware detection
A malicious software and confidence band technology, applied in transmission systems, electrical components, computer security devices, etc., can solve problems such as misjudgments and missed judgments, reduce misjudgments and/or missed judgments, and improve malware detection technology Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
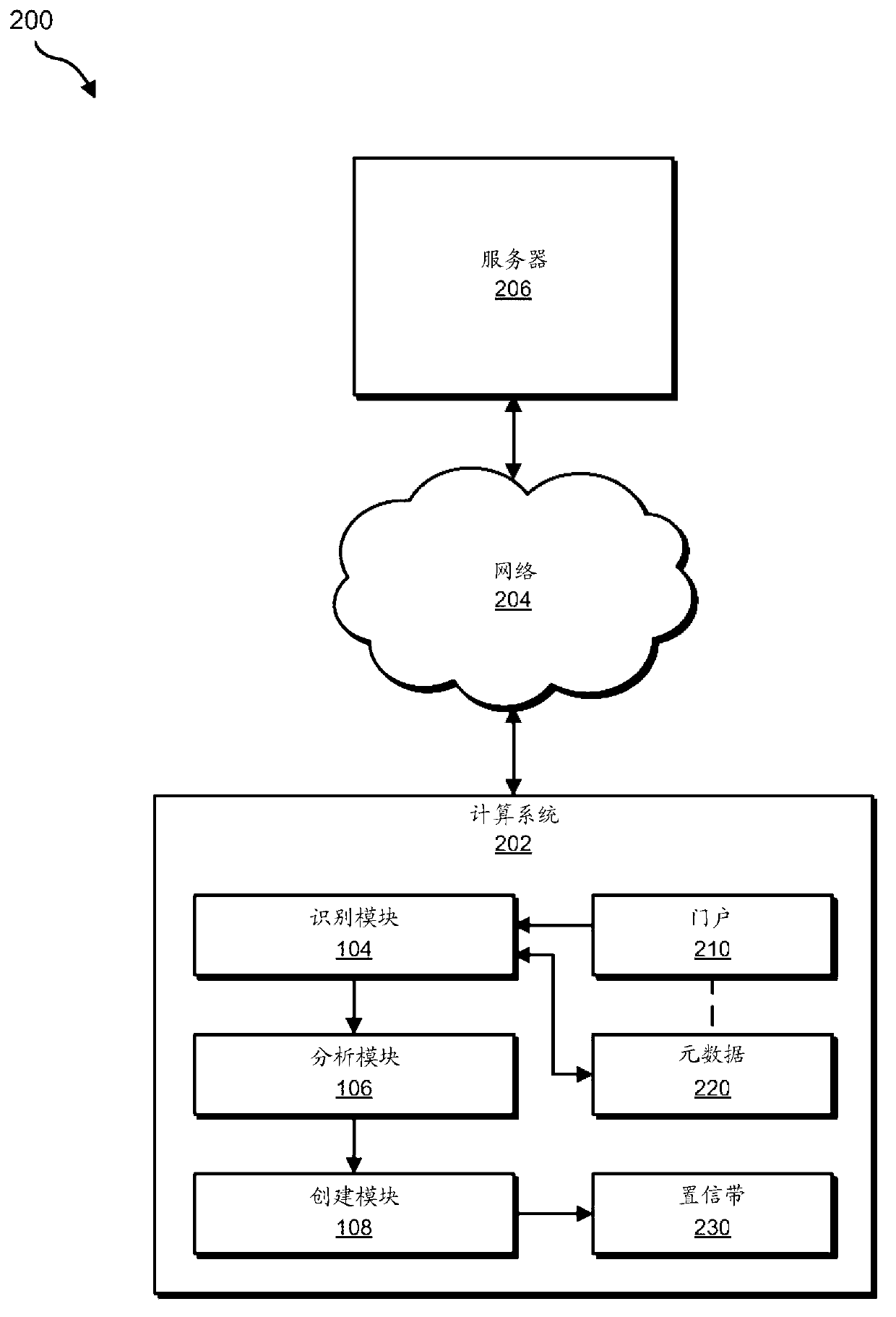
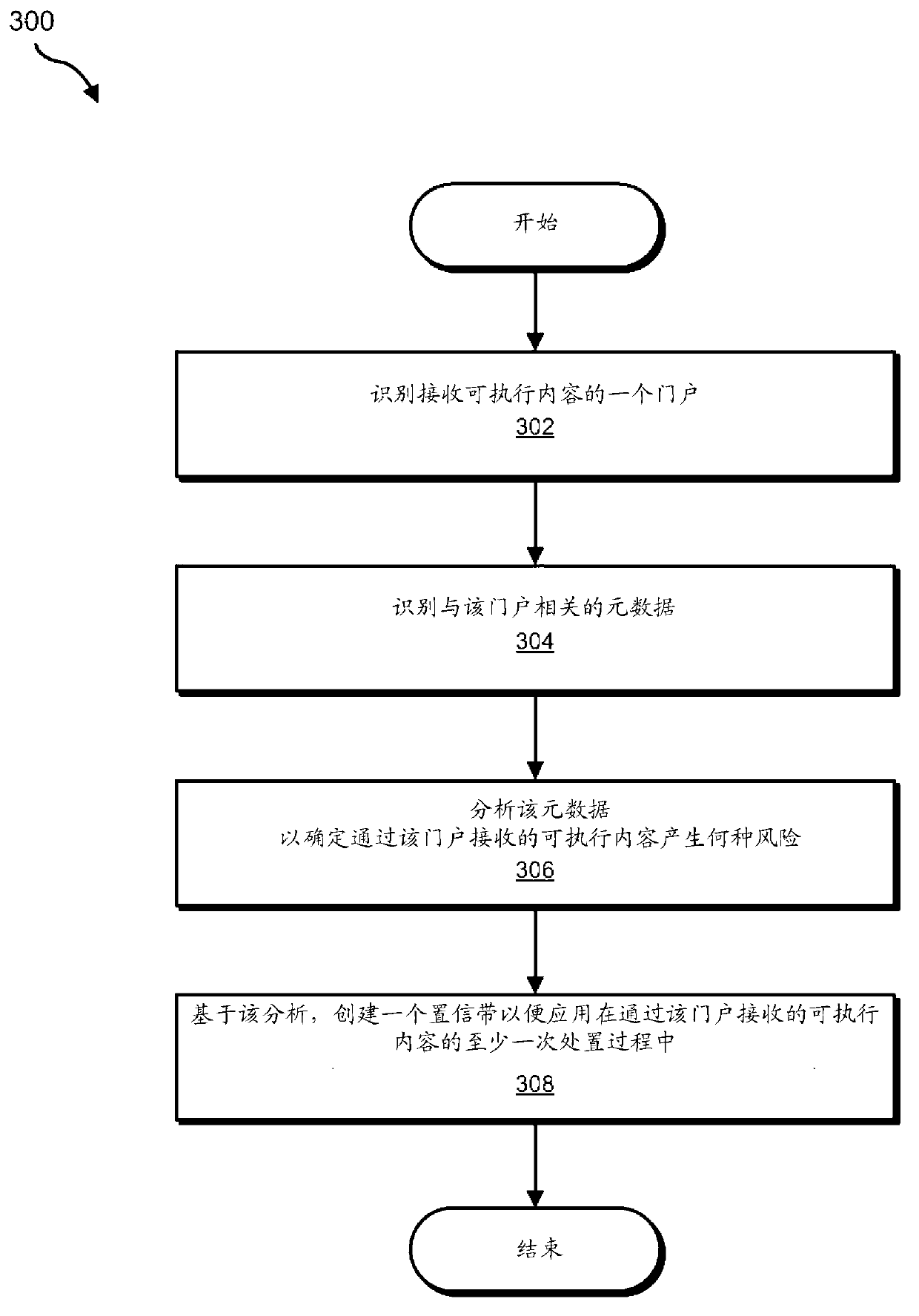
[0020] See below figure 1 , 2 and 5 detail an exemplary system for creating customized confidence bands for use in malware detection. will also combine image 3 , 4 and 6 provide a detailed description of the corresponding computer-implemented method. Additionally, will combine Figure 7 and 8 Detailed descriptions are respectively provided of an exemplary computing system and network architecture capable of implementing one or more of the embodiments described herein.
