Information security risk assessment method based on fault tree and system thereof
A technology for information security and risk assessment, applied in the field of information security risk assessment method and its system based on fault tree, which can solve the problems of improper use of assessment method and the accuracy of fault location affecting the progress of assessment, so as to improve stability and use The effect of long life and convenient system safety maintenance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
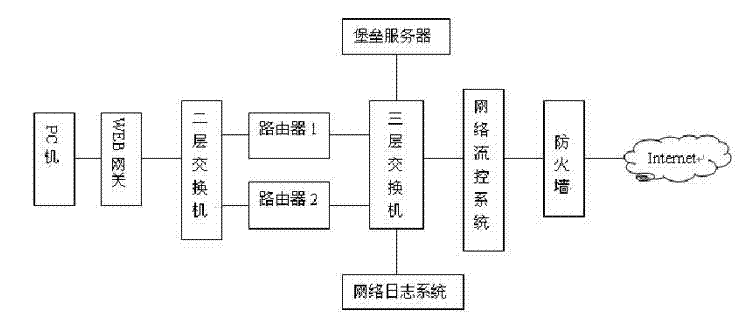
[0019] A fault tree-based information security risk assessment method, in which the fault tree analysis method is used for network equipment to realize system risk calculation, and the disjoint minimum cut set is used for risk qualitative analysis and top event probability analysis, so as to quickly identify the weakest link in the system Locate and calculate its occurrence probability, use this method to classify system security, and propose corresponding corrective measures.
[0020] In this embodiment, the risk assessment based on the fault tree is carried out. In the implementation of the risk assessment, the risk calculation model of "asset-threat-vulnerability" is selected as the core to realize the assessment. The asset (asset), denoted as A, refers to the organization's Valuable information or resources, belonging to the object of security policy protection, can be described by confidentiality, integrity, and availability; threat (threat), denoted as T, refers to the po...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com