Method for detecting and filtering application layer DDoS (Distributed Denial of Service) attack on basis of access marking
A technology of access marking and filtering method, which is applied in the direction of electrical components, transmission systems, etc., can solve the problems of low transparency of detection algorithms, servers falling into attacks, and large limitations, so as to improve the ability to resist DDoS attacks at the application layer and achieve good detection performance effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The present invention provides a method for detecting and filtering DDoS attacks at the application layer based on access marks. The method realizes transparent detection and synchronous filtering of DDoS attacks at the application layer for various servers. The technical solution of the present invention will be described in detail below in conjunction with the accompanying drawings .
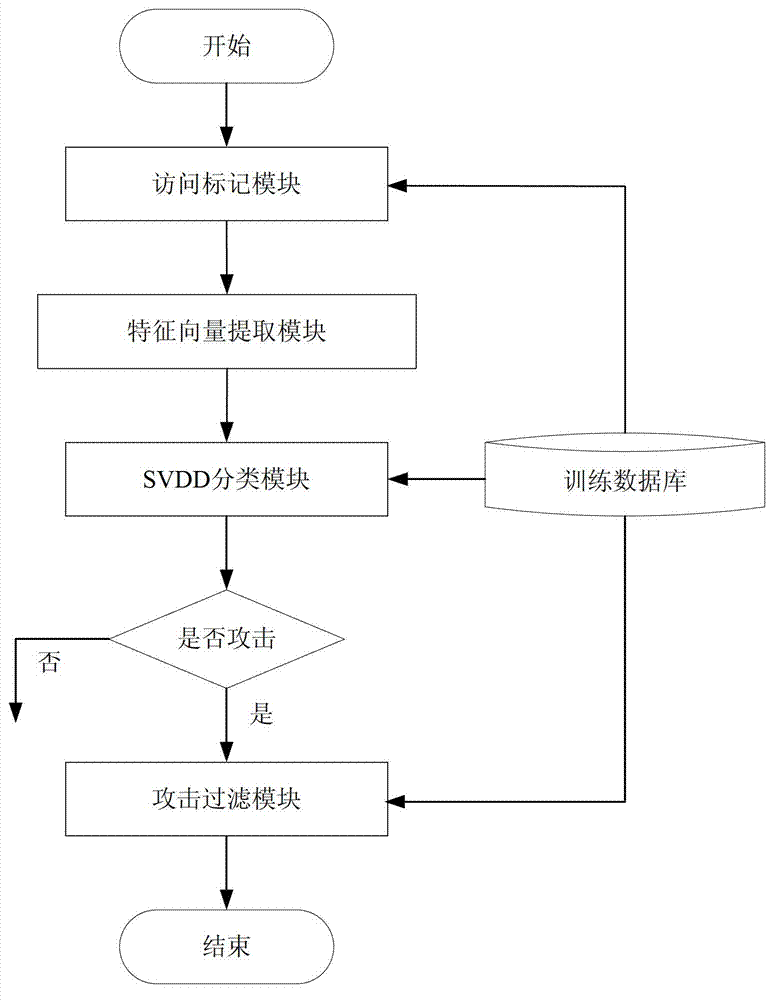
[0046] figure 1 It is a method flowchart of an embodiment of the method for detecting and filtering an application layer DDoS attack based on an access token in the present invention, as shown in the figure. The method includes the following steps:
[0047] Steps to build the training database, that is, the steps in the training phase:
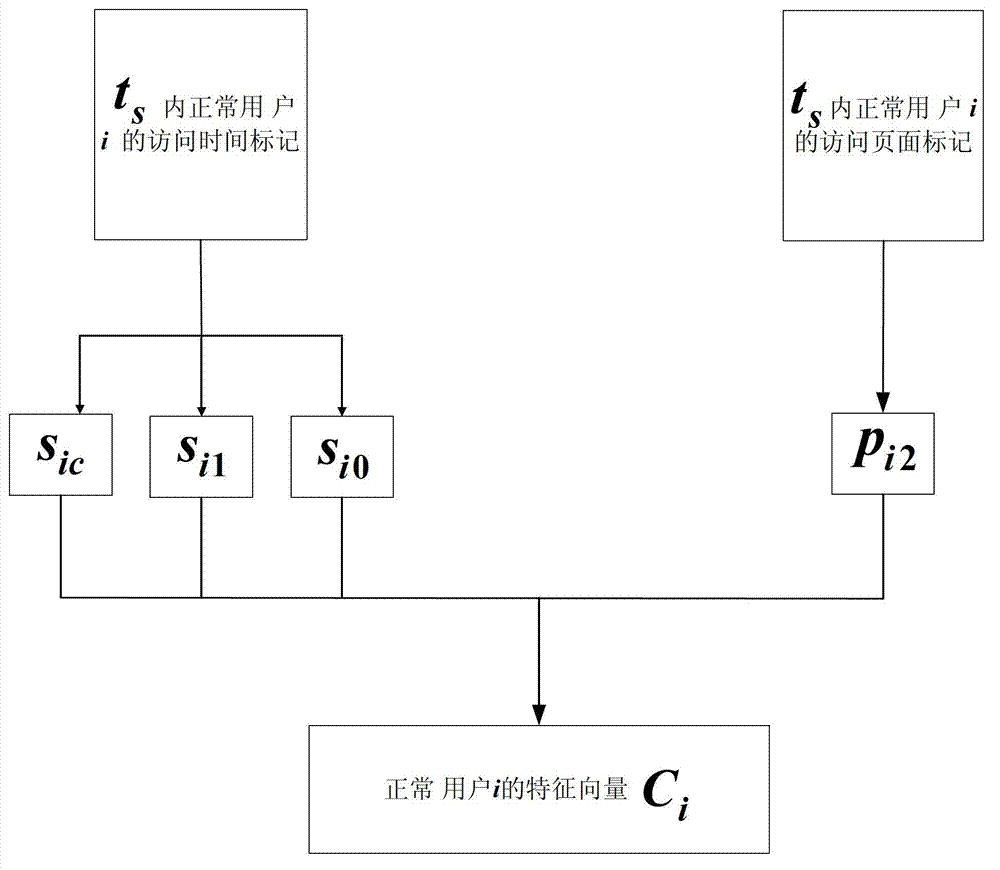
[0048] 1) Mark the normal user i's access behavior without policy, do not process the normal user i's access time and page, and obtain the original marking result;
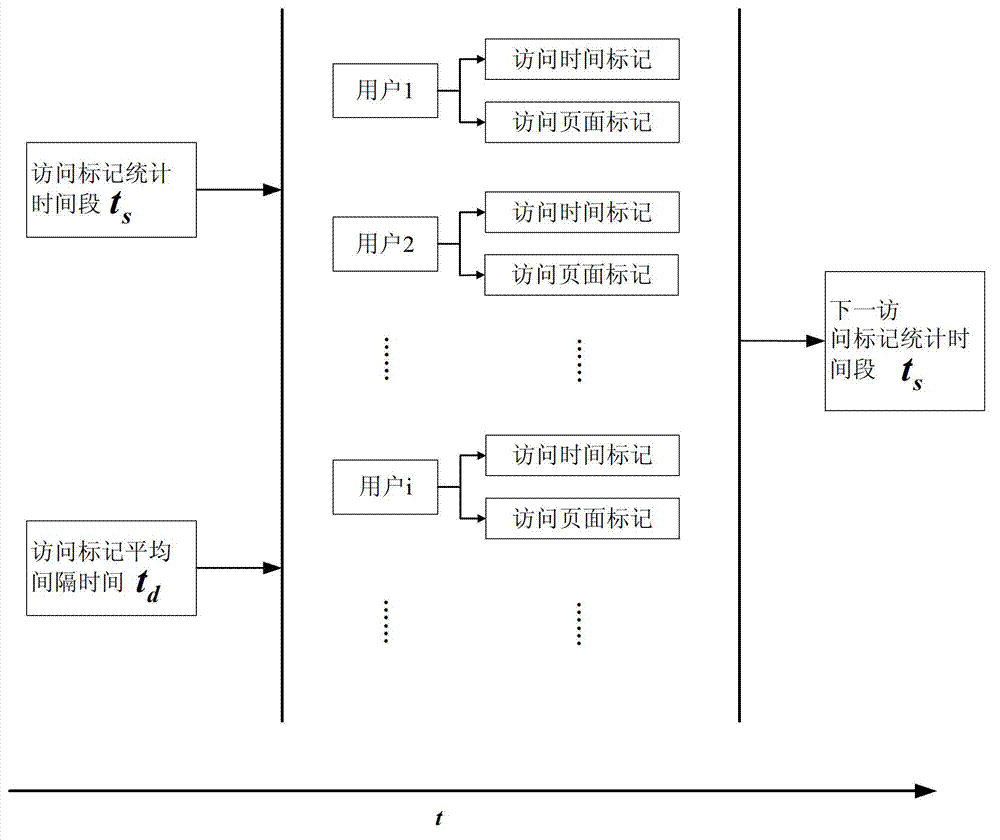
[0049] 2) Set the access mark statistics time period t s , set the average interval...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com