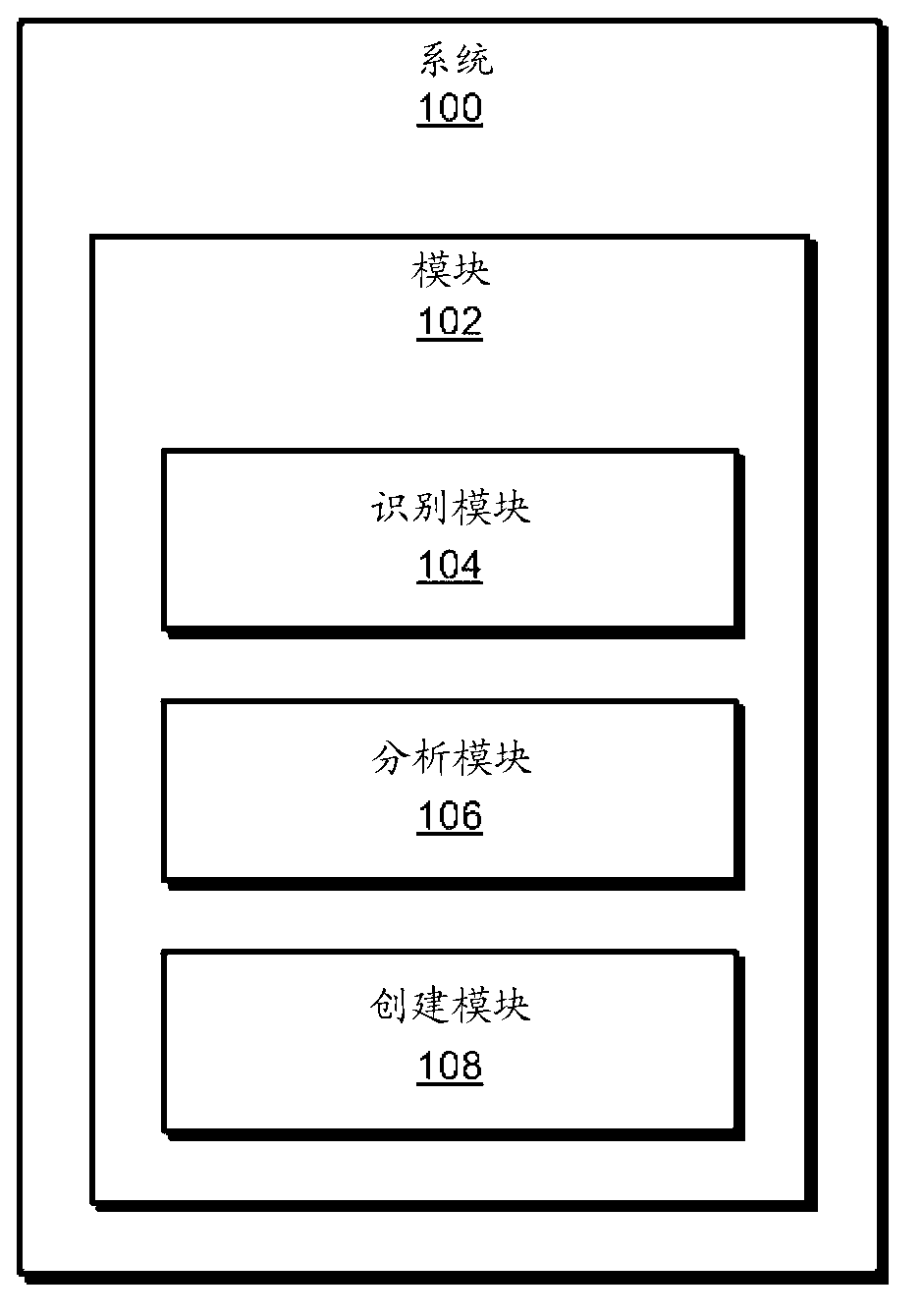
[0021] figure 1 is a block diagram of an exemplary system 100 for creating customized confidence bands for use in malware detection. As shown in this figure, exemplary system 100 may include one or more modules 102 for performing one or more tasks. For example, as will be explained in more detail below, exemplary system 100 may include an identification module 104 programmed to 1) identify a portal that receives executable content, and 2) identify metadata associated with that portal. Exemplary system...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com